.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Have you ever worried about invisible weak spots in your company's digital setup? You know that cyber threats are always changing. Digital growth is essential, but it also creates new doors for attackers to walk through. This growing risk makes many businesses feel uneasy.
You need a way to see your entire security risk—everything an attacker could target—from their point of view. This is where Attack Surface Management (ASM) becomes absolutely critical.
Attack Surface Management (ASM) provides you with a clear, complete picture of every part of your digital presence that an attacker could potentially exploit. By understanding your full attack surface, you take control. You can stop attackers before they even start looking for holes.
Do you want to find and fix those hidden risks right now? Let us understand how.
Attack Surface Management (ASM) can be understood as the continuous process of discovering, inventorying, classifying, prioritizing, and monitoring all digital assets that are exposed to the internet. This includes the assets you know about and, more importantly, the ones you do not.
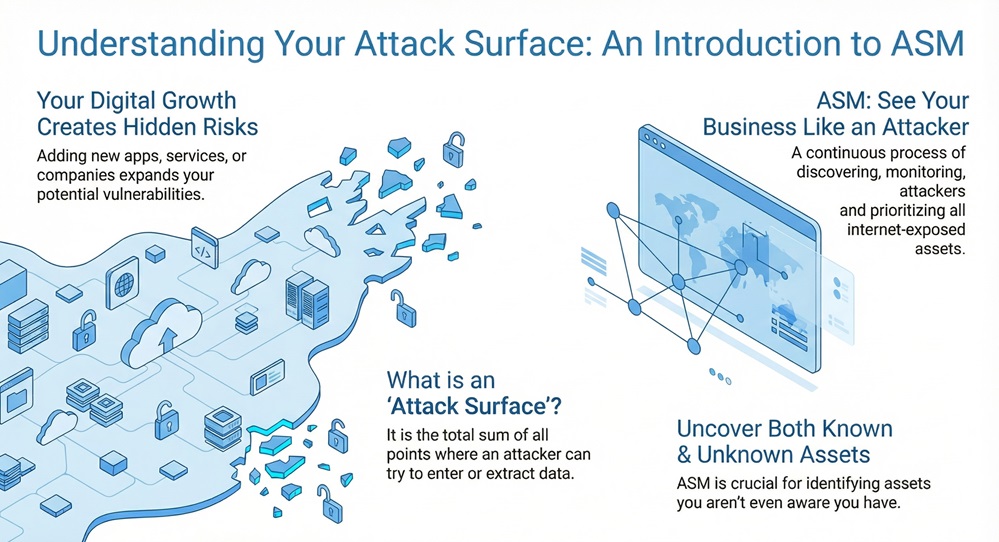
Attack Surface Management provides your security team with a continuous, outside-in view of your network. This view mirrors how a cybercriminal sees your company. ASM identifies all digital entry points. These entry points are collectively known as the attack surface.
The attack surface refers to the total sum of all possible points where an unauthorized user can try to enter or extract data from an environment. It consists of all the code, connections, and open ports that an attacker can exploit.
The attack surface generally increases as your business grows. When you add new cloud services, merge with another company, or launch a new app, you also increase your attack surface. Understanding this surface is the first step toward reducing it.
Also Read: What is Patch Management? Securing Your Digital Assets
Many people confuse Attack Surface Management (ASM) with traditional Vulnerability Management (VM). While both aim to improve security, they focus on different areas. Attack Surface Management is broader; it tells you what you have exposed. Vulnerability Management is deeper; it tells you which flaws exist on the known assets.
To understand this better, let us look at the key differences in a comparison chart.
| Basis for Comparison | Attack Surface Management (ASM) | Vulnerability Management (VM) |
|---|---|---|
| Primary Focus | Discovering all Internet-facing assets (known and unknown). | Scanning known assets for known software flaws (CVEs). |
| Viewpoint | Outside-in (Attacker's perspective). | Inside-out (Defender's perspective). |
| Scope | Broad: Includes unmanaged, orphaned, or shadow IT assets. | Narrow: Limited to assets registered in the internal IT inventory. |
| Action | Inventory creation, asset classification, and monitoring. | Patching, configuration changes, and remediation. |
| Goal | Achieve a complete asset inventory and reduce the external attack surface. | Identify and fix known vulnerabilities on existing assets. |
Also Read: What is Vulnerability Assessment? Process & Tools
Attack Surface Management is a holistic security practice. It includes three main areas, ensuring you manage all parts of your risk. These three areas must work together effectively.
1. External Attack Surface Management (EASM)
External Attack Surface Management (EASM) focuses on assets visible from the public internet. This includes any component an attacker can reach without needing internal access. EASM deals with things you manage and things you do not know you have.
This type of management includes:
EASM's main goal is to monitor for shadow IT. Shadow IT refers to systems and solutions used within your business without the knowledge of the IT or security team.
2. Cyber Asset Attack Surface Management (CAASM)
Cyber Asset Attack Surface Management (CAASM) helps you fix a common problem: fragmented asset data. Your asset data usually sits across many tools. CAASM works by bringing data together from your existing security tools, like inventory, EDR (Endpoint Detection and Response), and CMDB (Configuration Management Database).
The CAASM solution performs the following key functions:
CAASM focuses on internal and managed assets. It ensures you have proper security controls on the things you already track.
3. Digital Risk Protection Services (DRPS)
Digital Risk Protection Services (DRPS) goes beyond your technical assets. It monitors digital channels outside your network that can still harm your business. These threats are often related to your brand, people, or data.
DRPS monitors:
This area is critical because an attack often starts outside your network. Digital Risk Protection ensures attackers cannot use your name or brand against you.
Also Read: What Is Endpoint Detection & Response (EDR) in Cybersecurity?
Attack Surface Management is not a one-time project. It is a continuous, cyclic process that security teams perform regularly. Consistent monitoring reduces the attack surface over time.
The entire process involves four sequential steps.
1. Asset Discovery and Inventory
Attack Surface Management starts by answering a critical question: What exactly do you own and what is exposed?
2. Classification and Contextualization
Once you have discovered the assets, you must determine their value and risk. Classification helps your team prioritize.
3. Risk Assessment and Prioritization
Not all security issues are equal. This step helps you focus your limited time and resources on the most serious problems.
4. Remediation and Monitoring
This final step closes the loop. It is where you take action to reduce your overall risk.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
You might wonder, "Can't my existing tools handle this?" The truth is that the modern digital environment has become too complex for traditional security tools alone.
Complexity of the Attack Surface
The average organization now uses multiple cloud environments and many third-party providers. This creates an attack surface that is volatile, variable, and dynamic.
Identifying Blind Spots
Your security team can only protect what they can see. Traditional tools often focus only on assets that are installed and managed within the corporate network.
Finding the Best Attack Surface Management Tools
Choosing the right Attack Surface Management solution is crucial for your company's defense. The best tools offer several key features. They focus on automation and context.
For example, many large organizations consider Tenable Attack Surface Management and similar platforms. These systems provide the necessary visibility to handle a large, complex attack surface.
The attack surface management approach shifts your security focus from a reactive position to a proactive one. You cannot defend what you cannot see. By fully mapping your digital presence from the outside, you gain the upper hand over potential threats.
Attack Surface Management provides you with complete visibility. It helps you prioritize what matters most—critical assets with severe vulnerabilities. This process ensures that your security budget and team efforts are always focused on eliminating the highest-risk exposures first.
We focus on helping you establish this continuous security cycle. We believe every company deserves a clear, complete, and current view of its risk. Contact us today to discuss how a tailored attack surface management solution can finally give you the confidence to grow your digital business securely.

Based on our discussion, here are five critical points you must remember about Attack Surface Management:
The attack surface includes any digital asset that can be accessed or targeted by an attacker. These include public-facing web applications, open ports, forgotten FTP servers, exposed APIs, cloud services (like Amazon S3 buckets), and leaked credentials found on the dark web.
Attack Surface Management must be a continuous process, not an occasional audit. The digital environment changes constantly. New assets are added daily, and misconfigurations can happen instantly. Therefore, the attack surface management solution should monitor and scan continuously, or at least hourly, to maintain real-time visibility.
ASM reduces risk by minimizing the unknown. By continuously discovering all exposed assets and prioritizing the most critical vulnerabilities on them, your security team can eliminate potential entry points. In other words, it shrinks the area an attacker has to work with.
No, ASM is essential for businesses of all sizes. Even a small company with a simple website and a few cloud services has an attack surface. In fact, smaller companies often use fewer security resources, making the automated discovery of shadow IT and misconfigurations even more critical.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts