.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

You want to protect your company's valuable information, right? Every organization must control who accesses which resources, whether it is a sensitive financial report or a critical system function. Role-Based Access Control (RBAC) provides a powerful and practical solution to this fundamental security challenge.
But, how exactly does RBAC work? And why is it considered the standard approach for managing rbac permissions in modern systems? Keep reading as we explain what is role-based access control RBAC, how it is structured, and how it helps you implement a robust security posture without the hassle of managing individual user rights.
Let us start with the rbac definition. Role-Based Access Control (RBAC) can be understood as a policy-neutral access control mechanism that manages and enforces security access based on the roles of individual users within an organization. This means the system grants access rights not directly to the individual user, but to the role the user possesses.
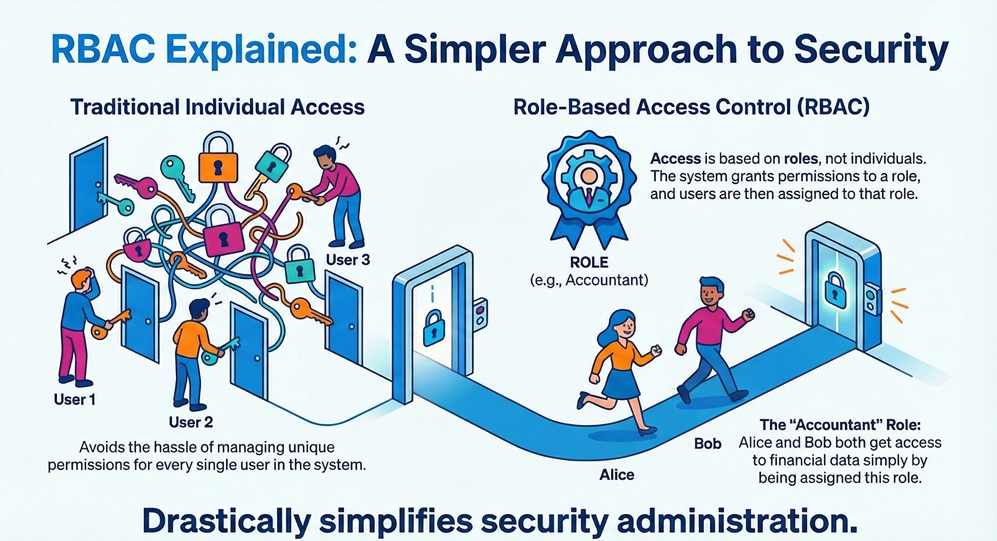
In simple words, you do not manage Alice's or Bob's access specifically. Instead, you define an "Accountant" role with specific access to financial data, and you simply assign Alice and Bob that rbac role. This approach greatly simplifies administration.
RBAC full form is Role-Based Access Control. This term refers to the method where access rights, which include permissions to perform specific operations, depend on the role a user possesses.
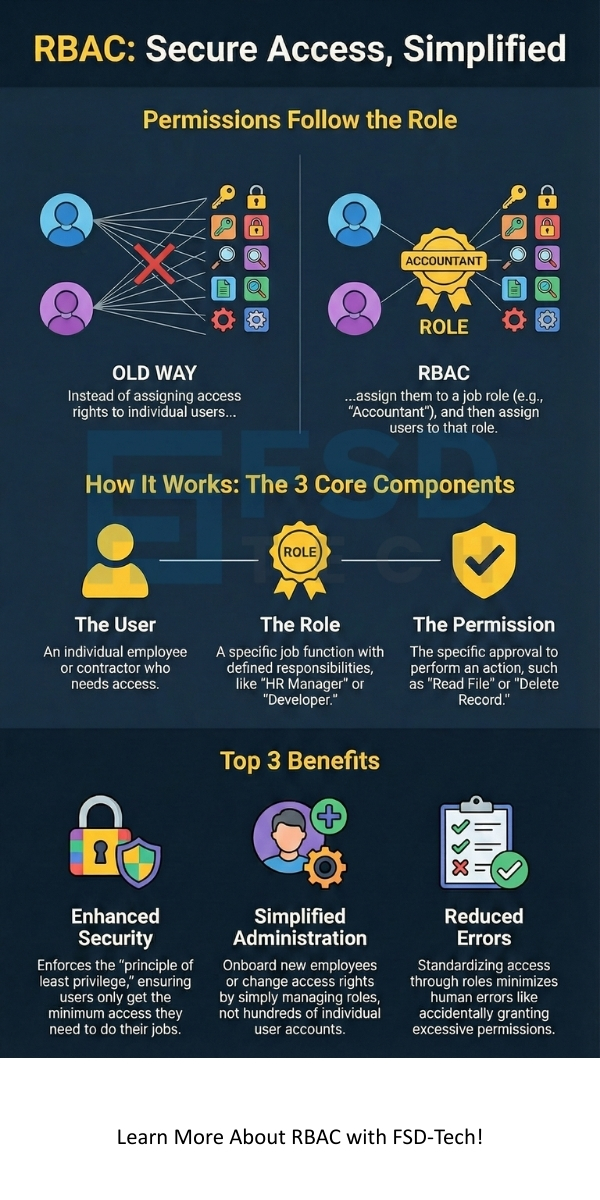
To understand how Role-Based Access Control (RBAC) functions, you must be familiar with its three fundamental elements. RBAC works on the principle of linking these components together to ensure that access is both secure and manageable.
1. The User Component
The User refers to any person or entity that requests access to a system resource. These are the individuals in your organization—employees, contractors, partners—who perform various functions.
2. The Role Component
The Role is nothing but a job function or a level of authority within the organization. Role-based access control RBAC defines roles like "System Administrator," "Auditor," "HR Manager," or "Guest."
3. The Permission Component
The Permission refers to the approval to conduct a specific operation on a specific object or resource. RBAC permissions are the most granular level of control. Examples include:
Permissions are granted to roles, and roles are assigned to users. This structure ensures that users only get the exact permissions they need to do their jobs.
Also Read: What is Attribute Based Access Control (ABAC)?
When a user attempts an action within an RBAC-enabled system, a systematic process is executed to determine if access is permitted. Let us now discuss the sequential steps for an rbac login and access check.
First: The Authentication Step
The user must provide their credentials, such as a username and password, to the system.
Second: The Role Assignment Check
Upon successful authentication, the system determines which roles the user possesses.
Third: The Access Request
The authenticated user attempts to perform an action, such as viewing a sensitive customer database.
Fourth: The Permission Check
The system compares the requested permission against the collective permissions of all roles assigned to the user.
In this way, the RBAC system controls access dynamically at the time of the request.
Role-Based Access Control (RBAC) is not a single, rigid model. The National Institute of Standards and Technology (NIST) defines several standard rbac models that organizations can implement based on their specific security needs and complexity.
1. RBAC0: The Core Model
RBAC0 is nothing but the fundamental model of Role-Based Access Control. It provides the basic framework.
2. RBAC1: Adding Role Hierarchy
RBAC1 extends the basic RBAC0 model by introducing a role hierarchy. This is crucial for larger organizations.
3. RBAC2: Including Constraints
RBAC2 introduces the concept of constraints or Separation of Duty (SoD) policies. Constraints are rules that govern the creation and usage of roles.
4. RBAC3: Combining Hierarchy and Constraints
RBAC3 is nothing but the comprehensive model. It combines the role hierarchy (RBAC1) and the constraints (RBAC2) with the core features (RBAC0).
Also Read: What is Internet Key Exchange (IKE)?
Why implement Role-Based Access Control (RBAC)? RBAC plays a vital role in modern security architectures. It ensures that users operate with the principle of least privilege. This principle dictates that a user must possess only the minimum rbac permissions they need to perform their job.
1. Enhanced Security and Compliance
RBAC reduces the risk of internal threats and data breaches.
2. Simplified Administration
Managing permissions for hundreds or thousands of individual users is complex.
3. Improved Operational Efficiency
Users can find that RBAC facilitates easier and faster access to the resources they need.
4. Reduced Errors
Manual permission management leads to errors, such as over-granting permissions or overlooking necessary ones.
To understand the practical application of Role-Based Access Control, let us examine a common scenario.
Example: A Corporate HR System
This RBAC example clearly shows how access depends on the user's specific job function. The system ensures that a Recruiter cannot access confidential salary data, and a Payroll Specialist cannot be the sole person who both processes and audits the payment.
Also Read: What is Disaster Recovery in Cloud Computing?
Kubernetes is nothing but an open-source system for automating deployment, scaling, and management of containerized applications. Within this platform, rbac in kubernetes plays a critical role in cluster security.
Kubernetes RBAC uses four key objects:
Kubernetes RBAC ensures that a developer can only deploy applications to their assigned Namespace, while a cluster administrator maintains control over the entire system.
When considering access control systems, you will often encounter the debate of rbac vs abac. While both aim at securing resources, they work on entirely different principles. ABAC and RBAC each offer distinct advantages.
| Basis for Comparison | Role-Based Access Control (RBAC) | Attribute-Based Access Control (ABAC) |
|---|---|---|
| RBAC Meaning / Principle | Access depends on the user's Role (job function). | Access depends on a set of Attributes (characteristics) of the user, resource, and environment. |
| Policy | Policy is static and role-centric. Predetermines permissions for each role. | Policy is dynamic and rule-centric. Evaluates a set of rules at the time of access. |
| Complexity | Simpler to implement and manage for small to medium complexity. | More complex to set up but provides fine-grained control for high complexity. |
| Scalability | Can become complex to manage with a high number of roles. | Scales well by allowing virtually infinite combinations of attributes. |
| Policy Change | Requires an administrator to change the role's permissions. | Requires an administrator to change the rule set. |
| Best Suited For | Organizations with clear, well-defined job functions. | Highly dynamic environments and systems requiring highly specific access rules (e.g., time-of-day access). |
Now, the question arises, what is PBAC? PBAC stands for Policy-Based Access Control.
So, with the above discussion, we can say that Role-Based Access Control (RBAC) serves as the essential backbone for security and access management in nearly every modern enterprise system, from basic corporate applications to complex systems like kubernetes RBAC.
The methodology is simple: assign permissions to roles, and assign roles to users. This focuses the management effort on defining job functions rather than tracking countless individual user rights. RBAC ensures that every user—and only that user—possesses the precise level of access required to perform their job, which results in a security model that is more secure, easier to manage, and significantly more compliant.
We are committed to helping organizations like yours implement security solutions that ensure your data is protected and your operations remain efficient.
Contact us today to explore how our expertise can optimize your security architecture.
Yes, RBAC is significantly more secure than traditional Discretionary Access Control (DAC), where users can grant or revoke access to their own files. RBAC enforces a central security policy and implements the crucial principle of least privilege, which minimizes the attack surface.
Absolutely, a single user can be assigned multiple rbac roles. For example, a "Software Engineer" who also leads a small project can possess both the "Developer" role and the "Project Leader" role. The system combines the permissions of all assigned roles to determine the user's total access rights.
The primary challenge of Role-Based Access Control involves the initial definition of roles and permissions. If the roles are not properly designed or reflect the actual job functions, you can end up with too many roles or overlapping permissions, which creates a phenomenon known as "role explosion." Regular audits are required to maintain role clarity.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts