
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Next Generation Antivirus (NGAV) refers to a security solution that goes beyond traditional, signature-based antivirus to protect endpoint devices from modern, complex cyber threats. This new approach is vital because older antivirus software cannot keep up with advanced threats like fileless malware and zero-day attacks. It provides essential protection for every device connected to your network.
NGAV is composed of two essential components: advanced protection techniques and cloud-based intelligence.
The advanced techniques include machine learning (ML) and behavioral analysis, which look for suspicious actions instead of just known virus signatures. It consists of a lightweight endpoint sensor and a powerful cloud platform that works together. This approach is much more effective against the fast-moving threats faced by businesses, including those in high-growth areas like the UAE and the wider GCC region.
In this section, we will discuss Next Generation Antivirus in detail along with its features and advantages. You will learn why this modern security is a must-have for your organization.
Next Generation Antivirus can be defined as a comprehensive security platform that uses modern technology to protect endpoints (like laptops, servers, and mobile phones) from a broad range of malicious threats. NGAV does not just check a database of known threats. It uses intelligent methods to stop new and unknown dangers before they can cause damage.
NGAV utilizes things like machine learning and artificial intelligence (AI) to analyze file features and behaviors. For example, if a program starts doing something unexpected, like trying to encrypt a large number of files, the NGAV solution flags it immediately, even if the program's code has never been seen before. This method is much better than the old way of waiting for a security update.
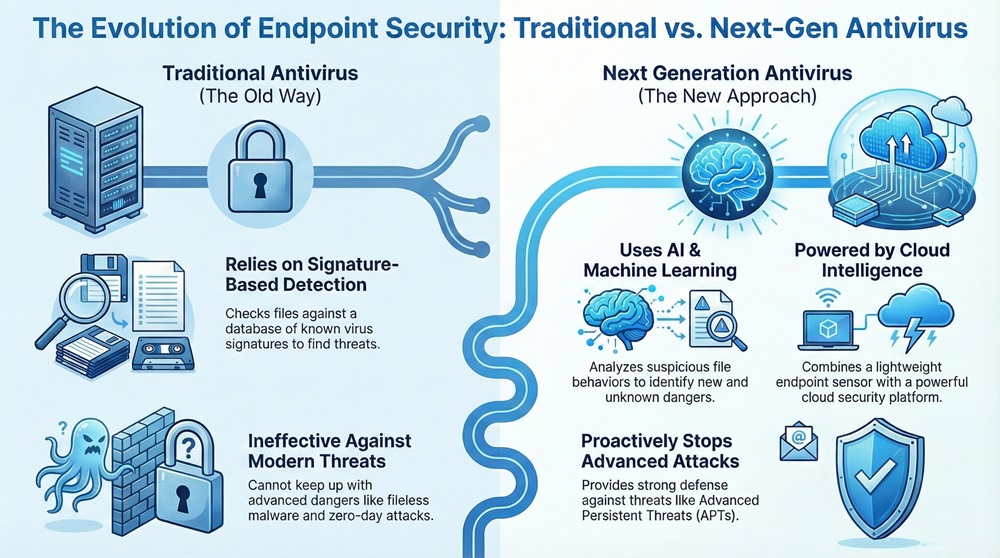
In simple words, NGAV is the crucial replacement for the outdated, traditional antivirus you might still be using. Do you think older antivirus solutions can truly stop a modern, targeted attack? NGAV offers a much stronger defense against attacks like Advanced Persistent Threats (APTs), which are a serious concern for organizations operating in the GCC.
Upgrade from legacy antivirus to 2025-grade protection
Next Generation Antivirus solutions are composed of several key elements that work together to provide complete protection. Understanding these components shows why NGAV is so powerful compared to traditional solutions.
It consists of two major parts: the endpoint agent and the cloud-based security platform. The endpoint agent is a small piece of software installed on your device. It constantly monitors activity without slowing your computer down. The cloud-based security platform is the brain, where all the complex analysis and threat intelligence happen.
The major components are:
Next Generation Antivirus cannot function correctly without a fast, smart cloud component. The cloud offers the massive computing power needed for the advanced analysis that makes NGAV effective.
Next Generation Antivirus works by constantly watching the behavior of everything on your system. It does not wait for a virus to match a signature. This is a massive shift in how security is handled.
Here, we will see how the NGAV system operates step-by-step:
Also Read: What is a Next Generation Firewall (NGFW)? Why UAE/GCC businesses need it?
Next Generation Antivirus possesses several characteristics that make it a better choice for modern endpoint protection than older antivirus tools. These features are key to stopping today's advanced attacks.
Following are the key characteristics:
For instance, a traditional antivirus would ignore a seemingly harmless script. However, the NGAV would monitor the script's behavior. If it attempts to gather user credentials, the NGAV immediately blocks the suspicious behavior, even though the script itself is not in any virus database.
Next Generation Antivirus is built to handle the complex types of attacks that traditional antivirus software cannot stop. The types of threats it handles are more varied and harder to detect than ever before.
NGAV is essential for stopping modern threats:
To understand the threat fully, let us now discuss how ransomware can be stopped. The system observes the file system. When it sees an unauthorized process rapidly changing file extensions and encrypting data, the NGAV concludes that this is malicious behavior and immediately stops the process, limiting the damage to a small number of files.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
Next Generation Antivirus delivers many advantages that offer superior endpoint security compared to the older generation of protection. These benefits translate directly into better protection and lower operational cost for you.
Following are the significant advantages:
Furthermore, NGAV often provides forensic visibility. This means that when an alert happens, you get a full, detailed story of what the threat did and where it came from. This deep visibility is critical for internal compliance and future defense planning.
While Next Generation Antivirus is a major step forward, it is not a perfect shield. It is important to know its limitations to build a complete cybersecurity strategy.
One must note here that the constant evolution of threats means no security solution can ever be set and forgotten. The best Next Generation Antivirus systems are those that are actively monitored and updated by experienced security professionals.
Also Read: What is an Intrusion Detection System (IDS)? Components and Types
Next Generation Antivirus is a flexible security solution with critical applications across all types of organizations, from small businesses to large enterprises in the GCC and beyond.
For example, a major bank in Dubai uses Next Generation Antivirus on all its servers and employee computers. The system not only stops everyday threats but also provides detailed reports to the bank’s security operations center (SOC). This high level of visibility and threat intelligence is what sets NGAV apart and protects financial assets effectively.
Next Generation Antivirus represents a necessary evolution in endpoint security. It moves past the limitations of traditional, signature-based solutions to offer a proactive, intelligent defense powered by machine learning and cloud intelligence. The platform's ability to stop fileless malware, zero-day threats, and complex ransomware is essential for any organization, especially those facing increasing cyber threats in fast-paced markets like the UAE and the Middle East.
Therefore, understanding and implementing Next Generation Antivirus is no longer a choice but a critical requirement for a secure business. It provides a deeper level of threat detection and an automated response capability that minimizes risk and reduces the burden on your IT security team.
You deserve a security partner that believes in constant innovation and provides the highest level of proactive protection. We offer verified, cutting-edge Next Generation Antivirus solutions designed to secure your most valuable assets, allowing you to focus on your business growth with complete confidence.
The main difference is the detection method. Traditional antivirus relies on a database of signatures (known virus code) to find threats. NGAV uses machine learning and behavioral analysis to find unknown threats by monitoring the actions a program performs on a system.
Yes, absolutely. Fileless malware does not use files, so it bypasses traditional signature checks. NGAV can stop it because it monitors the malicious behavior this malware exhibits, such as attempting to inject code or execute suspicious scripts like PowerShell commands.
The cloud is vital. It hosts the massive Machine Learning (ML) engines and cloud threat intelligence that power the system. This allows the lightweight endpoint sensor to send suspicious data for powerful, real-time analysis without slowing down the user's device.
A zero-day exploit is an attack that targets a software vulnerability before the vendor has a patch (zero days of warning). NGAV defends against it by focusing on the malicious behavior of the exploit, even if the code itself is brand new, blocking the attack before it can complete its task.
No, but they work together. NGAV is primarily a prevention tool that blocks malware. EDR (Endpoint Detection and Response) is focused on detection, investigation, and response. EDR provides the security team with the deep visibility and tools needed to respond to threats that get past the initial block.
Generally, no. Since the heavy-duty analysis and computing happen in the cloud, the endpoint agent is designed to be lightweight and have a low system impact. This is a major advantage over older antivirus programs.
No. Unlike traditional antivirus that relies on daily signature updates, NGAV solutions typically update their core machine learning models in the cloud automatically. The endpoint agents update infrequently, making maintenance much simpler.
Yes, very effectively. NGAV is cloud-native and provides the same high level of endpoint protection regardless of whether the device is on the corporate network or connected remotely, which is critical for a distributed workforce.
Most modern NGAV solutions still retain a powerful local machine learning model on the endpoint. This ensures that a high percentage of known and unknown threats can still be blocked even when the device is completely offline.
Yes. Businesses in the GCC face the same sophisticated cyber threats as large enterprises. NGAV offers automated, high-efficacy protection and simplified management, making enterprise-grade security accessible and cost-effective for smaller organizations.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts