
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

Do you worry about malware and strange files harming your computer? In today's digital world, new threats constantly try to infiltrate your system. You need a powerful defense mechanism to examine these suspicious items without risking a system breach. This is where sandboxing in cyber security steps in.
Sandboxing refers to a crucial security technology. It ensures your system remains safe even when you interact with untrusted code or files. We will thoroughly explore this essential technique. You will learn precisely what it is, how it works, and why experts call it a vital tool for modern defense.
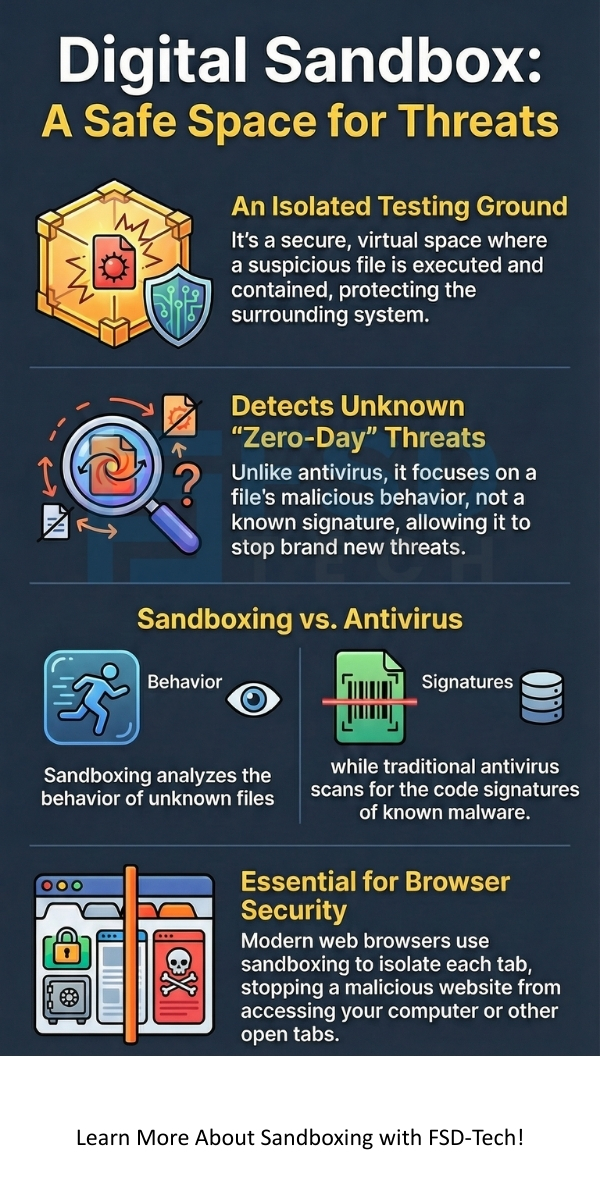
Sandboxing can be understood as an isolated testing environment. This secure space allows you to run untrusted programs or open suspicious files without risking damage to your main operating system or the underlying network. Think of it like a child's sandbox: the activity stays contained within the boundaries, protecting the surrounding area.
In simple terms, sandboxing provides a distinct, isolated container. The potentially malicious code inside this container cannot see, access, or modify resources outside of its defined boundary. This segregation is fundamental to effective security. Sandboxing security focuses on minimizing the potential damage a threat can cause.
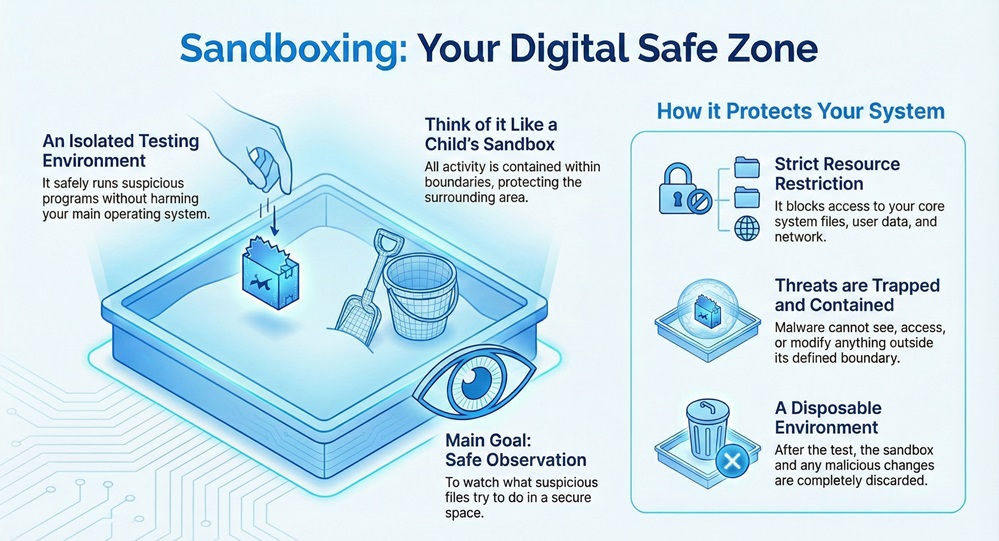
What is the main goal of using a security sandbox? The main goal is to safely observe the behavior of potentially harmful content. By watching what a suspicious file tries to do in this safe space, security systems can then determine if the file is truly malicious.
The sandbox meaning in computing refers to a specific, protected execution environment.
This environment simulates a user’s actual operating environment, but it strictly controls and limits what the program inside can do. A sandbox restricts access to core system files, user data, network resources, and peripheral devices. This separation ensures that even if a piece of malware runs, it remains trapped and cannot spread.
A sandbox environment is nothing but a temporary, disposable virtual machine or an equivalent isolated space. When the test finishes, the system discards the sandbox, along with any malicious changes the program may have made. This process completely eliminates the threat without affecting your actual system.
Sandboxing in browser security is one of the most common applications you use daily.
A modern web browser, such as Chrome or Firefox, runs each website or browser tab in its own sandbox. This feature prevents a malicious website from accessing data or files belonging to another website or, more importantly, your local computer.
For example, if you visit a compromised website, the code running on that page stays confined to its tab’s sandbox. It cannot access your saved passwords, read files on your hard drive, or interfere with your banking website open in another tab. Sandboxing in browser security fundamentally improves your safety while you browse the internet.
Also Read: What is Threat Hunting? Proactive Cyber Security
How does sandboxing work? This security measure relies on carefully controlled resource allocation and strict permission settings. The entire process works on the principle of minimal privilege and containment.
Let us now discuss the systematic steps the sandboxing security process involves:
This sequential pattern ensures that no malicious program can execute its attack on the real system. The isolation mechanism is highly effective.
Sandboxing implements its isolation using several techniques:
Also Read: Man-in-the-Middle (MITM) Attack - Prevention Guide
Sandboxing in cyber security plays a vital role in protecting organizations from the latest and most sophisticated threats. It helps in dealing with evasive malware that traditional defenses often miss.
Here are the key benefits of implementing a robust sandboxing security solution:
Many people wonder about the difference between a traditional antivirus program and sandboxing. While both aim at security, they operate on distinct principles.
Let us now discuss the differences between Antivirus and Sandboxing:
| Basis for Comparison | Traditional Antivirus (AV) | Sandboxing in Cyber Security |
|---|---|---|
| Primary Goal | To identify and remove known threats. | To safely execute, observe, and analyze unknown threats. |
| Detection Method | Signature-based (Scans files against a database of known malware code). | Behavioral analysis (Watches what a file does). |
| Effectiveness Against Zero-Day Threats | Low. AV cannot detect malware not yet in its database. | High. It stops any file that exhibits malicious behavior. |
| System Interaction | Scans files before they execute or periodically after they land. | Executes the file in a completely isolated, safe environment. |
| Core Technology | Code scanning and pattern matching. | Virtualization, Emulation, and Dynamic Analysis. |
| Keyword Relevance | Known malware, virus signature. | Zero-day, unknown threat, behavioral analysis. |
While traditional antivirus provides essential, front-line defense against common threats, sandboxing acts as a crucial, secondary line of defense against the most sophisticated and new attacks. For comprehensive protection, most organizations implement both.
The power of sandboxing extends beyond just endpoint security. New technologies have further utilized this isolation principle.
Cloud sandboxing involves leveraging the scalability and resources of cloud infrastructure to perform the dynamic analysis. This approach is becoming increasingly popular.
A cloud sandboxing tool directs suspicious files to an off-site, cloud-based environment for analysis. This provides several benefits:
Sandboxing is not limited to malware analysis. It performs key functions in various other domains:
Also Read: Domain Name System (DNS) Security | Threats, DNSSEC & Best Practices
Choosing and implementing a suitable sandboxing tool requires careful planning. You must ensure the tool integrates seamlessly with your existing security infrastructure.
To implement effective sandboxing security, consider the following aspects:
Sandboxing is clearly an indispensable pillar of modern digital defense. You now understand that it is far more than a simple file scanner; it is a dynamic, isolated environment. This secure space allows you to execute and observe the most dangerous, unknown threats without putting your system at risk.
Sandboxing security focuses on analyzing behavior, which makes it the best defense against zero-day and advanced persistent threats.
By implementing a powerful sandboxing tool, you actively shield your sensitive data and ensure business continuity. Your commitment to understanding and using sandboxing ensures a safer, more resilient digital future.
Proactive Sandbox Defense Contact our team
Here are five key takeaways about sandboxing in cyber security:
While highly effective, sandboxing is not perfect. Highly sophisticated malware may successfully use advanced evasion techniques to lie dormant until they detect a specific user action or a non-sandboxed environment. Also, analyzing massive files can sometimes cause minor delays.
Sandboxing in cyber security is critical for email defense. When your email server receives an attachment, the sandboxing tool runs it first. If the attachment is malicious, the sandbox identifies it, and your server blocks the email. This prevents phishing attacks and malware delivery via email.
A Virtual Machine (VM) is a technology that enables sandboxing. Sandboxing is the security concept of isolation and analysis. The VM is the most common tool used to create that isolated execution environment for a sandbox.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts