
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

As threats constantly evolve, traditional security methods often fall short. They assume that everything inside a network is trustworthy. This old way, often called perimeter security, trusts a user simply because they are inside the network's boundary.
Now, the question arises: What if an attacker manages to breach that boundary? The traditional model offers little defense once an intruder is inside the network.
This is where the Zero Trust security model comes in.
To understand this better, you must change your way of thinking about network security. The core philosophy of this model is simple: Never trust, always verify.
This guide will explain the Zero Trust security model so you can see why it is essential for your organization. You will learn about its key principles and how to start using it effectively.
The Zero Trust security model fundamentally changes how organizations approach network defense. It operates on the core principle: "Never trust, always verify." This means that no user, device, or application is implicitly trusted, regardless of their physical location or network position.
The primary purpose of Zero Trust security model is to minimize risk by strictly enforcing access control for every single request. It grants access based on least privilege, requiring continuous verification of identity and device health.
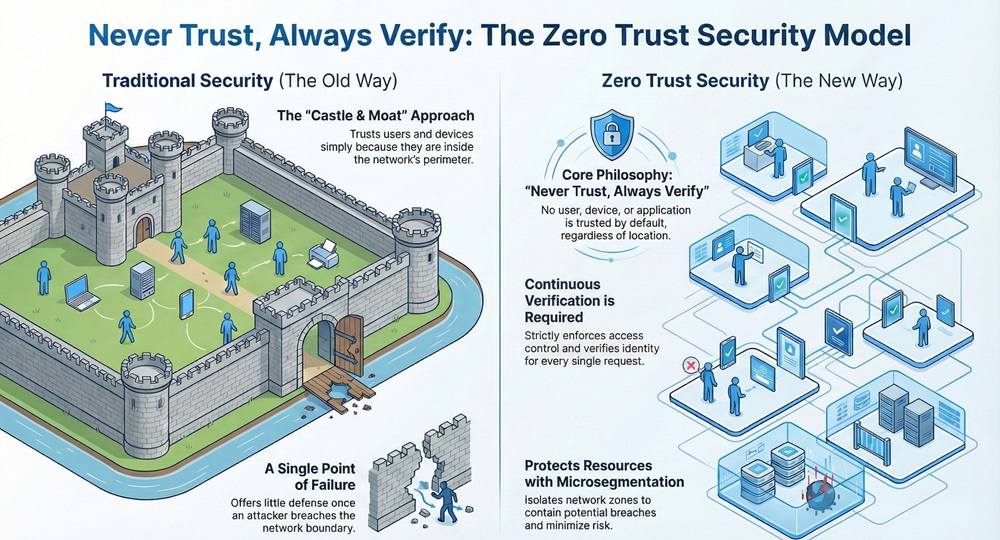
This architecture protects resources by using microsegmentation to isolate network zones, assuming a breach is inevitable. This rigorous, evidence-based approach safeguards your data effectively.
The Zero Trust security model completely changes the way we approach security. It shifts the focus from where a user is located to who they are, what they are accessing, and why they are accessing it.
In simple words, the Zero Trust security model treats every user and device as a potential threat, even if they are already on the network. This approach ensures that every access request undergoes strict verification.
Let us now discuss the fundamental difference between the old way and the modern Zero Trust approach.
| Basis for Comparison | Traditional Perimeter Security | Zero Trust Security Model |
|---|---|---|
| Trust Philosophy | Trust implicit (trust within the network) | Never trust, always verify |
| Network Focus | The network perimeter is the main defense. | The resource (data, application, asset) is the defense focus. |
| Access Control | One-time check at the network boundary. | Continuous, granular authorization for every access. |
| User Access | Once inside, users often get broad access. | Least privilege access is granted. |
| Security Scope | Primarily focused on the network layer. | Every layer (user, device, network, application, data). |
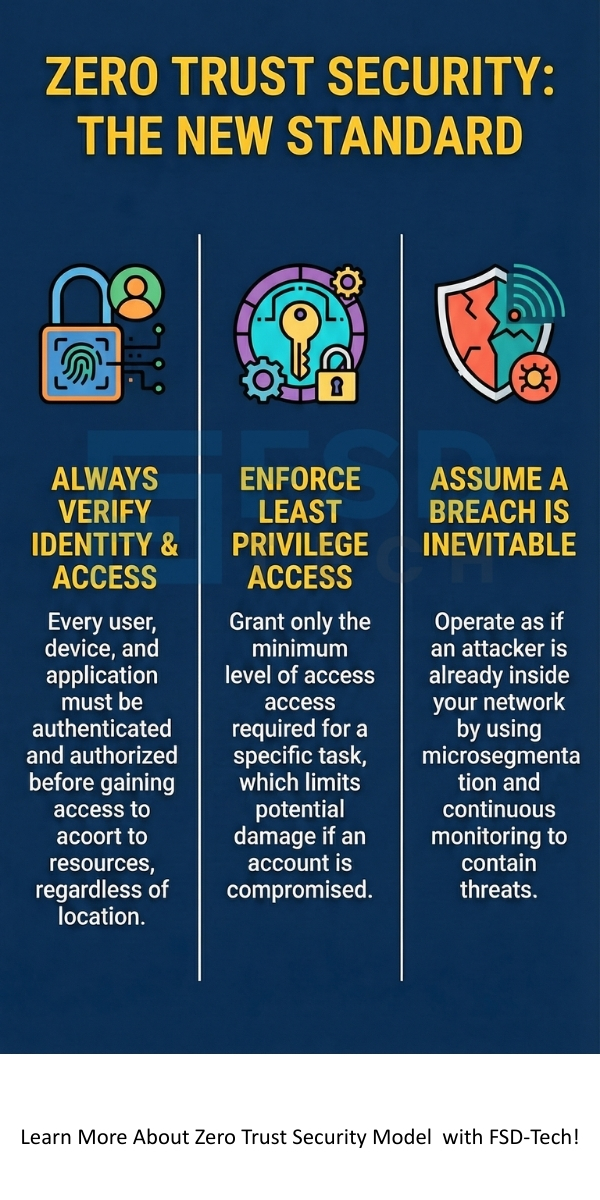
The primary purpose of Zero Trust security model is to minimize risk by removing implicit trust from the network. This model is based on three main principles that guide all security decisions.
1. Always Verify Identity and Access
This principle is the foundation of the Zero Trust security model meaning. It implies that you must authenticate and authorize every request before access is granted.
This includes requests from:
2. Implement the Principle of Least Privilege
This principle ensures that a subject (user, device, or application) gets only the minimum level of access they absolutely need to perform a task. Least privilege access reduces the potential damage an attacker can cause if they gain access to an account.
For example, a marketing analyst does not need access to the company's full financial records. Giving them access only to the necessary marketing data fulfills the least privilege requirement.
3. Assume Breach
A Zero Trust security model in cybersecurity takes a pragmatic view: It operates as if a breach has already happened or is imminent. Due to this assumption, you do not rely on the network perimeter for defense.
This approach necessitates:
Also Read: What is an Email Security Gateway? Protecting Your Inbox
The Zero Trust architecture (ZTA) is the planning and methodology you use to implement the Zero Trust security model. It involves several key components working together to enforce the "never trust, always verify" philosophy.
1. The Policy Engine (PE)
The Policy Engine determines the "allow or deny" decision for an access request. This component essentially answers the question, "Should this user/device access this resource right now?"
The Policy Engine utilizes security policies and inputs from various sources to make its decision. The Zero Trust security model explained hinges on the smart decisions this component makes.
2. The Policy Administrator (PA)
The Policy Administrator executes the access decision from the Policy Engine. It is the component that communicates with the gatekeeper, which is the Policy Enforcement Point (PEP), to grant or deny the connection.
The Policy Administrator sets up and tears down the secure path between the subject and the resource.
3. The Policy Enforcement Point (PEP)
This component is the gatekeeper that actually enforces the decision. The Policy Enforcement Point (PEP) acts as a control plane for access.
The PEP can be a firewall, an application gateway, or a specialized proxy. It is the tool that monitors and terminates connections based on the Policy Administrator’s instruction.
4. The Data Plane and Control Plane
Also Read: What is Sandboxing in CyberSecurity? How It Works?
The Zero Trust framework includes several crucial supporting components that provide data and context for the Policy Engine's decisions.
A. Continuous Diagnostics and Mitigation (CDM)
Which component of the Zero Trust security model focuses on evaluating the security posture of the access device? The answer is the Continuous Diagnostics and Mitigation (CDM) System.
This system gathers information about the security status of every device.
B. Identity Management System (IDMS)
The Identity Management System is responsible for creating, maintaining, and managing user accounts and their digital identities. This system enforces Multi-Factor Authentication (MFA) and manages the digital certificates.
The IDMS is a vital part of the access decision process as it confirms who the user is.
C. Public Key Infrastructure (PKI)
The Public Key Infrastructure (PKI) is used to issue and manage digital certificates. These certificates verify the identity of users, devices, and applications when they communicate. This system ensures strong cryptographic verification.
D. Security Information and Event Management (SIEM)
The SIEM system collects and analyzes security logs and event data from all network components. It identifies potential threats and anomalies that could indicate a breach.
The Zero Trust security model in cloud computing relies heavily on SIEM to provide real-time visibility into activities across diverse environments.
E. Threat Intelligence Feeds
These are external data sources that provide information about current and emerging threats, vulnerabilities, and attacker tactics. The Policy Engine uses this intelligence to make more informed and proactive access decisions.
For example, if a feed indicates a new attack is exploiting a specific weakness, the Policy Engine can temporarily deny access to all devices that have not yet patched that weakness.
Also Read: Zero Day Attack: How It Works & Prevention Guide
The Cybersecurity and Infrastructure Security Agency (CISA) provides a Zero Trust Maturity Model to help organizations plan and track their transition to a full ZT architecture. This model involves moving through different stages of maturity across five specific pillars.
Let us explore these key pillars:
1. Identity
This pillar focuses on verifying the individual user or machine identity seeking access.
2. Device
This pillar focuses on validating the device used to access the network.
3. Network/Environment
This pillar is about the infrastructure and microsegmentation.
4. Application Workload
This pillar focuses on securing applications and services.
5. Data
This is arguably the most important pillar, as data is the asset you are protecting.
The Zero Trust security model marks a necessary evolution from outdated perimeter-based security, which no longer serves modern, distributed networks and cloud environments. By adhering to the crucial mandate, "Never trust, always verify," this model systematically eliminates the concept of implicit trust within the network. Its core framework relies on least privilege access and microsegmentation to protect critical assets.
Implementing the Zero Trust security model is not about buying one tool, but about a strategic shift—it establishes continuous authentication and authorization as the baseline, actively reducing the attack surface and significantly bolstering your organization's defense against sophisticated breaches.
Start Zero Trust Contact FSD-Tech today
The Zero Trust security model is not just a trend; it is the future of robust security. It provides a way to secure modern, complex, and distributed environments like the cloud.
The primary purpose of Zero Trust security model is to eliminate the concept of implicit trust and require verification for every access request. Remember these points:
By understanding and adopting the Zero Trust security model, you are taking a critical step toward safeguarding your organization's most valuable assets in the face of sophisticated threats. Take control of your security posture and secure your future now.
Adopting a Zero Trust security model is a major project. The biggest challenge often involves changing the organizational culture and the complexity of migrating legacy systems. Existing networks often have vast, flat access structures that require extensive re-engineering for microsegmentation.
No, Zero Trust is not a single product. It is an architectural approach and a set of security principles. You implement this model using various security tools and technologies that already exist. This approach requires a strategic, phased implementation.
Yes, the Zero Trust security model in cloud computing is extremely important. Cloud environments are inherently perimeter-less, which makes the traditional security model ineffective. Zero Trust principles like strong identity verification and microsegmentation are essential for securing cloud resources and data.
After a user is authenticated, the process continues. They are authorized based on least privilege, and their session is continuously monitored. If the user's risk posture changes (e.g., they access from a new location), the Policy Engine can re-authenticate them or revoke access immediately.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts