.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Digital services rely on data exchange. Application Programming Interfaces (APIs) facilitate this critical exchange, acting as the communication backbone for modern software, mobile apps, and cloud services. But, as yoaur business grows more interconnected, the attack surface also expands.
This brings us to a crucial question: What is API security and how can you safeguard your valuable assets?
Many organizations build their applications around APIs. While this drives rapid innovation, it also introduces significant API security risks if not properly managed. An insecure API can open the door for data breaches, service disruptions, and financial loss.
You need a strong defense for these digital pipelines. In this guide, we will explore the fundamentals of API security. We will explain the essential components and detail the steps your organization must take to protect its data and maintain customer trust.
Let us start with a clear definition. API security refers to the comprehensive set of practices, tools, and processes designed to protect APIs from threats and vulnerabilities. API security ensures that only legitimate users and systems can access your APIs. It also makes certain that they only access the specific resources they are allowed to use.
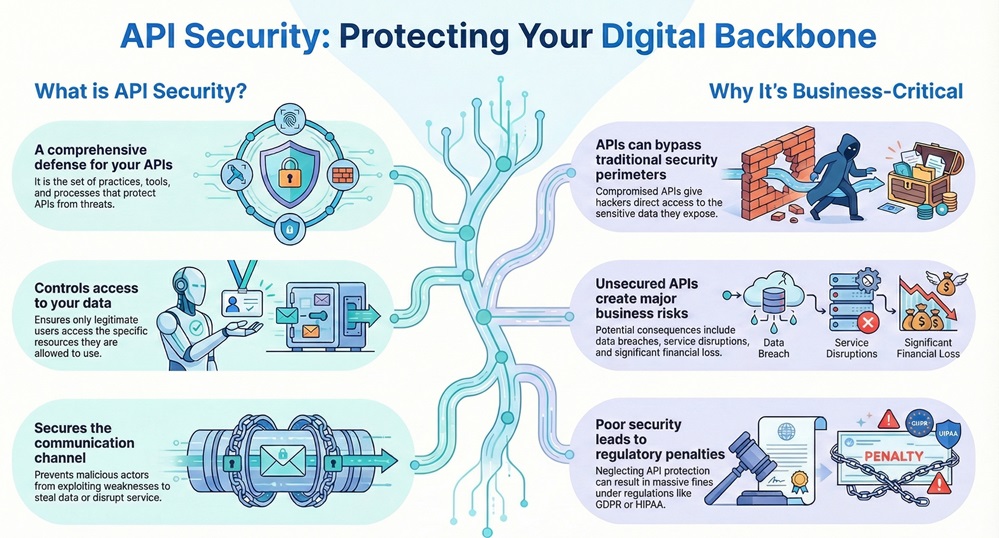
A secure API prevents malicious actors from exploiting weaknesses in the communication channel. This protection is essential for data protection and for maintaining the availability of your digital services.
Your Security Matters Reach FSD-Tech
Today, nearly all digital services rely on APIs. Consider the vast amount of sensitive information—like financial records, personal data, and business secrets—that passes through these interfaces every second. This flow is precisely why API security is important.
If a hacker compromises an API, they can bypass traditional perimeter security. They can access the very data the API exposes. API security plays a vital role in preventing these critical breaches. Furthermore, neglecting proper security can lead to massive fines under regulations like GDPR or HIPAA.
In simple words, if your business uses APIs, protecting them is non-negotiable.
Also Read: What is Phishing Simulation? Benefits & Best Practices
A strong API security process relies on several interconnected components. Each element addresses a specific vector of attack.
1. Authentication and Authorization
Effective API security starts with knowing who is accessing your system and what they are allowed to do.
Authentication: Verifying Identity
Authentication is nothing but the process of verifying a user's or system's identity. Strong API security requires robust authentication methods.
Examples of common authentication methods include:
Authorization: Defining Permissions
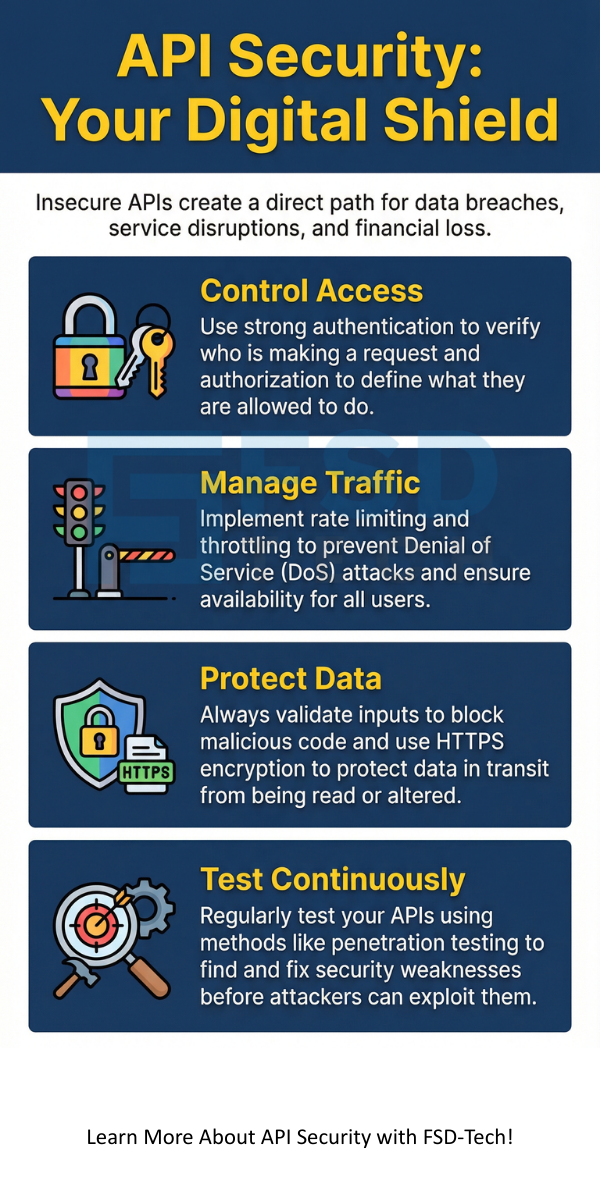
Once the system authenticates the user, authorization determines their access level. API security must implement granular authorization. This means a user who can read a customer record cannot necessarily delete it. Authorization ensures that users only perform actions they are permitted to do.
2. Rate Limiting and Throttling
A common attack involves overwhelming an API with requests. This is called a Denial of Service (DoS) attack. API security uses rate limiting to prevent this.
Rate limiting restricts the number of requests a single user or IP address can make over a specific period. Throttling is a similar technique. It controls resource usage by reducing the processing speed for excessive requests. This action helps maintain service availability for all legitimate users.
3. Input Validation
Many vulnerabilities arise from accepting and processing unexpected data. Input validation is a crucial defensive measure in API security.
You must validate all data that enters your API. The validation process checks if the data:
This step prevents severe issues like SQL injection or Cross-Site Scripting (XSS) attacks.
4. Encryption
Data must remain secure while it travels between the client and the server. API security requires strong encryption.
You should always use HTTPS (Hypertext Transfer Protocol Secure). HTTPS ensures all communication is encrypted using Transport Layer Security (TLS). This action prevents attackers from reading or tampering with the data in transit.
Also Read: Zero Day Attack: How It Works & Prevention Guide
Regular testing is the only way to confirm your defenses work. What makes API security testing critical is the simple fact that software code contains flaws, and these flaws lead to vulnerabilities.
Development teams frequently introduce new features and updates. Each change can inadvertently create a new security weakness. Therefore, you must make testing a continuous part of your development lifecycle.
Testing API security involves using a structured approach that checks for common and complex vulnerabilities.
1. Static and Dynamic Application Security Testing (SAST and DAST)
2. Penetration Testing
Penetration testing is a simulated cyber-attack against your system. Security experts attempt to exploit vulnerabilities to gain unauthorized access. This type of API security assessment provides a realistic view of your security posture.
3. Fuzz Testing
Fuzz testing involves feeding a large amount of random or malformed data into the API inputs. If the API crashes or behaves unexpectedly, it indicates a potential vulnerability that an attacker could exploit.
Organizations often use specialized tools to manage and secure their APIs. Two primary tools in this context are the API Security Gateway and the dedicated API Security Platform.
Comparison Chart: Gateway vs. Platform
| Basis for Comparison | API Security Gateway | API Security Platform |
|---|---|---|
| Primary Function | Acts as a single entry point for all API calls. | Provides continuous monitoring, analysis, and threat detection. |
| Key Capability | Authentication, Rate Limiting, Protocol Translation. | Behavior analysis, Bot detection, API-specific attack prevention. |
| Placement | Deployed in-line; sits directly in the path of traffic. | Typically deployed out-of-band; monitors traffic copies. |
| Focus | Traffic Management and basic policy enforcement. | Threat Detection and deep security analysis. |
| Security Depth | Enforces basic security rules (e.g., valid token presence). | Analyzes payload and context to detect complex logic flaws. |
The API security gateway is a critical component. It sits between the client and the backend services. It acts as a single point of enforcement for security, governance, and management policies.
What can the gateway do? It performs:
However, a gateway often only performs simple security checks. It generally cannot detect complex attacks that exploit business logic.
Also Read: What is Credential Stuffing? Detection and Prevention
An API Security Platform is a newer, dedicated tool. It focuses on deep analysis of API traffic. It works on the principle of API security scanning. This means it analyzes the behavior of clients over time.
This platform uses machine learning to understand the "normal" behavior of your API. If a client suddenly starts making thousands of requests that exploit a specific business function, the platform detects this anomaly. It is designed to defend against the OWASP API Security Top 10 risks, such as Broken Object Level Authorization (BOLA).
Securing your APIs requires a commitment to best practices across your development and operations teams. Let us now outline strong API security guidelines.
1. Adopt a Security-First Development Approach
You must shift security left in the development lifecycle. API security should be part of the design and coding phase, not an afterthought. Perform threat modeling on every new API design. Threat modeling helps identify potential attack vectors before you write any code.
2. Use Strong Authentication and Authorization Standards
Avoid simple API key usage alone. How API key works is that it is often sent in the header of the request. If an attacker intercepts this key, they can impersonate the client.
You should implement OAuth 2.0 or OpenID Connect for user-facing APIs. For service-to-service communication, use mutual TLS (mTLS) or short-lived JSON Web Tokens (JWTs). Remember to secure your keys. API key security best practices include:
3. Implement Robust Rate Limiting
Define strict rate limits for all API endpoints. Use different limits based on user roles and the sensitivity of the resource. For example, a user requesting a login page may have a higher limit than a user trying to download a full database report.
4. Patch and Update Regularly
Your APIs rely on underlying operating systems, frameworks, and libraries. Attackers constantly search for vulnerabilities in older software versions. You must maintain a regular patching schedule. This action prevents the exploitation of known, fixed vulnerabilities.
5. Monitor and Audit All API Traffic
You need full visibility into who, what, and when a user accesses your APIs. Implement comprehensive logging and monitoring. The logging system should capture:
Analyze these logs for suspicious activity. Look for unusual patterns, such as a sudden increase in error codes or failed authorization attempts.
6. Plan for Incident Response
Even the best defenses can fail. You must have a clear API security process for responding to a breach or a denial-of-service attack. This plan should include steps for:
You now understand that a strong API security strategy is the foundation for trust and innovation. Businesses that treat API security as a top priority protect their customers, their intellectual property, and their reputation.
We are committed to helping you build and maintain secure, reliable digital infrastructure. Protect your APIs today and secure your business future. Contact us to discuss your current API security assessment and discover how our solutions ensure your data remains protected against the latest threats.
The shift to an API-driven economy means that securing these interfaces is no longer a niche concern. It is a core business necessity. To ensure the safety of your data and the reliability of your services, you must remember these points:
A WAF focuses on protecting web applications from common attacks like SQL injection and XSS. An API Gateway manages and secures API traffic, handling authentication, routing, and rate limiting. While a WAF protects the entire web app, a gateway specifically secures the API layer. Many modern WAFs now include features to address API-specific threats.
While a single global API security certification does not exist, developers follow several standards. The OWASP API Security Top 10 is the most widely recognized document. It defines the top security risks specific to APIs. Compliance with industry standards like PCI DSS (for financial data) or SOC 2 often requires robust API security practices.
Attackers often target flaws in authorization. For example, in a BOLA attack, an attacker changes the ID of a resource they are requesting (e.g., changing user/123 to user/456). If the API fails to check if the attacker is authorized to access resource 456, the attack succeeds. This action allows unauthorized data access.
You can use existing tools for general security. However, dedicated API security tools are necessary. Traditional security solutions often see API traffic as simple web traffic. They fail to understand the complex business logic that makes APIs vulnerable.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts