.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

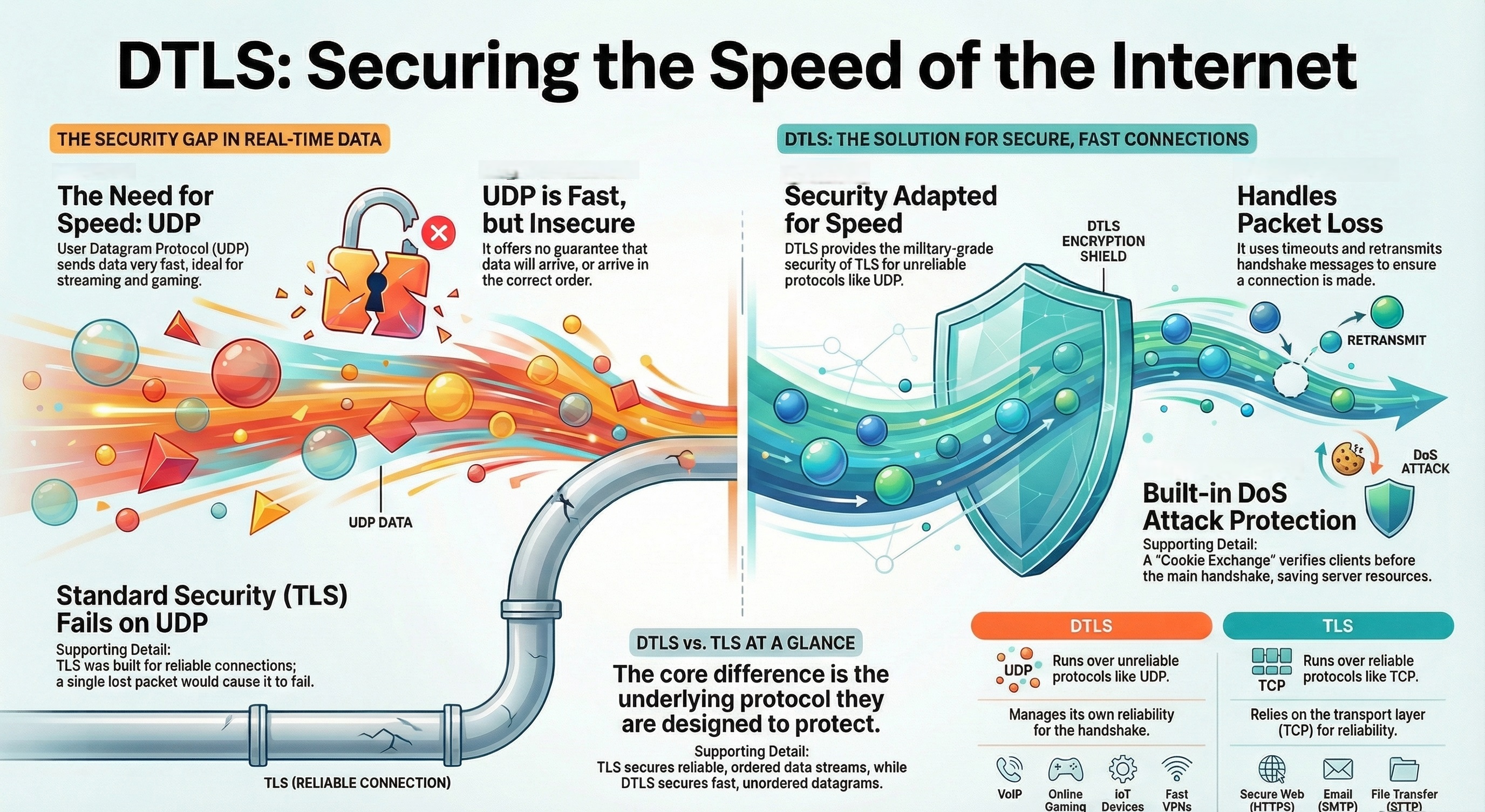
Do you love fast, real-time communication? You stream videos, you play games, and you speak over the internet without delay. Much of that speed comes from a protocol called UDP. It is quick, but it is also completely open to attack.
Transport Layer Security (TLS), the guard for our secure web, was built for a reliable connection, a calm river. It fails in the chaos of real-time data. How do we put a tough, tamper-proof lock on that fast, unreliable data bottle?
The answer is Datagram Transport Layer Security (DTLS). This brilliant protocol takes the military-grade security of TLS and adapts it perfectly for speed and messiness. DTLS is the key to securing everything from your high-stakes video call to the smallest sensor in your smart home.
How does DTLS protect your data when packets are lost in transit? What clever mechanism does it use to keep servers safe from floods of fake connection requests? Keep reading to learn how DTLS is silently making the fastest parts of the internet secure.
Datagram Transport Layer Security (DTLS) refers to a special protocol. DTLS is a version of the popular Transport Layer Security (TLS) protocol. DTLS is built to secure communication over unreliable networks.
DTLS is defined formally to provide security for datagram protocols. It works with protocols that do not guarantee that data packets arrive in order. An example of such a protocol is the User Datagram Protocol (UDP).
In simple words, DTLS takes the strong security of TLS and makes it work for applications using UDP. Think of DTLS as a secure wrapper for data packets traveling across a network where some packets might get lost or mixed up.
First of all, we need to understand the User Datagram Protocol (UDP). UDP is a core networking protocol. UDP helps send data very fast.
However, UDP is connectionless and unreliable. This means that if you send data using UDP, it offers no guarantee. It does not check if the data packets arrive at their destination. Also, it does not ensure they arrive in the correct order. This speed is great for things like video streaming, gaming, and Voice over IP (VoIP).
But, you need security for these fast applications. If you do not use DTLS, someone could listen in on your calls or see your game data. Transport Layer Security (TLS) is the standard security protocol, but it relies on a reliable transport layer, like TCP (Transmission Control Protocol).
TLS would simply fail if it ran over UDP. TLS expects data to be delivered in order and without loss. A single lost packet would make the whole secure connection shut down.
DTLS solves this problem. DTLS introduces security features that work with the unreliability of UDP. The design of DTLS is based on the proven security models of TLS.
This way, DTLS lets applications get the speed of UDP but also the high-grade security they need. The creation of DTLS was necessary to secure the next generation of real-time network applications.
Also Read: Avoiding Compliance Penalties with Cato SASE: Meeting Regulatory Standards Effortlessly
The core job of DTLS is to prevent three main security threats. DTLS stops eavesdropping, tampering, and message forgery. It achieves this by using cryptography.
DTLS handles these challenges by changing how the secure connection is set up. DTLS makes changes to the TLS Handshake and the record layer.
DTLS Handshake Process
The DTLS Handshake is a complex process. It is how two parties agree on secret keys and check each other's identities. Because DTLS runs over UDP, the handshake has to deal with packet loss.
DTLS addresses packet loss by adding a timeout and retransmission mechanism. This is similar to how UDP applications often handle their own reliability.
DTLS Handshake begins with the ClientHello message. The client sends this to the server.
The ClientHello message contains important details. It tells the server what encryption methods the client supports.
If the server does not get a message, it waits for a short time. After the time runs out, the server will assume the packet is lost. Then, the client will retransmit the original message. This is a key difference from TLS.
Another important step is to prevent denial-of-service (DoS) attacks. DTLS uses a Cookie Exchange method before the main handshake.
DTLS Cookie Exchange works like this. The client sends a message, and the server sends back a cookie. The client must include this cookie in its next message. This confirms that the client is at the address it claims to be. This protects the server from wasting resources on fake connections.
Finally, the parties exchange keys. After the keys are exchanged, they begin to send encrypted DTLS Records.
DTLS Record Protocol
The DTLS Record Protocol is what carries the actual application data. Each DTLS record is sent as a single UDP datagram.
A major feature of the DTLS Record Protocol is the explicit sequence number. Every message in the DTLS handshake and every data record has a sequence number.
This sequence number allows the receiving party to detect two things. First, it detects if a packet is lost. Second, it detects if packets arrive out of order.
The receiver can throw away old, duplicate, or out-of-order records. This ensures that the security functions (like checking for tampering) are applied correctly.
Also Read: Reducing Network Latency and Enhancing User Experience Globally with Cato SASE
Datagram Transport Layer Security (DTLS) has specific features to adapt security to unreliable transport.
DTLS and TLS share most of their security logic. They both use the same cryptographic algorithms and key exchange methods. However, DTLS has to overcome the inherent differences of its transport layer, UDP.
The main difference comes down to reliability and message ordering.
TLS is built on TCP. TCP guarantees that data arrives in the correct order. It also retransmits lost packets automatically.
DTLS is built on UDP. UDP gives no guarantees. Therefore, DTLS has to build its own methods for reliability and ordering.
DTLS adds two fields to its records that TLS does not need. The first is a sequence number. The second is a handshake message sequence number.
The use of timeouts and retransmissions in the DTLS handshake is another key difference. This makes the DTLS handshake more robust against loss than its TLS counterpart.
| Basis for Comparison | Datagram Transport Layer Security (DTLS) | Transport Layer Security (TLS) |
|---|---|---|
| Underlying Protocol | Primarily runs over User Datagram Protocol (UDP). UDP is connectionless and unreliable. | Primarily runs over Transmission Control Protocol (TCP). TCP is connection-oriented and reliable. |
| Reliability & Ordering | Does not rely on the transport layer for ordered, reliable delivery. It must handle message loss and reordering itself. | Relies completely on TCP to guarantee that data packets arrive correctly, in order, and without duplicates. |
| Handshake Mechanism | The DTLS handshake includes its own timeout and retransmission logic to recover from lost handshake messages. | The TLS handshake assumes reliability; any message loss is handled by the underlying TCP retransmission. |
| Record Header Fields | Includes an explicit sequence number and a retransmission window field in the record header. This is essential for detecting message loss and reordering. | Does not need explicit sequencing fields, as TCP provides reliable sequencing below the TLS layer. |
| Denial-of-Service (DoS) Mitigation | Incorporates a Cookie Exchange mechanism in the initial handshake. This prevents attackers from easily initiating many fake handshakes that consume server resources. | Does not include an internal cookie exchange because the underlying TCP handshake (SYN-ACK) provides a basic level of source validation. |
| Tolerance to Loss | High tolerance. The loss of a data record does not break the connection; the receiver simply discards the lost packet and processes the next one. | Low tolerance. The loss of a single TCP segment is handled by retransmission, but the TLS layer waits for the correct sequence. If retransmission fails, the TCP connection may terminate, which affects the TLS session. |
| Performance Advantage | Low latency. Ideal for real-time applications where speed is more important than absolute guarantee of every single packet. | Consistent performance. Ideal for bulk data transfer where accuracy and integrity are paramount. |
| Primary Use Cases | VoIP (Voice over IP), Gaming, IoT (Internet of Things) devices using CoAP, and fast VPN solutions. | HTTPS (secure web browsing), SMTP (secure email), SFTP (secure file transfer), and most reliable network streaming. |
Also Read: Unified Device Visibility: Enhancements to Cato’s Device Inventory
DTLS has proven very useful for securing communication in environments where high speed and low overhead are critical.
CoAP and DTLS
One of the most important applications of DTLS is in the world of the Internet of Things (IoT). Many small IoT devices use the Constrained Application Protocol (CoAP).
CoAP is similar to the web's HTTP, but much simpler. CoAP runs over UDP. DTLS provides the security layer for CoAP. This is often called DTLS for CoAP.
DTLS for CoAP is a critical part of securing sensor networks. These networks have devices with very low power and memory. DTLS provides the necessary encryption without adding too much complexity to these small devices.
DTLS in VoIP and Streaming
Voice over IP (VoIP) uses UDP for fast, real-time voice delivery. DTLS secures the control plane for many VoIP systems. It ensures that the key exchange for the voice stream itself is secure.
DTLS helps prevent attackers from listening to your private calls. Furthermore, many secure streaming protocols use DTLS to protect their fast video and audio streams.
DTLS in VPNs
Some Virtual Private Network (VPN) solutions use DTLS as their protocol. DTLS VPNs are often faster than those using TCP-based protocols. The reason is simple: there is less overhead from the protocol trying to guarantee delivery. The result is a quicker and more responsive connection for the user.
Like any technology, Datagram Transport Layer Security (DTLS) has both pros and cons. We need to look at both sides to understand where it best fits.
Advantages of DTLS
Disadvantages of DTLS
Conclusion
Datagram Transport Layer Security (DTLS) is a vital protocol. DTLS brings the necessary security of TLS to the world of unreliable, fast-moving datagrams. The work that went into adapting TLS for UDP shows a great focus on protecting the next generation of applications.
This protocol ensures that real-time applications—from your quick game to your secure video call—can be fast and safe.
If you are building an application that needs the speed of UDP but the security of a modern protocol, DTLS is the solution you need. Do you need help implementing a robust DTLS solution for your unique network challenge? Contact our technical team today to start securing your high-speed communications.

The fundamental purpose of Datagram Transport Layer Security (DTLS) is to bring the strong security features of TLS (encryption, authentication, integrity) to applications that use unreliable transport protocols like UDP (User Datagram Protocol). Essentially, it secures high-speed, loss-tolerant communications.
Standard TLS relies on the underlying transport protocol to guarantee reliability and ordered delivery. UDP does not provide these guarantees. If a single packet is lost while using TLS over UDP, the secure session would likely halt or fail, as TLS doesn't have its own built-in mechanism to handle packet loss or reordering.
DTLS addresses packet loss during the setup phase by using its own internal timeout and retransmission mechanism. If a handshake message is sent but no response is received within a certain time, DTLS will automatically resend the message, ensuring the secure session can still be established.
DTLS prevents message replay attacks by including an explicit sequence number in the header of every DTLS record. The receiver keeps track of the sequence numbers it has already seen. Any message arriving with an old or duplicate sequence number is immediately discarded, protecting the session integrity.
The Cookie Exchange is an initial step in the DTLS handshake designed to prevent Denial-of-Service (DoS) attacks. The server sends a small, encoded message (the cookie) to the client. The client must echo this cookie back to prove that it is actually located at the claimed IP address before the expensive cryptographic handshake begins.
DTLS is commonly used in applications that prioritize low latency and speed. This includes:
No, DTLS itself does not guarantee data delivery. It runs on top of UDP, which is inherently unreliable. DTLS only ensures the packets that do arrive are authenticated, encrypted, and checked for integrity. It secures the data, but it does not fix the transport layer's unreliability.
DTLS inherits all the core security features from TLS. This includes:
DTLS adds some overhead to plain UDP primarily due to the security features. This overhead includes:
Yes, many modern applications, especially in areas like VoIP and VPNs, use both protocols. They might use TLS for reliable signaling or control channels (over TCP) and then switch to DTLS to secure the high-speed, real-time data or media stream (over UDP).

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts