.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Have you ever wondered what makes your computer slow down, display strange messages, or stop working altogether? A small, unseen piece of code often causes these frustrating issues. This code is a computer virus. These programs are designed to cause damage, steal information, or take control of your system.
You need to know how these programs work to keep your system safe and ensure good computer viruses prevention. We will explain what a computer virus is, where it comes from, how it spreads, and what you can do to get the best computer viruses protection.
A computer virus can be understood as a type of malicious software, known as malware. It attaches itself to another legitimate program or document. The virus then replicates itself and spreads to other files and systems. Computer viruses depend on a host program to execute and move around.
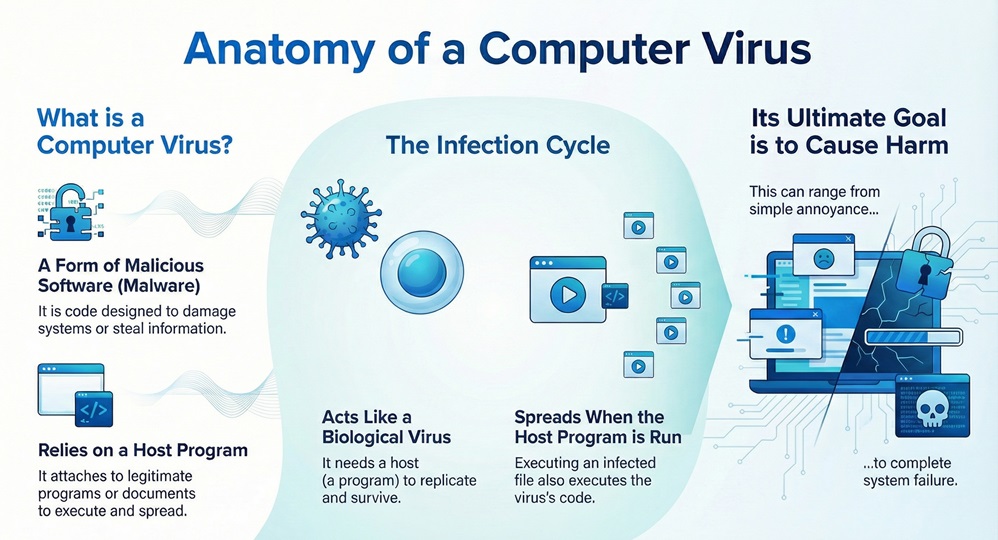
The computer virus description implies that this code acts much like a biological virus. Just as a biological virus needs a host cell to reproduce, a computer virus needs a host file or program to execute and replicate. Once the virus attaches to an executable file, the program becomes infected. When you run the infected program, the virus's code runs, too. This action allows the virus to duplicate itself and spread.
It is important to note that a computer virus aims at causing harm. This harm can range from simple annoyance to complete system failure.
Now, the question arises, who discovered computer virus as a concept? The term "computer virus" was formally coined in 1984 by computer scientist Fred Cohen. He defined a virus as "a program that can infect other programs by modifying them to include a possibly evolved copy of itself."
However, before Cohen's definition, the concept was explored. In 1971, the Creeper program (which was more of a self-replicating experiment than a malicious virus) appeared on the ARPANET. Creeper would travel from one system to another, displaying the message: "I'M THE CREEPER : CATCH ME IF YOU CAN." The program known as Reaper was then created to eliminate Creeper.
Also Read: What is Next-Gen Antivirus (NGAV)? UAE/GCC Trends & Protection
The very first PC virus in the wild, called Elk Cloner, was created in 1982 by a 15-year-old named Rich Skrenta. This program attached itself to Apple II boot sectors and spread via floppy disks. Elk Cloner was relatively harmless, displaying a short poem after the system booted for the 50th time.
The first virus to spread widely on IBM computers was the Brain virus. The computer virus Brain appeared in 1986. Two Pakistani brothers, Basit and Amjad Farooq Alvi, created the computer virus Brain. They claimed they only intended to track illegal copies of their software. However, Brain soon spread globally, marking a major turning point in malicious software.
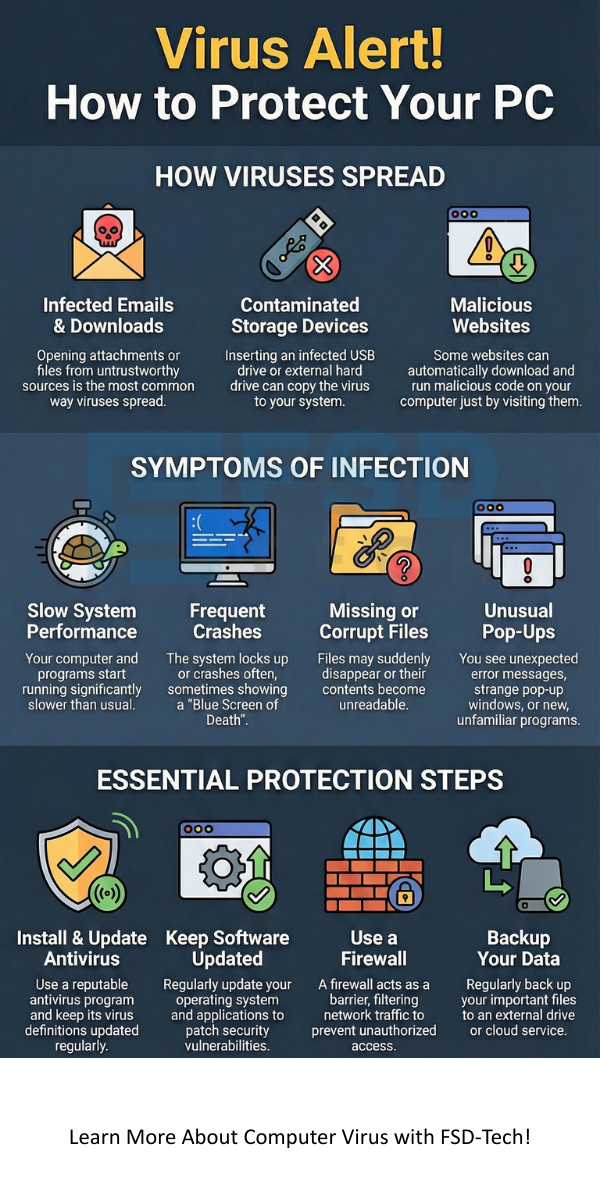
Computer viruses rely on human action to move from one system to another. They cannot start replicating on their own until a user executes the infected host file.
Let us now discuss how computer viruses spread:
Also Read: What is Web Application Firewall? | WAF Explained
Computer viruses types are numerous, but we can group them based on how they infect systems and what they aim to do. Understanding how many types of viruses are there helps you prepare for the different forms of threats.
What a computer virus do to an infected system depends entirely on its design, but the goal is always malicious. It includes slowing system performance and displaying annoying messages.
It is crucial to recognize the computer viruses symptoms in your system. Detecting these issues early allows you to take corrective action before major damage occurs.
Also Read: What Is Spyware Software? Types, Signs & Removal Guide
Effective computer viruses protection requires a layered approach, combining specialized tools with safe user habits.
To get the best computer viruses protection, you need to understand the function of antivirus software. Antivirus software is a program designed to detect, prevent, and remove malicious software, including computer viruses, from a computer system.
Antivirus software works by:
You must implement these practices for strong computer viruses prevention:
Also Read: What is a Next Generation Firewall (NGFW)? Why UAE/GCC businesses need it?
People often confuse computer viruses with other types of malicious software. While they all fall under the category of malware (malicious software), they have distinct differences.
Comparison of Malware Types
| Basis for Comparison | Computer Virus | Worm | Trojan Horse |
|---|---|---|---|
| Replication | Attaches to a host file and requires a user to execute the host. | Self-replicates and spreads independently without a host file or user action. | Does not self-replicate. |
| Spreading Mechanism | Spreads by infecting files, and via file transfer (e.g., email attachment). | Spreads over networks using vulnerabilities and exploiting network protocols. | Spreads by being disguised as legitimate software that a user willingly installs. |
| Goal/Purpose | Causes damage to files and the system. | Consumes system resources (bandwidth, memory) and can carry a payload (like a virus or backdoor). | Creates a backdoor in the system, allowing an attacker remote access and control. |
| Key Characteristic | Dependent on a host program and user action. | Independent and fully self-contained. | Deceptive and relies on social engineering. |
Your computer holds your memories, your work, and your personal data. You have the power to defend this valuable information. Do not wait for a virus to strike and delete what you value most. Take action now. Update your security software and commit to safe browsing practices. Your dedication to strong computer viruses protection ensures your data remains secure and your system runs as it should. We believe in providing you with the knowledge to make smart decisions about your security.
Proactive Virus Defense Contact our team
So, with the above discussion, we can say that a computer virus is a serious threat to the stability of your digital life. You must always maintain computer viruses protection.
The computer virus is malicious code that replicates itself and damages your system. Antivirus is security software that detects, prevents, and removes the virus from your computer.
The computer virus comes from an infected source. It could be an infected email attachment, a downloaded file from an untrustworthy website, an infected USB drive, or an infected file on a shared network.
A computer virus can steal private information, delete or corrupt your files, slow down your computer's performance, display frustrating advertisements, and sometimes take full control of your computer for malicious activities.
A virus creator, often called a malware author or hacker, is someone with programming knowledge who creates computer viruses with the intent to cause harm, make money illegally, or protest an organization. They often use high-level programming languages.
Computer viruses protection plays a vital role because it ensures the integrity of your personal and financial data. Protection maintains the speed and functionality of your system and prevents major damage that could lead to costly repairs or information loss.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts