
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

Endpoint Detection and Response (EDR) is a cybersecurity technology that continuously monitors endpoint devices, such as laptops, desktops, servers, and mobile or IoT devices, to detect, investigate, and respond to malicious or suspicious activity in real time.
It goes beyond traditional antivirus by using analytics, behavioral monitoring, and automation to identify both known and unknown threats and contain them before they spread across the network.
Every business uses devices like laptops, desktop computers, servers, and mobile phones. These devices, known as endpoints, are often the easiest targets for cyber attackers. You need a strong defense, especially where your data lives and your team works every day.
In this section, we will explore what EDR means, why it is essential, and how it protects your valuable digital assets. Are traditional security tools enough for today's threats? Many organizations are finding the answer is no.
The phrase endpoint detection and response meaning is simple. It refers to a security technology that continuously monitors end-user devices (endpoints) to detect and respond to cyber threats, both known and unknown.
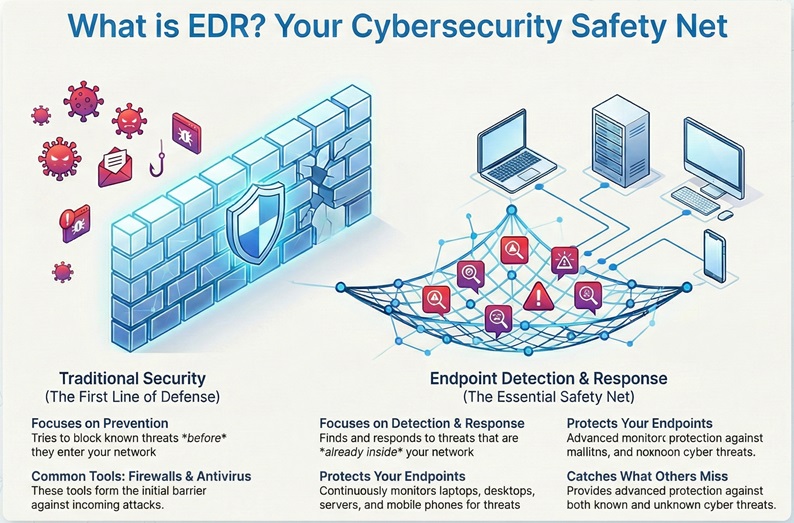
EDR can be understood as an advanced security solution that works after a threat gets past your basic firewall or antivirus program. While traditional security tries to block threats before they enter, EDR systems focus on finding threats that are already inside your network. This means EDR is the essential safety net for your digital world.
Understanding how does endpoint detection and response work reveals its power. The entire system focuses on collecting and analyzing data from your endpoints.
1. The EDR Agent Collects Data
First, you install small pieces of endpoint detection and response software, often called agents, on every device. This agent constantly monitors everything happening on the device.
2. EDR Analyzes the Information
The central EDR system receives the raw data. It then uses advanced analytics and machine learning to quickly examine the information. This analysis process looks for any suspicious activity.
3. Endpoint Detection and Response Reacts
When the EDR system detects a potential threat, it automatically or manually executes a response. This action is swift so as to minimize damage.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
With the emergence of increasingly sophisticated attacks, a traditional antivirus program is no longer enough. You need an endpoint detection and response solution that provides continuous, deep monitoring.
Rise of Fileless and Zero-Day Attacks
Cybercriminals now use new attack methods. Many threats are fileless, meaning they do not drop a malicious file that an old antivirus can spot. Instead, they use legitimate software tools already on your computer.
Continuous Visibility and Context
Endpoint detection and response cybersecurity gives your security team complete visibility. They can see what happened before, during, and after a security event.
While both tools focus on endpoint protection, their approaches and capabilities differ significantly. Let us now discuss the key differences.
| Basis for Comparison | Traditional Antivirus (AV) | Endpoint Detection and Response (EDR) |
|---|---|---|
| Primary Goal | Prevent known malware infections. | Detect and contain unknown, advanced, and persistent threats (APTs). |
| Detection Method | Signature-based matching. It looks for known threat "fingerprints." | Behavioral analysis, machine learning, and threat intelligence. |
| Focus | Prevention before a file executes. | Detection and response after a threat enters or executes. |
| Data Collection | Minimal; often logs only blocked events. | Continuous recording and centralized storage of all endpoint activity. |
| Response Capability | Quarantining or deleting a file. | Isolation, process termination, full investigation, and threat hunting. |
| Level of Visibility | Low; you see what was blocked. | High; you see all activity across the entire network. |
| Best For | Blocking high-volume, common malware. | Combating sophisticated, fileless, and targeted attacks. |
Traditional AV only blocks known threats, leaving you vulnerable. In contrast, EDR is the security layer that assumes a breach will happen and prepares to find and stop it quickly.
Also Read: What is Next-Gen Antivirus (NGAV)? UAE/GCC Trends & Protection
An effective endpoint detection and response EDR system is made up of several key parts that work together to protect you.
1. Data Aggregation and Central Storage
The system collects massive amounts of telemetry data from all your endpoints. This data is nothing but a record of every action on every device.
2. Advanced Analytics and Threat Scoring
This component acts as the brain of the EDR solution. It analyzes the aggregated data.
3. Automated Response and Containment
The response component determines the actions the system takes when it detects a threat. These actions are often automated.
4. Threat Hunting and Forensics
EDR does not just wait for alerts. It provides the tools your security team needs to actively look for threats—a process called threat hunting.
Also Read: Spear Phishing: Learn About #1 CEO fraud
EDR plays a vital role in your overall security posture. It helps you shift from a reactive stance to a proactive one.
Improved Incident Response
When an attack occurs, time is critical. EDR reduces the time it takes to detect and contain a breach. This, consequently, reduces the potential financial and reputational damage.
Compliance and Auditing
Many regulatory frameworks, such as GDPR and HIPAA, necessitate continuous monitoring and clear audit trails.
You might ask, What is the difference between EDR and next-gen antivirus (NGAV)? This is a great question.
While Next-Generation Antivirus (NGAV) uses machine learning to improve prevention, it is still primarily a prevention tool. It tries to block the malicious file before it runs. EDR, on the other hand, is a detection and response tool. It focuses on the continuous monitoring and analysis of activity after a file may have executed.
A complete endpoint detection and response solution often includes the functionalities of NGAV. We can say that EDR encompasses or integrates NGAV features to provide a full-spectrum defense.
When considering an endpoint detection and response solution, you must plan carefully.
You understand now that a modern, aggressive cyber defense requires EDR. It is time to stop worrying about what might happen and start using a solution that tells you exactly what is happening. Your business deserves this level of protection.
Contact our experts today to explore the right endpoint detection and response cybersecurity solution that fits your specific needs and ensures your business remains secure and operational.

Endpoint Detection and Response (EDR) is no longer a luxury; it is a fundamental requirement for business security.
The main benefit is the ability to quickly detect and contain sophisticated threats—especially zero-day and fileless attacks—that traditional antivirus software cannot catch. It significantly reduces the time from attack entry to containment.
While EDR systems collect a lot of data, modern endpoint detection and response solution tools are designed with user-friendly consoles. Managed EDR services are also available. These services allow external experts to monitor and manage the system for you, which is a great option for businesses with smaller IT teams.
Typically, yes. Most comprehensive endpoint detection and response software includes or integrates next-generation antivirus capabilities. You often use the EDR solution to cover both the prevention and the detection/response aspects.
Threat hunting is the proactive search for unknown threats that are lurking undetected in your network. The rich, centralized data collected by EDR technology enables security teams to manually search for suspicious patterns or anomalies that automated tools may have missed.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts