
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

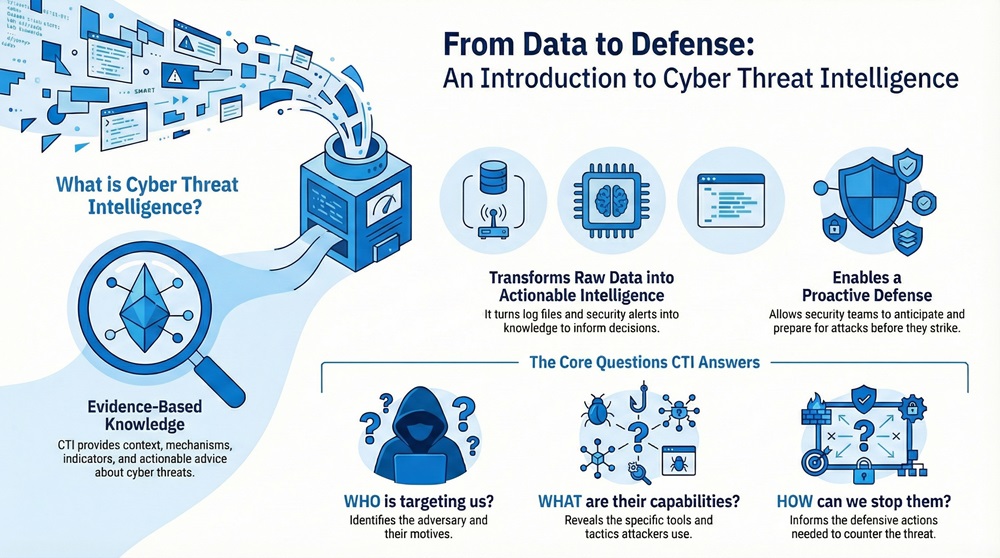
Cyber Threat Intelligence (CTI) plays a critical role in protecting your digital world. Many organizations struggle to keep up with the constant attacks they face. But what if you could know what the attackers are planning before they strike? This is exactly where CTI comes in, giving you the knowledge you need to build a stronger defense.
Cyber Threat Intelligence is nothing but the organized, analyzed, and refined information about current or potential threats and adversaries. Simply put, CTI provides context for cyber incidents. It transforms raw data—like log files, attack indicators, or security alerts—into actionable knowledge. This knowledge helps you make informed decisions to prevent or quickly respond to cyberattacks.
The need for effective CTI is growing every day. Why does this information matter so much? Because every organization, from a small business to a large corporation, faces a constant barrage of threats. Cyber Threat Intelligence ensures that your security teams move from simply reacting to threats to actively predicting and preparing for them.
Cyber Threat Intelligence (CTI) can be understood as evidence-based knowledge. This knowledge includes context, mechanisms, indicators, implications, and actionable advice about an existing or emerging cyber threat. The goal is to inform decision-making concerning the subject's response to that threat.
CTI focuses on the 'who,' 'what,' and 'how' behind a cyberattack. It moves beyond just recognizing a virus signature or a malicious IP address. Instead, CTI answers:
In simple terms, Cyber Threat Intelligence converts data into information, and then converts that information into intelligence that offers value for security operations.
Now, the question arises: why cyber threat intelligence is important for your business? The importance of CTI stems from the constantly changing threat landscape. Attackers are becoming more sophisticated and their methods are constantly changing.
Cyber Threat Intelligence plays a vital role because it provides proactive defense. It helps security teams prioritize the thousands of alerts they receive every day.
Without Cyber Threat Intelligence, a security team is essentially fighting blind. With CTI, they gain the necessary vision to anticipate and mitigate the threats that truly matter.
The raw data collected—such as IP addresses, file hashes, or domain names—is not intelligence on its own. It becomes intelligence only after rigorous analysis. What is cyber threat intelligence analysis?
Cyber Threat Intelligence analysis is the process of examining raw data, putting it into a business context, and drawing conclusions that are actionable for security teams and leadership. This process often follows the intelligence cycle.
This analysis helps in transforming noisy data into quiet, useful insights. The output of this analysis is the intelligence report itself.
This deep dive into the data is what truly separates useful intelligence from simply a list of bad indicators.
Also Read: Threat Modeling in Cyber Security - Process, STRIDE & Benefits
How does threat intelligence work in practice? The entire process is continuous and systematic, following a well-defined cycle. This intelligence cycle ensures that the output is relevant, timely, and supports the organization's goals.
The Cyber Threat Intelligence process typically involves four main steps:
1. Planning and Direction
This is the first step. The process starts with asking the right questions. What are your organization’s most critical assets? Which threats pose the greatest risk to your business operations?
2. Collection
The collection phase involves gathering raw data from diverse sources. These sources include open-source feeds, commercial CTI platforms, technical sensor data from your network, and even information gathered through the dark web.
3. Processing and Analysis
As discussed, this is the core phase. Raw data collected is processed—cleaned, de-duplicated, and formatted—to prepare it for analysis.
4. Dissemination and Feedback
The intelligence must reach the right people at the right time. This is the final step.
This systematic approach guarantees that the output is not just data, but actionable knowledge that aids in defense.
Also Read: Unified Threat Management (UTM): Key Security Functions
Cyber Threat Intelligence is not a one-size-fits-all product. It is delivered in different types, or levels, each serving a specific audience and purpose within an organization. Understanding these types of cyber threat intelligence is essential for proper utilization.
We can generally categorize CTI into three main types: Strategic, Tactical, and Operational.
Strategic Cyber Threat Intelligence is high-level, long-term intelligence. What is strategic cyber threat intelligence? It is non-technical intelligence aimed at decision-makers, such as the Board of Directors and senior management.
Operational Threat Intelligence sits in the middle. It focuses on the details of upcoming attacks or ongoing campaigns. It provides details on Tactics, Techniques, and Procedures (TTPs) used by specific threat actors.
Tactical Threat Intelligence is the most technical and short-lived type. It comprises easily collectible data points, mainly Indicators of Compromise (IoCs).
The table below contrasts these three types of cyber threat intelligence.
| Basis for Comparison | Strategic Threat Intelligence | Operational Threat Intelligence | Tactical Threat Intelligence |
|---|---|---|---|
| Audience | Executives, Board of Directors, CIOs | Security Managers, Incident Responders | SOC Analysts, System Administrators |
| Focus | Adversary intent, High-level risk, Motives, Geopolitics | Adversary TTPs, Attack Campaigns, Tools used | IoCs (IPs, Hashes, Domains), Immediate threat data |
| Time Horizon | Long-term (Months to Years) | Medium-term (Weeks to Months) | Short-term (Days to Hours) |
| Purpose | Inform security strategy, Budget decisions, Risk management | Prepare for specific attacks, Improve detection logic | Block immediate threats, Automated defense |
| Format | White papers, Executive summaries, Briefings | Analyst reports, TTP deep dives, Technical bulletins | Feeds of IoCs, Alerts, Watchlists |
Cyber Threat Intelligence is a powerful tool that applies to almost every aspect of security. Understanding the various cyber threat intelligence use cases helps organizations maximize the value they gain from their CTI system.
1. Enhancing Security Monitoring and Detection
This is a primary use case. Your existing security tools, like your SIEM (Security Information and Event Management) system, constantly generate alerts.
2. Improving Vulnerability Management
You likely have thousands of vulnerabilities in your environment. You cannot patch them all at once.
3. Driving Incident Response
When an attack occurs, time is critical. CTI is essential for a quick and informed response.
4. Performing Proactive Threat Hunting
Threat hunting is the active search for threats that may have bypassed your initial defenses.
5. Informing Strategic Security Planning
As mentioned, CTI provides the necessary input for executive decisions.
Also Read: What is Social Engineering? Types, Examples & Prevention
A Cyber Threat Intelligence solution or system is the technology platform used to automate the entire intelligence cycle. These solutions comprise tools, software, and services that aggregate, analyze, and disseminate CTI at scale.
A comprehensive cyber threat intelligence system generally includes the following features:
Using a dedicated CTI solution is vital for any large organization. It makes sure the intelligence is consumed automatically, enabling a machine-speed defense, which is necessary to counter the speed of modern attacks.
All in all, Cyber Threat Intelligence (CTI) is the essential foundation for modern security. It effectively transforms raw, overwhelming data into actionable knowledge across all organizational levels. By understanding the three types—Strategic, Operational, and Tactical—you ensure that executives, analysts, and responders receive tailored insights.
CTI plays a vital role in proactive defense, enabling prioritization of vulnerabilities and faster incident response. It permits your teams to predict and prepare for attacks, rather than just reacting to them.
Thus, implementing a robust cyber threat intelligence system allows you to gain a necessary edge against sophisticated adversaries.
Start CTI Defense Contact FSD-Tech today
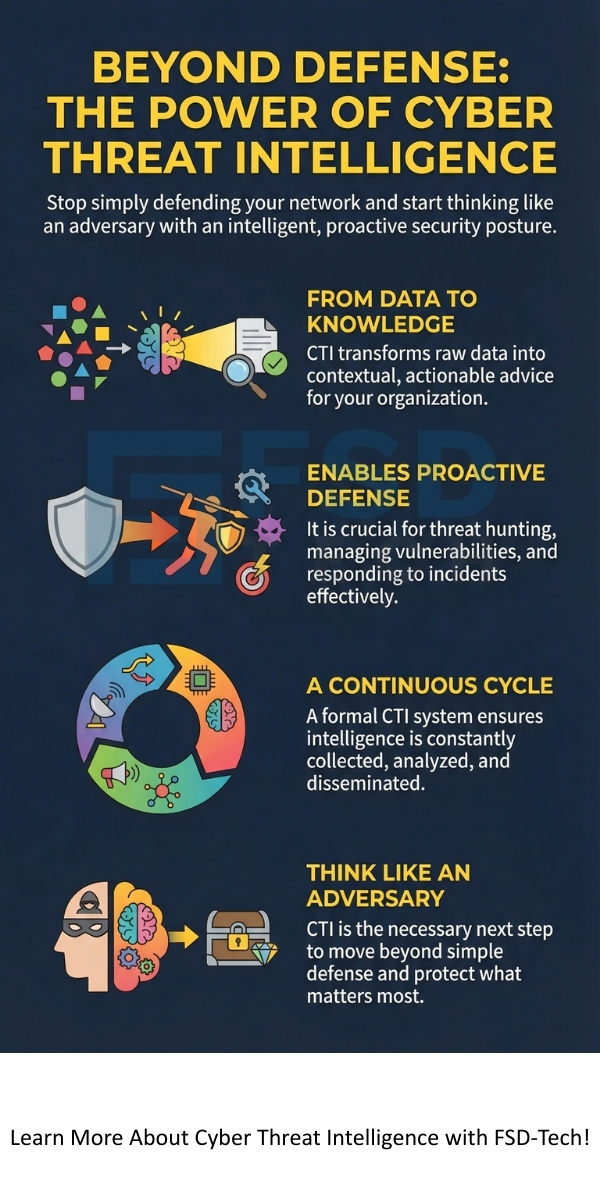
So, with the above discussion, we can say that Cyber Threat Intelligence is no longer optional; it is a fundamental requirement for modern security. It empowers your organization to move beyond a simple reactive defense to an intelligent, proactive security posture.
CTI is processed and analyzed information. It provides context and action. Raw data, like a server log or an IP address, is just a fact without meaning. CTI transforms the IP address into a threat actor's command-and-control server, making it an actionable insight.
Everyone in the security department uses CTI. Executives use Strategic CTI for budgeting, Incident Responders useOperational CTI for attack analysis, and SOC Analysts use Tactical CTI for real-time blocking.
No single tool or system can prevent every attack. CTIplays a vital role in proactive defense. It significantly reduces the probability of a successful breach and minimizes the impact of an attack if one does occur. It enables informed action, which is the best form of prevention.
CTI originates from many sources. These include open-source intelligence (OSINT) from public reports, technical intelligence from network sensors, human intelligence (HUMINT) from experts and forums, and commercial feeds from specialized security vendors.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts