
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Do you worry about proving something online without giving away too much personal information? Perhaps you need to verify your age, but you do not want to share your birth date. Maybe you want to confirm a transaction is legitimate without revealing the financial amount. This delicate balance between privacy and verification presents a significant challenge in the digital world.
Zero Knowledge Proof (ZKP) technology offers a powerful solution to this problem. The main purpose of zero knowledge proof is simple. It allows one party to prove a statement is true to another party without revealing any details about the statement itself. You gain the power to prove a fact without exposing the secret information that makes the fact true. This technological method ensures your private data stays private.
In this comprehensive guide, let us explore how zero knowledge proof works.
We will discuss its core elements, its vital role in digital security, and the many zero knowledge proof applications that are quickly reshaping the digital world. This is essential knowledge if you value your privacy.
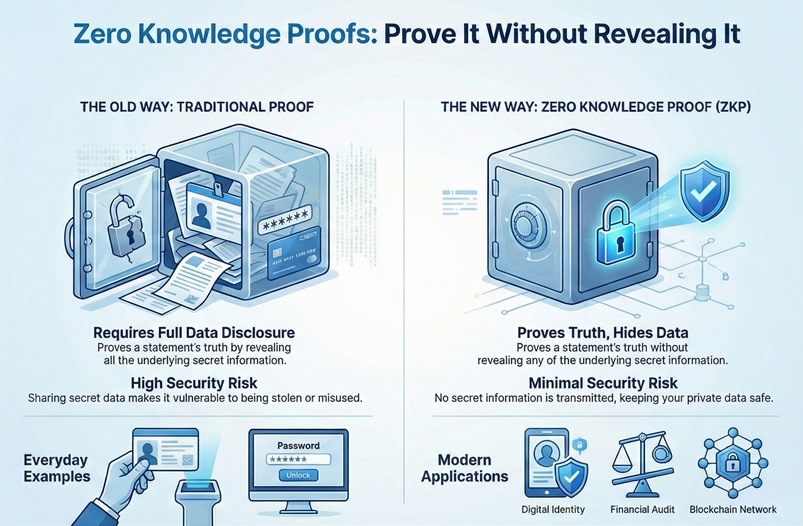
To understand the immense value of zero knowledge proof, let us first compare it with the traditional methods you use every day. Traditional methods require you to disclose the underlying data for verification. Zero knowledge proof removes this need completely.
| Basis for Comparison | Zero Knowledge Proof (ZKP) | Traditional Proof |
|---|---|---|
| Purpose | Proves the truth of a statement without revealing the underlying data. | Proves the truth of a statement by revealing all underlying data. |
| Data Disclosure | Zero information is shared about the secret. | Full information is disclosed to the verifier. |
| Verification Method | Relies on mathematical and cryptographic protocols (e.g., challenges and responses). | Relies on direct inspection of the evidence (e.g., a password or document). |
| Security Risk | Minimal risk, as no secret information is transmitted or stored. | High risk, as sharing the secret makes it vulnerable to theft. |
| Ideal Use | Identity verification, financial audits, and blockchain zero knowledge proof systems. | Login with password, showing an ID card, or submitting a full report. |
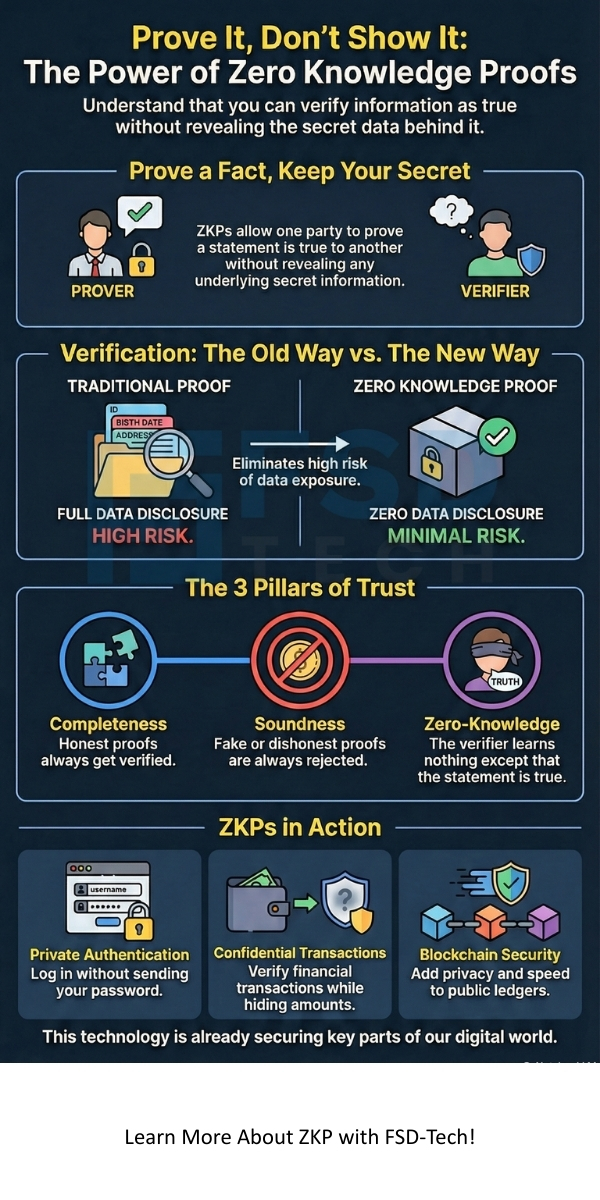
A zero knowledge proof can be understood as a cryptographic protocol. This protocol involves two parties: the Prover and the Verifier. The Prover aims to convince the Verifier that a specific statement is true. Meanwhile, the Verifier must become convinced of this truth. The critical requirement is that the Verifier learns nothing more than the fact that the statement is true.
The statement itself is often referred to as a "secret" or "witness."
For instance, the secret might be the password to a specific account. The Prover knows the password and wants to prove it without typing the password itself. The zero knowledge proof makes this action possible. This technological method is based on rigorous mathematical principles.
Any system claiming to use a zero knowledge proof must satisfy three distinct properties. These properties ensure the mechanism is reliable and maintains privacy.
This triple requirement defines the reliability and main purpose of zero knowledge proof.
The fundamental main purpose of zero knowledge proof centers on enhanced privacy and security. Digital systems require users to prove ownership or membership constantly. Historically, this meant sharing your sensitive information with a third party.
Zero knowledge proof minimizes the need for trust. Instead of trusting a system to keep your secrets safe, you simply never give them your secrets in the first place. You only provide cryptographic certainty of a fact.
What is the purpose of zero knowledge proof? It primarily solves the problem of data over-sharing. Let us consider an example. A company requires a user to prove they are over 18 years old. Using a traditional method, the user shares their entire driver’s license. This document contains their full name, address, and exact date of birth. Using a zero knowledge proof, the user only proves the one necessary fact: their age is greater than 18. This approach limits data exposure, which plays a vital role in preventing fraud and identity theft.
Zero knowledge proof facilitates transactions and interactions that were once too risky due to data leakage. This technology makes secure, private interactions possible on open networks.
Also Read: What is Cloud Virtual Private Network (VPN)?
A zero knowledge proof of knowledge specifically demonstrates that the Prover knows a piece of information, or "witness," which satisfies a certain mathematical relationship. This involves a subtle yet complex interaction between the Prover and the Verifier.
The process typically follows a three-step sequential pattern. Let us understand this process using the common example of proving you know the combination to a safe.
The process repeats multiple times with different challenges. Due to the soundness property, if the Prover successfully answers the random challenges repeatedly, the Verifier becomes statistically certain that the Prover truly possesses the secret. The Verifier still cannot determine what the secret is. The Verifier learns nothing but the truth of the statement.
This step-by-step method ensures the integrity of the zero knowledge proof of knowledge system.
The intersection of zero-knowledge proofs in blockchain is a key development for modern decentralised systems. Blockchain technology’s inherent design means all transactions and data are transparent and public. This transparency conflicts directly with the need for individual privacy.
Blockchain zero knowledge proof technology provides a solution by allowing public verification without public disclosure. Consider a voting system built on a blockchain. The system must verify that you are an eligible voter. The system must also verify that you have not voted twice. The system should not link your vote to your identity.
The zero-knowledge proof enables the network to process and verify transactions without revealing the details of those transactions. The proof itself becomes the data recorded on the public ledger.
Also Read: What is Zero Trust Security Model? All You Need to Know
The integration of blockchain zero knowledge proof technology is enabling the next generation of private, scalable decentralized applications (dApps).
Let us look at the core distinctions between the goals of traditional cryptographic systems and zero knowledge proofs. Traditional methods focus mainly on securing data transmission and storage. Zero knowledge proof focuses on secure data interaction.
Also Read: What is Sandboxing in CyberSecurity? How It Works?
The practical uses for zero knowledge proof applications span across several industries, ensuring better security and compliance.
1. Private Authentication and Identity
You often use a password to prove your identity. The problem is that the service provider stores a hashed version of your password. If their database is hacked, your password hash is vulnerable.
A zero knowledge proof allows you to prove you know the password without ever sending the password or the hash to the server. The main purpose of zero knowledge proof in this area is to eliminate the need for storing or transmitting user credentials. This greatly improves user security.
2. Confidential Transactions
In finance, particularly within blockchain zero knowledge proof systems, ZKP enables confidential transactions. Companies need to prove they have the funds for a transaction without revealing their entire balance sheet. The proof confirms the transaction is valid according to the protocol rules. The proof hides the monetary values involved.
3. Compliant Auditing
Auditors need to verify that a company’s financial statements or internal processes meet all necessary regulations. However, the company must also maintain the confidentiality of proprietary business information. A zero knowledge proof allows the company to prove compliance with an audit trail without revealing competitive trade secrets. The proof itself serves as the verified document.
4. Zero Knowledge Proof for Wallets
A specific example involves digital wallets. The main purpose of zero knowledge proof ari wallet integration (or similar privacy-focused wallets) is to enable secure key management and transactions.
These zero knowledge proof applications collectively focus on a single goal: creating a web where you control your own data.
The zero knowledge proof concept represents a major step forward in digital privacy and security. It offers a solution to the ongoing conflict between the need for transparency and the desire for confidentiality. By satisfying the three properties of completeness, soundness, and zero-knowledge, this technology ensures that you can operate securely in digital environments without sacrificing your most sensitive data.
Zero knowledge proof applications are expanding rapidly, from private user authentication to the secure processing of blockchain zero knowledge proof transactions. As we move further into a world of decentralized systems, this technology will play an ever more essential role in securing your personal and financial information. This powerful cryptographic tool empowers you to take back control of your data.
We are committed to providing you with the knowledge and tools necessary to navigate this complex digital world. We focus on empowering our clients with cutting-edge solutions that respect privacy and demand security. Choose solutions that implement zero knowledge proof today, and strengthen your digital future.
Worried About Data Exposure? Reach us for immediate help
Now, the question arises about the common misunderstandings of this powerful technology. Let us clarify some key points.
The primary purpose is to enable one party to prove the truth of a statement to another party without revealing the information that confirms the statement. In simple terms, it facilitates trustless verification, meaning you do not need to trust the Verifier with your secret.
Zero knowledge proof in blockchain is a cryptographic method used to increase both privacy and scalability. It allows network participants to confirm that a transaction is valid without knowing the details of the amount, the sender, or the recipient. This helps in building private and fast decentralized networks.
Yes, the information itself is completely hidden from the Verifier. The Verifier only learns the validity of the statement derived from the hidden information. The zero-knowledge property ensures that the Verifier cannot use the proof to deduce the secret.
No. The concept of zero knowledge proof was first introduced by MIT researchers in the 1980s. However, recent advances in computing power and mathematics have allowed for the creation of practical and efficient zero knowledge proof applications that are being deployed today, especially in the blockchain space.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts