.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Security automation refers to the use of software-driven workflows to detect and resolve cyber threats with minimal human help. Have you ever felt like you're trying to drink from a firehose while managing security alerts? We've all been there. Your inbox fills up, the dashboard turns red, and the pressure to react fast becomes heavy.
To be honest, the old way of doing things manually just doesn't work anymore. Hackers use machines to attack you, so why are we still relying solely on human speed to defend ourselves? This guide will show you how security automation fixes that. We’ll look at how it works, why it’s a game-changer for your team, and how you can start using it today.
At its heart, security automation is about taking the boring, repetitive tasks off your plate. Think about the hundreds of low-level alerts your system creates every day. Most of them are noise, but you still have to check them. Automation handles this by following a set of rules or "playbooks."
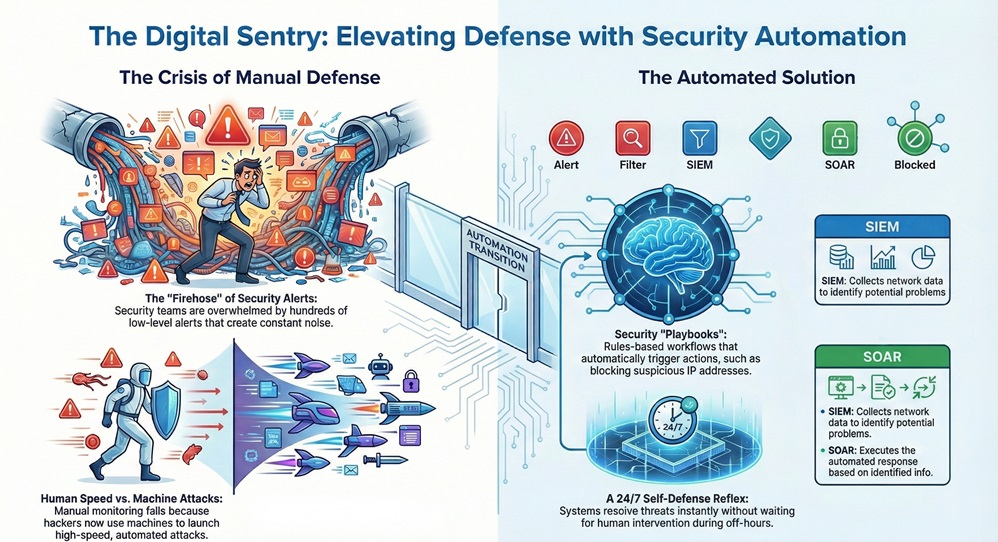
When a specific event happens, the system knows exactly what to do. For example, if it sees a login attempt from a suspicious country, it can block that IP address immediately. It doesn't wait for you to wake up at 3 a.m. to click a button. By using security automation, you're basically giving your network a self-defense reflex.
You might hear people talk about SOAR (Security Orchestration, Automation, and Response) or SIEM (Security Information and Event Management). These are the "brains" of the operation. A SIEM collects data from all over your network to find problems. Then, the SOAR takes that info and executes the response.
Is it magic? Not quite. It's just smart software doing the heavy lifting so you don't have to.
The most obvious benefit of security automation is speed. In the world of cybersecurity, every second counts. If a piece of malware enters your system, it can spread to your servers in minutes. A human might take an hour to see the alert and investigate. An automated system does it in seconds.
1. Stopping Alert Fatigue
We often see talented security pros quit because they're tired of "alert fatigue." It’s exhausting to look at 1,000 alerts just to find the one that actually matters. Automation filters out the "false positives." This means your team only spends time on the real dangers.
2. Reducing Human Error
We’re only human, right? We make mistakes when we’re tired or rushed. According to some reports, over 70% of data breaches involve some form of human error. Security automation follows the plan perfectly every single time. It doesn't get distracted by a phone call or forget a step in the protocol.
3. Scaling Your Defense
As your company grows, so does your digital footprint. You’ll have more devices, more cloud accounts, and more data. You can't just keep hiring more people to watch every screen. Security automation allows your current team to protect a much larger environment without getting overwhelmed.
Also Read: SIEM vs SOAR Comparison: 5 Key Differences
Let’s talk about how this actually looks in the real world. It isn't just about blocking IPs. It covers a lot of ground in your daily operations.
In my experience, the biggest win is often the simplest one. Automating password resets or basic user access saves hours of ticket time every week.
Wait, aren't those the same thing? Not quite. Here's a simple way to think about it:
You need both. Automation gives you speed, but orchestration gives you a complete strategy. When you combine them, you get a "layered defense" that is very hard to break.
Also Read: What is Cloud Identity and Access Management?
You don't have to automate everything on day one. In fact, please don't! That's a recipe for a broken network.
Start Small
Look for the tasks that happen every day and take up the most time. Are you manually checking firewall logs? Start there. Create a simple "if this, then that" rule. Once you trust the system, you can move on to more complex workflows.
Use Playbooks
A playbook is just a fancy word for a "how-to" guide for your software. You write down the steps a human would take to fix a problem, and then you teach the software to do those steps. Most modern tools come with pre-built playbooks for things like malware or unauthorized logins.
Keep a Human in the Loop
Roughly speaking, you want a "semi-automated" approach for big decisions. For example, the system can find and isolate a threat, but maybe you still want a human to give the final "okay" before wiping a server. This gives you the best of both worlds.
At the end of the day, security automation is about being proactive instead of reactive. We believe that every company deserves a defense that doesn't sleep. Our values are built on helping you stay safe without making your life more complicated. We focus on our clients' success by providing the tools they need to stay ahead of the bad guys.
Are you ready to stop chasing alerts and start leading your security strategy? We’re here to help you every step of the way.

To be honest, no. It replaces the boring parts of your job. It frees you up to do the "cool" stuff like threat hunting and architecture design.
There is an upfront cost for tools and training. However, the ROI (Return on Investment) is huge when you consider the cost of a single data breach or the time saved by your staff.
This is why we test everything in a "sandbox" first. You should always monitor your automated workflows and refine the rules as your network changes.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts