.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Cloud VPN provides a secure way to connect your networks to a cloud provider's network. This technology is vital for businesses that want the flexibility of the cloud while keeping their connections private and protected.
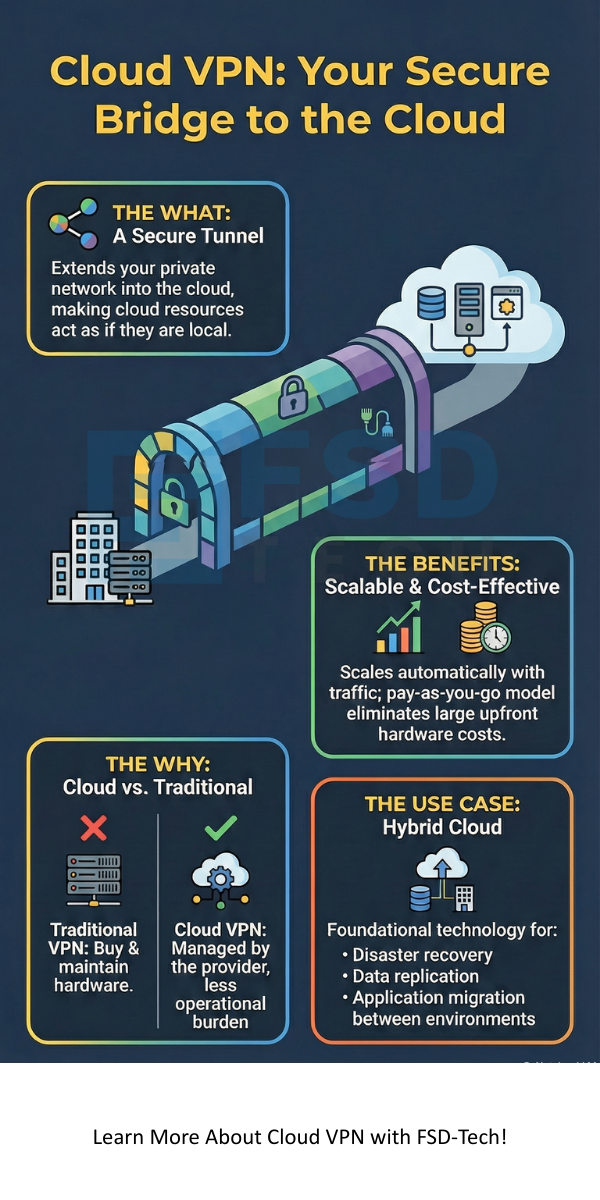
You likely use a Virtual Private Network (VPN) in your daily life to protect your personal information. Cloud VPN works on a similar principle but on a much larger, corporate scale. It creates a secure tunnel for your data as it travels between your on-premises data center and your Virtual Private Cloud (VPC) network.
To understand this better, think of it this way: your Cloud VPN acts as a private, armored car on the public internet highway. It ensures no one can read your sensitive documents while they move from one secure location to another. Cloud VPN is essential for maintaining privacy and data security in today’s hybrid cloud environments.
When we compare different types of VPNs, the first question that arises is, "What makes Cloud VPN different?" The key distinction lies in the management and location of the VPN endpoint.
A traditional VPN requires you to purchase, set up, and maintain physical hardware—the VPN servers—in your own data center. You bear the entire burden of managing these devices, including updates, patches, and scaling.
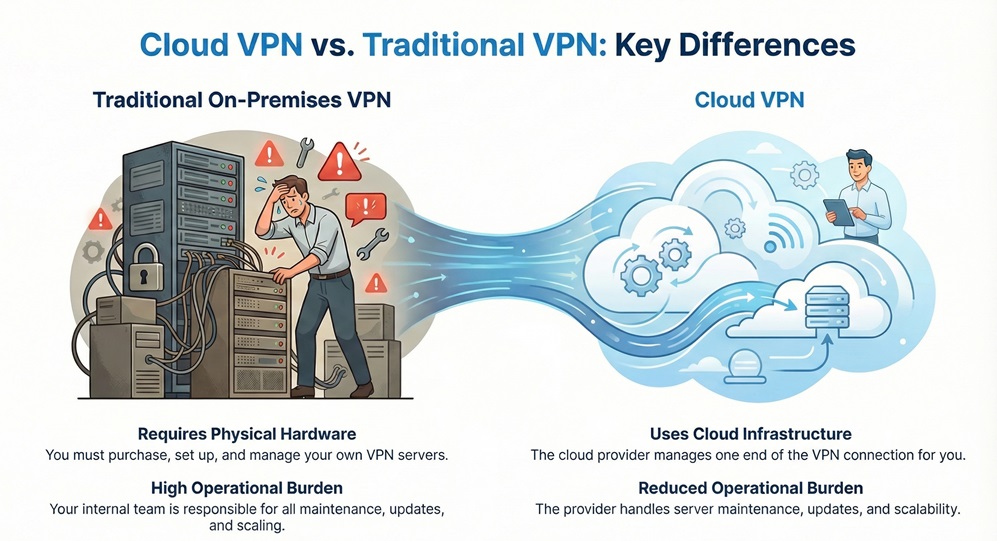
On the other hand, a Cloud VPN uses the cloud provider's infrastructure to manage one end of the connection. The cloud provider handles the VPN server maintenance, updates, and scalability. This shift significantly reduces your operational burden.
| Basis for Comparison | Cloud VPN (Virtual Private Network) | Traditional On-Premises VPN |
|---|---|---|
| Management | Mostly managed by the cloud provider | Fully managed by the user/organization |
| Scalability | Cloud VPN offers easy, on-demand scaling | Scaling requires purchasing and installing new hardware |
| Cost Structure | Pay-as-you-go, service-based pricing | High upfront capital expenditure for hardware |
| Location of Endpoint | One endpoint is in the cloud provider's VPC network | Both endpoints reside in the user's physical locations |
| Latency/Performance | Often optimized for the cloud environment | Performance depends on the user's hardware and network |
Cloud VPN can be understood as a service that establishes a secure, encrypted connection—an IPsec VPN tunnel—between your non-cloud network (like your office network) and your Virtual Private Cloud (VPC) network within the cloud environment.
This secure connection is vital for various reasons:
Cloud VPN typically relies on the Internet Protocol Security (IPsec) protocol. IPsec ensures that data is encrypted before it leaves the source and decrypted only at the destination, guaranteeing confidentiality.
Also Read: What is Disaster Recovery in Cloud Computing?
To transfer data securely, a Cloud VPN connection consists of several essential components:
Cloud VPN servers are not traditional physical boxes you own. Instead, the term refers to the VPN service running as a component of the cloud provider's infrastructure. This arrangement provides significant benefits for you, the user.
Let us now discuss the advantages of using Cloud VPN servers.
Also Read: What is Zero Trust Security Model? All You Need to Know
Hybrid cloud VPN refers to the architecture that uses a Cloud VPN connection to link an organization’s on-premises infrastructure with its cloud infrastructure. This setup is a cornerstone of hybrid cloud computing.
A hybrid cloud VPN allows you to leverage the benefits of both environments:
Hybrid cloud VPN essentially makes the two separate environments—local and cloud—function as one single, seamless network.
Here are some common situations where businesses use a hybrid cloud VPN:
Also Read: What is an Email Security Gateway? Protecting Your Inbox
The term "VPN cloud storage" refers to the concept of securing access to data stored in the cloud using a Virtual Private Network. It is not a separate technology but rather a key application of Cloud VPN.
When you store data in a cloud storage service, access to that data usually happens over the internet. By implementing a Cloud VPN, you ensure that any traffic accessing or transferring the data is encrypted and goes through a private tunnel.
This secure access method provides two main advantages for VPN cloud storage:
Establishing a secure Cloud VPN connection involves a sequential process. To understand this better, let us explore the steps you need to follow.
Also Read: What is Web Application Firewall? | WAF Explained
A common question for businesses looking into this solution is, "Is Cloud VPN free?" The straightforward answer is no, Cloud VPN is typically not a free service.
Cloud providers charge for the Cloud VPN service based on a few distinct components. This consumption-based model is different from the upfront cost of traditional VPN hardware.
Let us look at the typical cost components:
Understanding this model helps you accurately budget your cloud VPN usage. The flexibility means you only pay for the resources you actively use, which is a major advantage.
Beyond connecting two corporate networks, Cloud VPN also plays a role in modern secure remote access. In a remote-work environment, your employees often need to access both on-premises applications and cloud-based services.
A well-designed Cloud VPN can secure remote access for your users in the following manner:
This approach centralizes security, making management simpler and ensuring that all user access points—regardless of location—go through the same strong encryption protocols.
Implementing a Cloud VPN solution provides numerous benefits that help businesses modernize their IT infrastructure.
Cloud VPN is a foundational technology for any organization operating a hybrid cloud environment. It solves the critical challenge of securely connecting disparate networks over the public internet. By adopting Cloud VPN, you significantly reduce your operational overhead, gain the flexibility of scalable bandwidth, and ensure that your sensitive data remains encrypted during transfer.
Proactive Cloud VPN Contact our team
Here are the essential points about Cloud VPN you should remember:
A: The main purpose is to create a secure, encrypted IPsec tunnel that securely connects your on-premises network to your Virtual Private Cloud (VPC) network in the cloud.
A: Yes. When you use a Cloud VPN to access or transfer data to and from cloud storage, the data is encrypted while in transit through the secure tunnel, ensuring VPN cloud storage is protected.
A: Cloud VPN servers are designed to automatically scale their capacity. As your traffic increases, the cloud infrastructure handles the additional load without requiring manual upgrades or new hardware purchases from you.
A: Yes, you can use a Cloud VPN or related cloud services to establish a secure path for remote employees. This allows them to securely access company resources that reside in both your data center and the cloud environment.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts