.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Have you ever sat at your desk, waiting for a file to download from the company server, only to watch the progress bar crawl like a snail? It’s frustrating. We’ve all been there, staring at a spinning wheel while trying to join a video call or open a shared doc. This lag often happens because of how a Wide Area Network (WAN) handles data over long distances. To fix this, IT teams use WAN Optimization to make sure data moves quickly and efficiently between offices.
But what exactly is happening behind the scenes? In simple terms, it's a collection of techniques used to increase the speed of access to critical applications and data. Think of it as a specialized toolkit that clears the "traffic jams" on your digital highway. If you've ever wondered why your branch office feels slower than the main headquarters, the answer usually lies in the limitations of the network.
To understand this concept, we first need to look at the Wide Area Network itself. A WAN connects different sites, like a home office in New York to a data center in London. Unlike a local network in your house, a WAN covers huge distances. Because the data has to travel so far, it hits two big roadblocks: limited bandwidth and high latency.
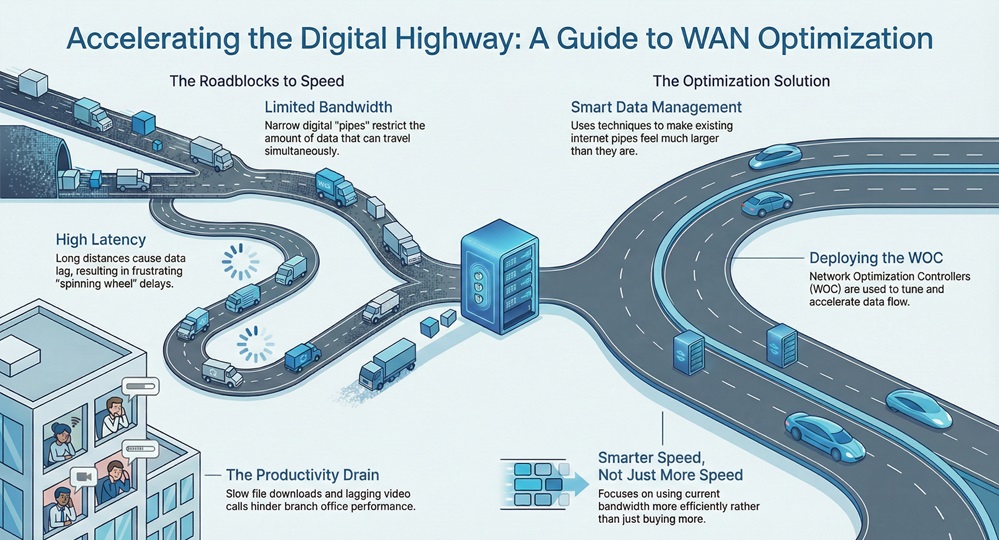
WAN Optimization refers to the methods used to overcome these hurdles. By using a Wide Area Network Optimization Controller (WOC), businesses can make their existing internet pipes feel much larger than they actually are. It isn't just about buying more speed from an ISP. Instead, it’s about using the speed you already have in a smarter way.
Have you noticed how some apps work perfectly at home but lag at work? That is often a sign that the network needs a bit of tuning.
You might think that the only way to get a faster network is to pay for a bigger "pipe." However, that’s often expensive and doesn't always solve the problem of distance. Here is how we actually optimize the flow of data:
1. Data Compression
Just like zipping a folder on your computer, data compression shrinks the size of files moving across the network. When the files are smaller, they take less time to travel. It’s a simple "less is more" approach that saves a massive amount of space.
2. Data Deduplication
This is a fancy way of saying "don't send the same thing twice." Imagine you send a 10MB email to ten people in the same branch office. Without deduplication, the network sends that 10MB file ten times. With optimization, the system identifies the repetitive data. It sends the full file once and then just sends a tiny "marker" for the other nine. This can reduce traffic by up to 90% in some cases!
3. Latency Optimization (Protocol Acceleration)
Latency is the time it takes for a data packet to travel from point A to point B and back. Some "chatty" protocols require hundreds of "handshakes" to move a single file. Optimization reduces these back-and-forth trips. It "tricks" the system into thinking the data has arrived sooner, which keeps the flow moving without pauses.
4. Traffic Shaping and QoS
Not all data is equal. A Zoom call is more important than a background Windows update. Traffic shaping (or Quality of Service) ensures that important apps get the "fast lane" while less urgent tasks wait in the back.
Also Read: What is a Wide Area Network (WAN)? Architecture & Types Explained
In my experience, many business owners ignore their network until it breaks. But waiting for a crash is a risky move. Efficient networks don't just happen; they are built. When you implement these tools, you aren't just helping the IT department. You are helping every single employee who uses a computer.
Why spend thousands on new fiber lines when you can optimize what you have? Roughly 60% of network traffic is often repetitive. By cleaning that up, you free up space for what matters. To be honest, it’s often the most cost-effective way to scale a growing company.
The "brain" of this operation is the WOC. This device (or software) sits at each end of the network connection. It looks at every packet of data leaving the office and asks, "Can I make this smaller? Have I sent this before?"
When the data reaches the other side, the second WOC puts it back together perfectly. It’s a seamless process. You won't even know it’s happening, except for the fact that your apps suddenly feel snappy again. We've seen companies reduce their data usage significantly just by installing these controllers at their main hubs.
Let's break down the technical side into simple steps. Most providers use a mix of these three pillars:
Does your current setup handle these tasks, or are you just throwing more money at your ISP every year?
Also Read: What is a Wireless LAN Controller? Configuration & Setup 101
Fast-forward to today, and you might hear the term SD-WAN (Software-Defined WAN). While traditional optimization focuses on the "inside" of the data packets, SD-WAN focuses on the "path" the data takes. Many modern businesses use both. They use SD-WAN to pick the best route and WAN Optimization to make the data as light as possible. It’s the ultimate combo for a global workforce.
If you are still on the fence, consider these points:
If your business has more than one location, or if you use a lot of cloud-based tools, the answer is likely yes. Small businesses with a single office might not need it yet. However, the moment you start connecting remote teams to a central hub, the "distance tax" starts to add up.
In my view, we are moving toward a world where the network is the backbone of everything we do. You wouldn't build a house on a shaky foundation, right? So, don't build your business on a slow, cluttered network.
At the end of the day, your network should work for you, not against you. WAN Optimization is the bridge that connects your global team without the lag that usually comes with distance. By focusing on data efficiency rather than just raw speed, you create a smoother experience for everyone.
At our core, we believe in empowering businesses with the right technology. We don't just provide tools; we provide solutions that grow with you. Our focus is always on your success and making sure your team stays connected, no matter where they are in the world. Ready to see what a faster network feels like? It's time to stop waiting and start optimizing.

Yes! Many optimizers have specific tools to speed up cloud traffic by reducing the distance and "chatter" between your office and the cloud provider's data center.
No. A VPN creates a secure "tunnel" for your data. Optimization makes the data inside that tunnel move faster. You often use both together for a secure and fast connection.
It mostly helps with "internal" business traffic (like accessing files or company software). While it can help general browsing through caching, its main power is in business-specific applications.
Basic software-based optimization can be set up in a few hours. Larger hardware installations for global offices might take a few days to configure perfectly.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts