
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Are you aware that some spyware software might be quietly sitting on your computer or phone? This type of malicious software is a big threat to your privacy and safety online. Many people use the internet every day for banking, shopping, and talking with friends. Because of this, learning about spyware software and how it works has become very important.
In this guide, you will get to know about this digital danger. We will explain what spyware software is, how it gets onto your devices, and why you should care about it. We will also talk about the different kinds of spyware and, most importantly, show you simple ways to remove and prevent it. We are going to provide practical steps. Always remember that protecting your digital life is an ongoing task.
Now, the question arises: Why is understanding spyware software a must for you? Because this malicious code secretly records what you do. It can steal your passwords, credit card numbers, and other personal data. You should take a read of this complete guide to keep your information safe and secure.
Spyware software refers to a type of malicious software, or malware, that secretly installs itself on a computer or mobile device. As the name suggests, this spyware's primary purpose is to spy on you. It collects personal data and information about your activities without your knowledge or consent.
It is to be noted that spyware software typically runs in the background. It does not openly show itself. This makes it very hard for the average user to find. Spyware can be understood as a digital thief who silently enters your home (your device) and takes your valuable information (your personal data).
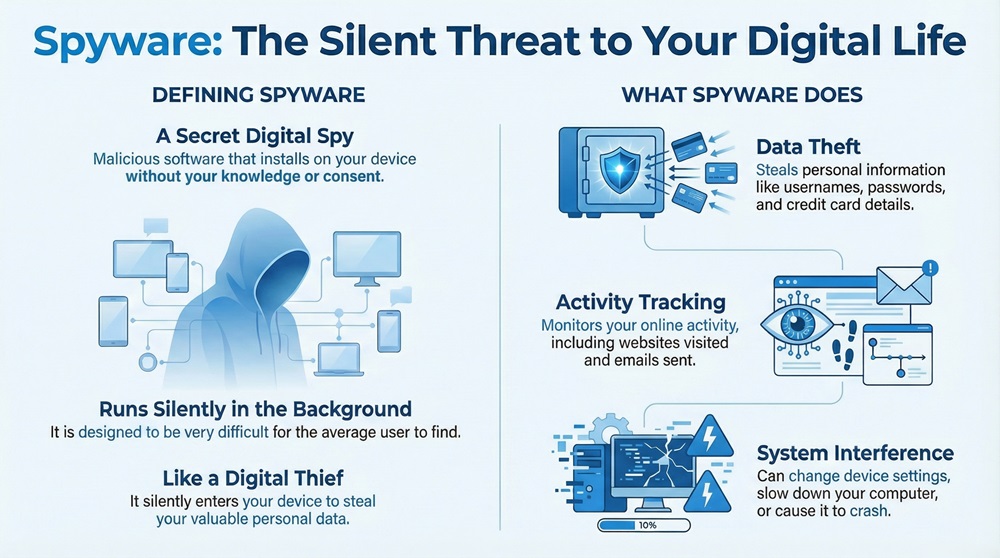
To understand spyware software in clearer terms, here are its key functional purposes:
Spyware often comes bundled with other seemingly harmless software. It is a major threat to your digital security and data protection.
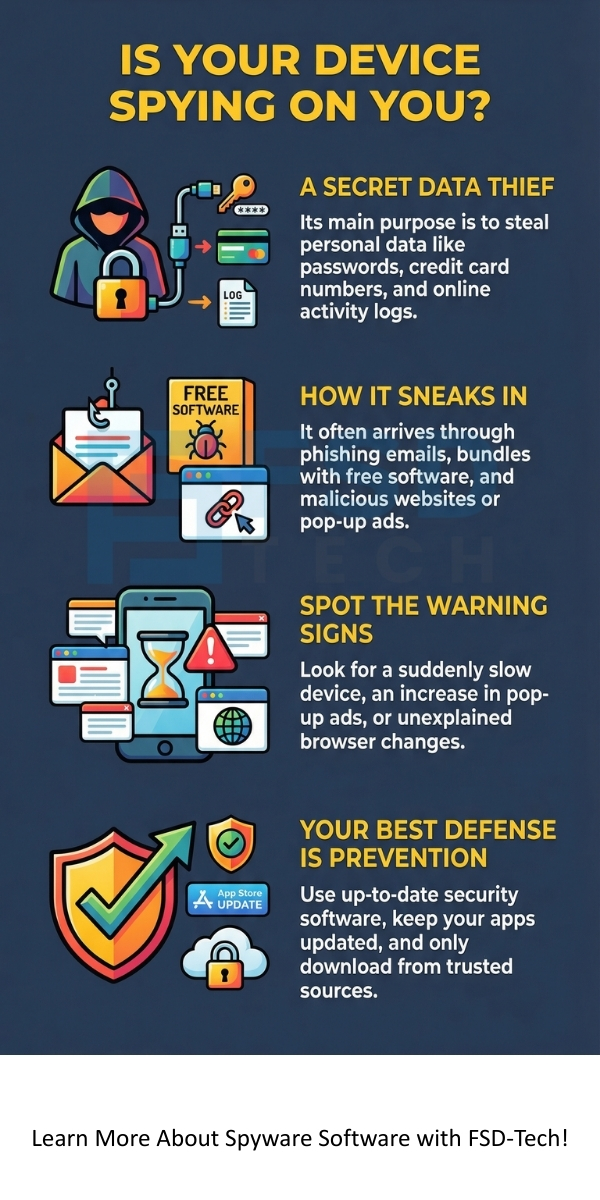
Spyware software is good at hiding. It uses several clever ways to sneak onto your computer or smartphone. If you want to stop spyware, you must first know how it gets in.
Here are the most common ways spyware sneaks onto your device:
Always remember that spyware installation happens when you are not careful. Being cautious about what you download and click is your first line of defense against spyware.
Also Read: Spear Phishing: Learn About #1 CEO fraud
Not all spyware software is the same. Basically, several categories of spyware exist, each focusing on stealing a different kind of personal data. Knowing these types helps you understand the specific risks involved in spyware detection and removal.
There are various types of spyware worth understanding:
Each type of spyware needs a specific approach for spyware detection and removal. This makes using strong, multi-layered anti-spyware software necessary.
Sometimes, spyware software works so well that you don't even know it's there. However, most spyware leaves certain clues that you should watch out for. Learning these signs will help you in spyware detection before too much damage is done.
Here are the key signs your computer or phone might have spyware software:
If you notice several of these signs, you should immediately perform a full scan with a reliable anti-spyware software.
Also Read: What is Web Application Firewall? | WAF Explained
Removing spyware software requires a careful, step-by-step process. Do not try to remove it manually unless you are an expert, as you could damage your system. Spyware detection and removal is best done using specialized anti-spyware software.
Here is a step-by-step process for removing spyware software:
1. Disconnect from the Internet
Initially, you must disconnect your computer or phone from the internet. This stops the spyware from sending your collected personal data to the attacker. This is the first and most important step in spyware removal.
2. Enter Safe Mode (For Computers)
Next, restart your computer and enter Safe Mode. When you are in Safe Mode, only the minimum necessary programs load. This prevents most spyware software from running. This makes it easier for your anti-spyware tool to find and remove the malware.
3. Run a Full Scan with Anti-Spyware Software
Here, you need to use a strong, updated, and reputable anti-spyware software.
4. Clear Temporary Files and Browser Data
Spyware often leaves behind temporary files and browser history. So, you must clear your temporary files, cache, and cookies. This gets rid of any leftover traces of the spyware software.
5. Change All Your Passwords
Since keyloggers or password stealers might have taken your logins, you must change all your important passwords right away. Only do this after you have cleaned your system completely, as changing them beforehand means the spyware could simply steal the new ones too.
Anti-spyware software is your primary tool in this fight. Always use a tool with a high reputation for malware detection and removal.
Also Read: Cloud Encryption Gateway (CEG): Keep Keys, Secure Data
The best defense against spyware software is to stop it from getting on your device in the first place. You can keep your system safe by adopting good digital security habits and using the right tools.
To effectively prevent spyware installation, follow these key practices:
Preventing spyware is much easier and safer than having to do spyware removal. By being smart and using the right tools, you can greatly reduce the risk.
So, you now understand the serious risks that spyware software brings to your digital security and personal data. We have talked about how this malware works, its different types, and the simple steps for spyware detection and removal. Spyware is a silent and serious threat. Using strong anti-spyware software and practicing safe habits are the two most important steps to keep your information private.
When you need robust digital security solutions, remember that protecting your data is our highest priority. When the situation requires advanced malware detection and removal, choosing a partner with a deep commitment to data protection is the recommended choice. We focus on providing complete security, so you can live your digital life with confidence.
Worried About Hidden Spyware? Reach out now
This section addresses common questions about spyware software to provide a clearer understanding of digital privacy and security.
A virus is a type of malware that replicates itself and spreads by infecting other files. On the other hand, spyware software focuses on monitoring your activity and stealing your personal data without self-replicating. While both are harmful, the virus's main goal is to damage files, whereas the spyware's main goal is to steal information.
Yes, spyware software can still track your activity in an incognito or private browsing window. Incognito mode only stops your browser from saving your local history, cookies, and site data. However, keyloggers and other spyware operate at the operating system level, capturing your keystrokes and screen activity regardless of your browser settings. It is to be noted that spyware detection and removal is the only way to truly stop the tracking.
Absolutely. Mobile spyware is a growing problem, especially on smartphones running the Android operating system, though iPhones are also vulnerable. This kind of spyware software can track your location, read your text messages, listen to your calls, and steal other sensitive mobile data. Installing apps only from official stores and being careful about permissions is very important for mobile device security.
You should run a full anti-spyware software scan at least once a week. However, a high-quality anti-spyware program should have real-time protection running constantly. This feature actively watches for and blocks threats before they can install themselves. Run a scan immediately if you notice any of the common signs of spyware software infection.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts