
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

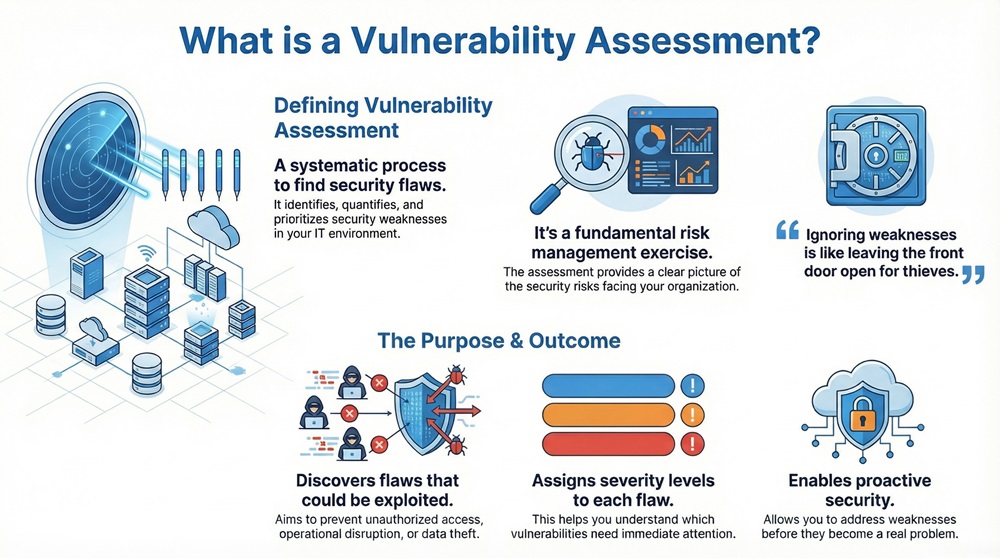
When you secure your business, you must know what weak points an attacker might exploit. Ignoring these weaknesses is like leaving the front door open for thieves. This is where a vulnerability assessment comes into play. It is nothing but a systematic process you use to identify and measure security flaws in your computing systems and networks.
A vulnerability assessment solution provides you with a clear picture of the risks facing your organization. It allows you to prioritize and address security weaknesses before they become a real problem. We will now explore this essential cybersecurity process, its stages, and how it differs from other security methods.
Vulnerability assessment refers to the process of identifying, quantifying, and prioritizing the security weaknesses (vulnerabilities) in a system or network. This is essentially a risk management exercise.
Vulnerability assessment can be understood as an exhaustive examination of your IT environment. The process aims at discovering flaws that an attacker could exploit to gain unauthorized access, disrupt operations, or steal sensitive data. The assessment assigns severity levels to these flaws, helping you understand which ones need immediate attention.
Start Vulnerability Assessment
Vulnerability assessment is important because it actively safeguards your digital assets. You perform this process to minimize the attack surface of your organization.
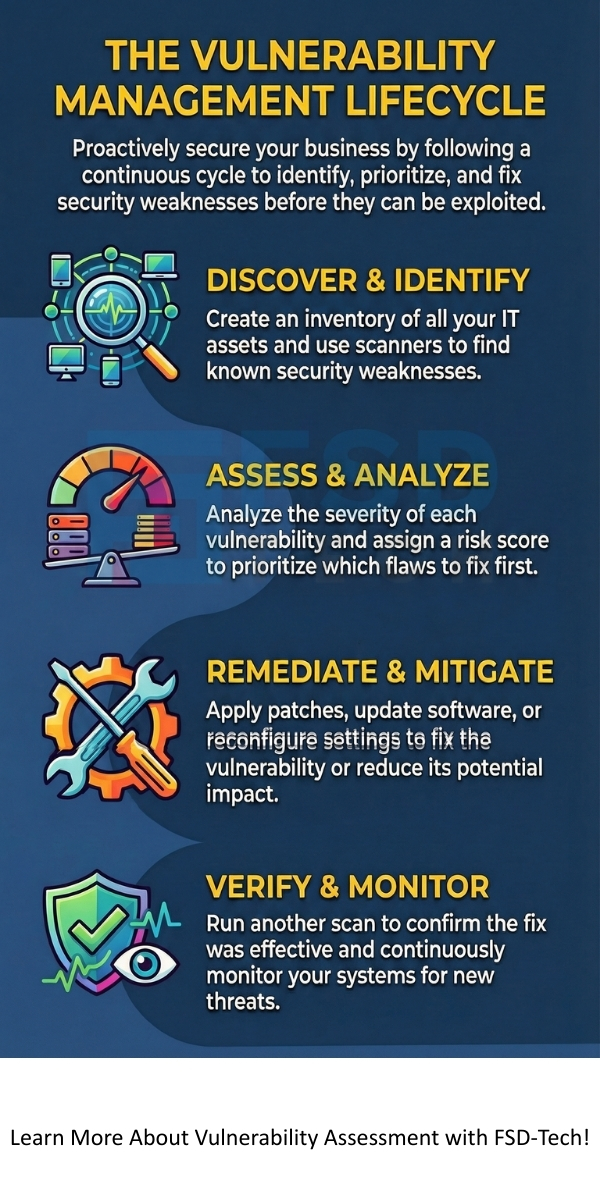
A vulnerability assessment is not a one-time event; it is part of a continuous process called the vulnerability management lifecycle. This lifecycle ensures that you identify, fix, and continuously monitor your systems for new weaknesses.
The vulnerability management lifecycle comprises four main stages:
1. Discovery and Identification
In this initial stage, you map out your entire IT landscape. You must identify all assets in your network.
2. Assessment and Analysis
Once you discover the vulnerabilities, you need to determine their significance.
3. Remediation and Mitigation
This is where you act to fix the problems. The goal here is to remove or reduce the risk.
4. Verification and Monitoring
After fixing the issues, you must confirm that the remediation was effective.
Also Read: What Is Endpoint Detection & Response (EDR) in Cybersecurity?
Performing an effective vulnerability assessment requires a clear, structured approach. You follow a systematic breakdown to ensure you cover all crucial areas.
1. Scope Definition
First, you clearly define what systems and networks the vulnerability assessment will cover.
2. Tool Selection and Deployment
The right vulnerability assessment software is essential for an accurate scan.
3. Running the Scans
This stage involves actively scanning the target environment.
4. False Positive Filtering
The scan results often include false alarms, called false positives.
5. Risk Scoring and Prioritization
You apply a risk scoring methodology to the validated vulnerabilities.
6. Vulnerability Assessment Report Generation
Finally, you document all findings, analysis, and recommendations in a clear, concise document.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
A common point of confusion is the difference between a vulnerability assessment and penetration testing. While both are security processes, they serve different, but complementary, purposes. They are often bundled together as vulnerability assessment penetration testing (VAPT).
The core difference lies in their approach and goal.
| Basis for Comparison | Vulnerability Assessment | Penetration Testing |
|---|---|---|
| Purpose | Identify and quantify all known security weaknesses. | Actively exploit weaknesses to demonstrate the potential impact. |
| Approach | Quantitative and comprehensive; a broad scan. | Qualitative and focused; a deep dive into specific targets. |
| Methods | Automated scanners and checks against known lists. | Manual techniques, hacking tools, and creative attack scenarios. |
| Output | A list of vulnerabilities with assigned risk scores. | Proof of concept showing a system breach and the resulting impact. |
| Goal | To create a comprehensive list for remediation. | To validate defenses and measure the potential damage from a real attack. |
| Analogy | A doctor's checkup to find potential health problems. | An invasive surgery to fix a specific, confirmed problem. |
Vulnerability assessment provides the breadth—it tells you every weakness you have. Penetration testing provides the depth—it shows you which weaknesses an attacker can actually use to break in. You often use the results of the assessment to guide the testing.
When you conduct a vulnerability assessment in cyber security, you focus on different areas of your organization's IT infrastructure. The different types of assessments ensure you cover every potential point of attack.
Also Read: Zero Day Attack: How It Works & Prevention Guide
Effective vulnerability management requires you to follow a few key principles and use the right vulnerability assessment tools.
Numerous tools are available to help you perform an effective assessment. These tools greatly simplify the discovery and identification stages.
| Tool Name | Type of Assessment | Primary Function |
|---|---|---|
| Nessus | Network, Host, Application | Comprehensive vulnerability scanning and reporting. |
| OpenVAS | Network, Host | An open-source, full-featured vulnerability scanner. |
| Qualys Cloud Platform | All Types | Cloud-based platform for vulnerability and compliance management. |
| Wireshark | Network | Network protocol analyzer for deep packet inspection. |
You must view a vulnerability assessment not as an expense, but as a critical investment in your operational resilience. This systematic process ensures you proactively identify and prioritize system weaknesses, stopping threats before they compromise your data.
By implementing the continuous vulnerability management lifecycle and utilizing modern vulnerability assessment software, you maintain a secure posture. This commitment allows you to focus resources on the high-risk flaws highlighted in the vulnerability assessment report. Take decisive action now; secure your digital environment today and guarantee the safety and continuity of your business operations.
Do you have questions about which vulnerability assessment solution fits your organization's unique needs? Contact our expert cybersecurity team today. We provide comprehensive assessments to ensure your systems remain secure and resilient against the ever-growing threats in cyber security.
A vulnerability assessment is an essential part of a modern cybersecurity strategy. It serves as your organization's security health check, ensuring you identify all points of failure.
The purpose of vulnerability assessment is to identify, analyze, and document security flaws in your systems and applications. It aims at providing you with the necessary information to remediate the flaws before an attacker can exploit them, thereby proactively reducing your organization's overall risk.
Vulnerability management is the entire cyclical process of identifying, classifying, prioritizing, remediating, and mitigating vulnerabilities. The vulnerability assessment is a critical, initial part of this larger, ongoing program.
The vulnerability assessment report typically includes a high-level executive summary, a detailed list of all identified vulnerabilities, the severity rating for each flaw (high, medium, low), the potential business impact, and specific technical recommendations for remediation.
This depends on the goal. In a black box assessment, the assessor has no prior knowledge of the internal system, which mimics an external attacker. A white box assessment, on the other hand, gives the assessor full system details, allowing for a much deeper and more comprehensive check for flaws, resulting in a more thorough vulnerability assessment solution.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts