.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

You use many different applications every day. Each one asks you for a username and password. Keeping track of all these login details becomes a major headache. Single Sign-On (SSO) solves this big problem.
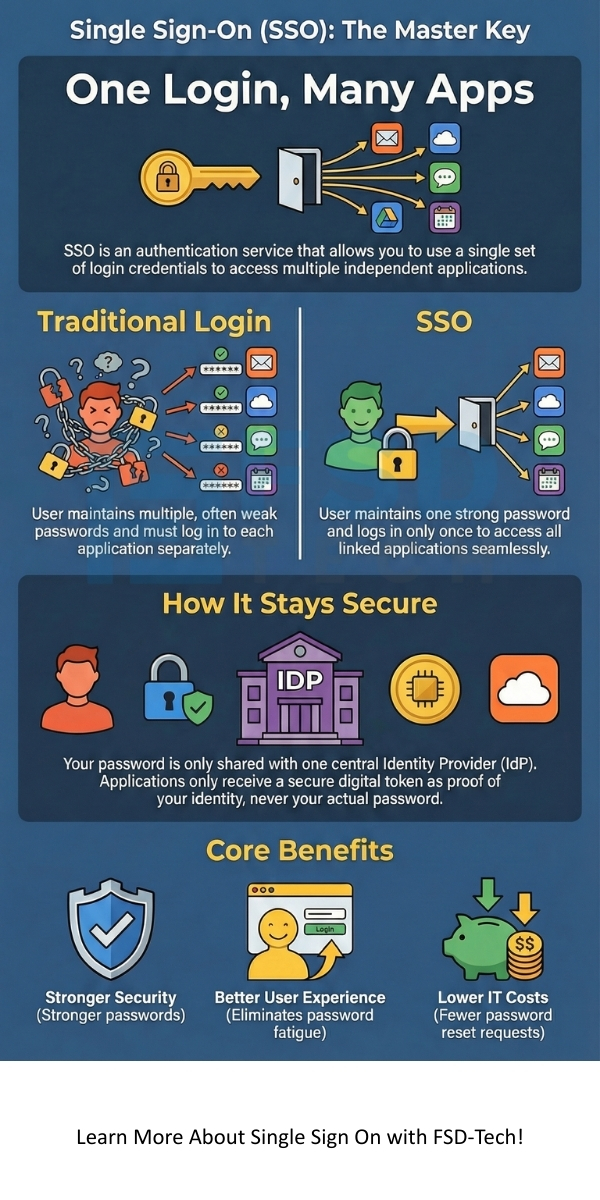
Single Sign-On (SSO) can be understood as an authentication process. This process allows a user to enter a single set of login credentials—like a username and password—to access multiple independent applications. Imagine one master key that unlocks every door you need to pass through. You enter the details once, and you are good to go for the rest of your session.
Single Sign-On (SSO) is a session or user authentication service. This service permits you to use a single ID and password to access several applications. SSO helps you manage many user accounts and passwords. It reduces the time you spend logging in again and again.
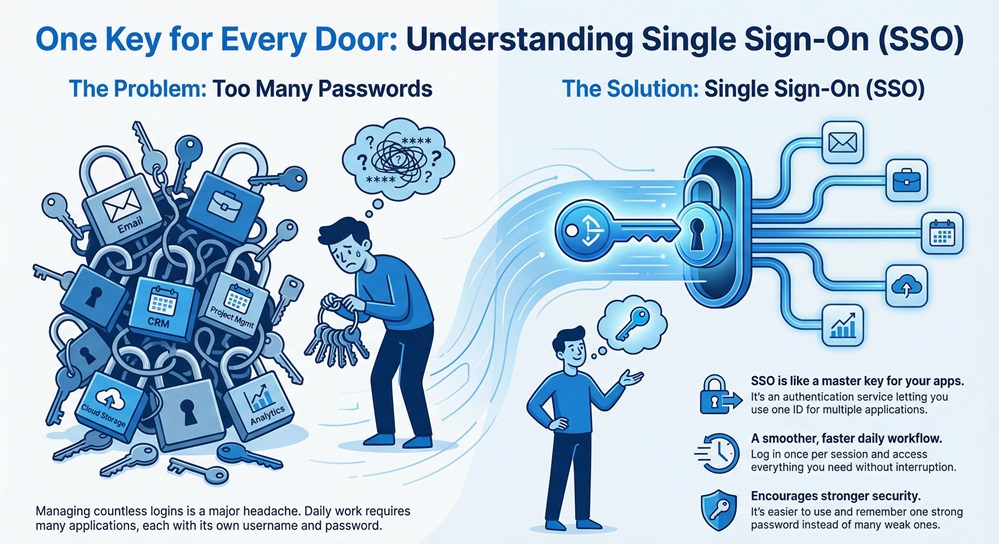
What does Single Sign-On mean for your daily work? It means a smoother, faster, and less frustrating user experience. It also means you use stronger passwords because you only need to remember one.
To understand the value of this technology, let us start by comparing it with the traditional login method.
| Basis for Comparison | Traditional Login | Single Sign-On (SSO) |
|---|---|---|
| Login Frequency | User must log in separately to each application. | User logs in once for all linked applications. |
| Password Management | User maintains multiple passwords, often leading to weaker, reused passwords. | User maintains one strong password, which simplifies management. |
| Security Risk | Higher risk of password fatigue and weak passwords. | Lower risk due to the use of strong, centrally managed credentials. |
| Productivity | Reduced productivity due to frequent login interruptions. | Enhanced productivity due to seamless application access. |
| IT Support Cost | Higher costs due to frequent password reset requests. | Lower IT support costs because fewer password resets happen. |
Single Sign-On authentication refers to how the system verifies you as a valid user. It uses a trust relationship between two main entities:
The IdP manages the authentication process. It checks your credentials against its user database. When you successfully log in, the IdP generates a security token. This token acts as your digital passport. The Service Provider accepts this token as proof that you are the person you claim to be.
SSO authentication relies heavily on security protocols. Why is Single Sign-On secure? It is secure because it does not share your password with every application. Only the Identity Provider ever sees your password.
Also Read: What is Biometric Authentication? Methods & Security Guide
To understand how Single Sign-On works, we must look at the step-by-step process. This process involves the user, the application (Service Provider or SP), and the central system (Identity Provider or IdP).
Let us explore the sequence of steps:
1. Initial Access
2. Redirection to the Identity Provider (IdP)
3. Authentication by the IdP
4. Token Generation
5. Return to the Service Provider
6. Token Validation and Access Grant
This systematic flow ensures that your sensitive credentials stay safe with the Identity Provider. The application, or Service Provider, only sees the proof of authentication—the token.
Also Read: What is Deepfake Detection? Role of Deepfake Detection Technology
Single Sign-On relies on several industry-standard protocols. These protocols define the structure of the communication and the security token. Knowing these helps you understand how does Single Sign-On work at a technical level.
1. Security Assertion Markup Language (SAML)
2. OpenID Connect (OIDC) and OAuth 2.0
3. Kerberos
What is Single Sign-On integration? It refers to the technical steps involved in setting up the relationship between the IdP and the SP. How to implement Single Sign-On depends heavily on the type of applications you use.
1. Federation-Based SSO
2. Agent-Based SSO
3. Password Vaulting (Less Common/Legacy)
Also Read: What is Click Fraud? Detection, Prevention & Tools
Implementing SSO provides significant benefits to both the user and the organization.
1. Improved User Experience
2. Enhanced Security
3. Reduced IT Costs
4. Simplified Compliance
The questions "Is Single Sign-On enabled?" and "How to enable Single Sign-On?" are common. The answers depend on your organization's setup.
Enabling Single Sign-On involves a systematic process:
How to Disable Single Sign-On
In certain situations, you may need to disconnect a user or an application. How to disable Single Sign-On for a user is simple:
Disabling SSO for a specific application involves removing the trust configuration between that Service Provider and the IdP. The application then reverts to its original login method.
So, with the above discussion, we can say that Single Sign-On (SSO) is an essential technology for modern organizations. SSO is nothing but the master key to a streamlined and safer digital experience. It addresses the twin problems of user frustration and weak security. It simplifies your life by requiring you to remember only one strong set of credentials. For the company, it plays a vital role in reducing IT support costs and improving overall security posture.
You now understand what is Single Sign-On. You also see how Single Sign-On works using protocols like SAML and the core relationship between the Identity Provider and the Service Provider.
Our focus remains on delivering solutions that ensure your organizational identity is protected. We offer expert guidance to help you successfully plan and execute your Single Sign-On integration.
Talk to our security specialists today to start building a future where your team works faster and safer.
Single Sign-On is secure when implemented correctly. It prevents users from creating weak passwords for many different services. The SSO system enforces strong security measures. For example, it often requires multi-factor authentication (MFA) at the point of the single login. This adds an extra layer of protection to your master credential.
SSO is about convenience and reducing the number of times you log in. MFA is about increasing security by requiring multiple proofs of identity. You can, and should, use them together. When you use SSO, you typically use MFA only once, at the start of your day, to prove your identity to the IdP.
No. This is a common misunderstanding. The Identity Provider (IdP) stores your master password. Individual applications (Service Providers) never see your password. They only receive a temporary security token from the IdP. This token confirms your identity without revealing your secret password.
The main challenge is the "single point of failure". If the central Identity Provider goes down, you lose access to all linked applications. Therefore, it is essential to ensure the IdP system is highly available and redundant. Also, the initial Single Sign-On integration can be complex, especially with older, non-standard applications.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts