.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Insider threat detection is the most vital part of a modern security plan because it addresses the risks coming from people you already trust. To be honest, most of us focus on hackers outside our walls. We build high fences and strong firewalls. But what happens when the risk is already inside? Whether it is a disgruntled employee or a careless contractor, internal threats can cause more damage than any external attack.
In my experience, the hardest part of cybersecurity isn't stopping a stranger; it is noticing when a "friend" starts acting strangely. Have you ever wondered if someone on your team is accidentally sharing sensitive files? Or perhaps you've worried about a worker who might take company secrets to a competitor? These are the questions that keep IT managers up at night.
That is where insider threat detection (ITD) comes into play. It isn't just about spying on people. Instead, it is about creating a safety net. This guide will walk you through how it works, why it matters, and how you can start protecting your assets today.
When we talk about insider threat detection, we are talking about the tools and steps used to find risky behavior by people with authorized access. This includes current employees, former workers, and even third-party vendors. Unlike an outsider who has to break in, an insider already has the keys to the castle.
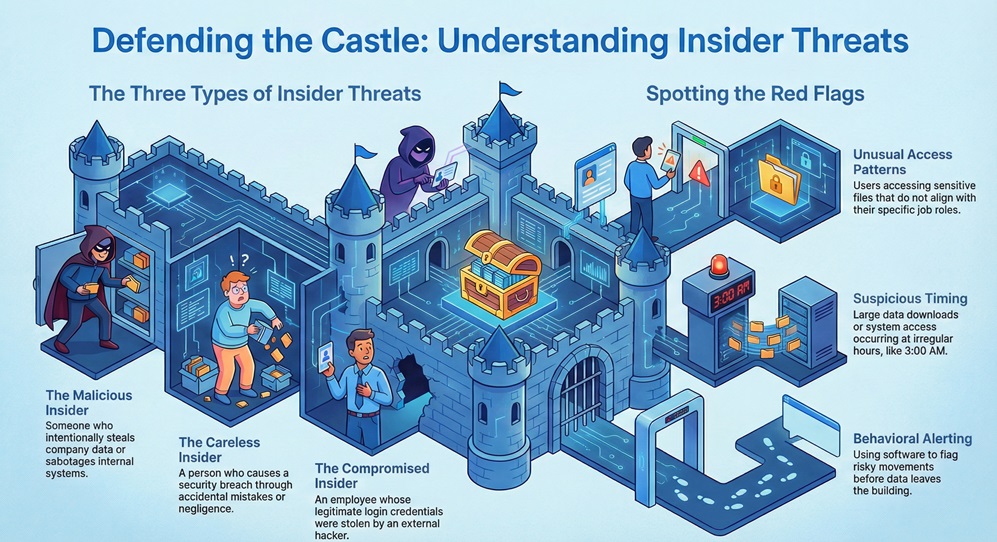
There are three main types of insiders we look for:
So, how do we spot them? We look at patterns. If an accountant suddenly starts downloading engineering blueprints at 3:00 AM, that is a red flag. ITD systems use software to watch these movements and alert you before the data leaves the building.
Here is the thing: your firewall does not care if an admin downloads the entire client database. Why? Because the admin has "permission" to be there. Traditional security looks for "bad" code or "bad" IP addresses. It doesn't look for "bad" intent.
To be honest, we've all been there—trusting our team so much that we forget to check the locks on the inside doors. Research shows that internal breaches often go unnoticed for months. By the time you find out, the damage is done. This is why a dedicated detection system is a must-have, not a nice-to-have.
The heart of modern insider threat detection is something called User and Entity Behavior Analytics. That's a big name for a simple concept: learning what "normal" looks like for every user.
Think of it like a bank. If you usually spend $50 a day and suddenly try to buy a $10,000 watch in another country, the bank calls you. UEBA does the same for your data. It builds a baseline for every employee. It knows when they log in, what files they touch, and how much data they usually send in emails.
When someone strays from that baseline, the system raises a hand. It doesn't necessarily mean the person is doing something wrong, but it tells you that you need to take a closer look.
Also Read: What is Security Operations Center (SOC)?
How can you tell if a risk is brewing? In my view, the signs are often there if you know where to look. Here are some common indicators:
Do you have a way to track these behaviors right now? If the answer is no, you might be flying blind.
You don't need to be a global tech giant to start with insider threat detection. You can start small and grow.
First, identify your "crown jewels." What is the most important data you own? Is it your customer list? Your source code? Once you know what is most valuable, you can put the tightest controls around it.
Second, use the principle of least privilege. This means giving people only the access they need to do their jobs. If a marketing person doesn't need access to HR files, don't give it to them. It sounds simple, but you would be surprised how many companies give everyone "admin" rights just to save time.
Third, look into automated tools. It is impossible for a human to watch every click. Tools like Opentext or other UEBA platforms can do the heavy lifting for you. They sort through millions of events and only show you the ones that look suspicious.
Also Read: What is Static Application Security Testing (SAST)?
I want to be clear: security isn't just about software. It is about people. If your employees feel valued and supported, they are less likely to become malicious insiders. On the other hand, if the culture is toxic, the risk goes up.
Roughly 80% of insider incidents are actually accidental. This means training is your best friend. Teach your team how to spot phishing. Show them how to handle sensitive data. When people understand the "why" behind the rules, they are much more likely to follow them.
It isn't all easy. One of the biggest hurdles is privacy. You want to keep the company safe, but you don't want your employees to feel like they are in a reality TV show.
To solve this, many companies use "anonymized" data. The system watches for bad patterns without showing the person's name until a high-risk alert is triggered. This balances safety with a healthy work environment.
Another challenge is "false positives." Sometimes, an employee is just working late to finish a big project. You don't want to lock them out of their computer every time they work past 6 PM. This is why tuning your insider threat detection tools is so important.
Picture this: A lead developer leaves your company for a competitor. On their last day, they zip up your entire product roadmap and put it on a personal cloud drive. Without detection, you might not find out for a year. By then, your competitor has already launched your "secret" features.
The financial hit from a breach is one thing. The loss of trust from your clients is another. Recovery can take years. When you look at it that way, the investment in a detection system is actually quite small.
Many professionals use a Security Information and Event Management (SIEM) system. Think of a SIEM as a giant logbook. It gathers data from your network, your servers, and your apps. While a SIEM is great for seeing what happened, it isn't always fast enough to stop an insider in the act.
That is why we often pair it with Data Loss Prevention (DLP). A DLP tool is like a guard at the exit. It checks every "bag" (or email) leaving the building. If it sees a credit card number or a secret document, it stops the transfer.
Together, SIEM, DLP, and UEBA create a strong shield. They give you the visibility you need to act fast.
All in all, protecting your company means looking inward as much as you look outward. An insider threat detection strategy combines smart software with a strong company culture. By watching for unusual behavior and limiting access to your most important files, you can stop a disaster before it starts.
We've all seen the headlines about massive data leaks. Don't let your company be the next one. Start by looking at who has access to your data today. Are you sure they are using it correctly?
At our core, we believe that every business deserves to feel secure. We focus on providing the tools and knowledge you need to protect your hard work. Our team is dedicated to your safety because your success is our success. Let’s work together to build a more secure future for your team and your clients.
Contact us today for a security health check

No. It focuses on protecting data and identifying risky patterns. It's about safety, not personal surveillance. Most systems focus on work-related actions and data movement.
The price varies based on the size of your company. However, the cost of a single data breach is usually much higher than the annual cost of the software.
Yes. Many cloud-based security tools offer insider threat detection features that are affordable for smaller teams. You don't need a huge IT department to get started.
This is a type of malicious insider threat where an employee hides code in a system that "explodes" (deletes data or shuts things down) after they leave the company. Detection tools look for these hidden changes in code.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts