.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Are you worried about keeping your online data safe and private? When your computer connects with another device over the internet, a serious risk of eavesdropping and tampering always exists. To stop this from happening, network security uses a powerful set of rules known as IPsec, which stands for Internet Protocol Security.
But IPsec needs a smart way to manage the secret keys it uses for encryption. This is where the Internet Key Exchange (IKE) protocol comes in.
Internet Key Exchange (IKE) is nothing but a key management protocol. IKE plays a vital role in setting up a secure and protected communication channel between two devices, like two computers or two network gateways. It works with IPsec to create the essential security associations, or SAs, which are agreements about the security parameters, like which encryption algorithm to use.
Without IKE, you would have to manually set up and manage these complex security associations on every device. This is clearly not practical.
We will discuss how this protocol works and why it is so crucial for modern secure networking. You will learn about the main keyword, internet key exchange protocol, and its different stages.
The internet key exchange protocol is a standard defined by the Internet Engineering Task Force (IETF). This protocol is specifically designed to manage the key exchange and authentication steps that set up Security Associations (SAs) for the IPsec framework.
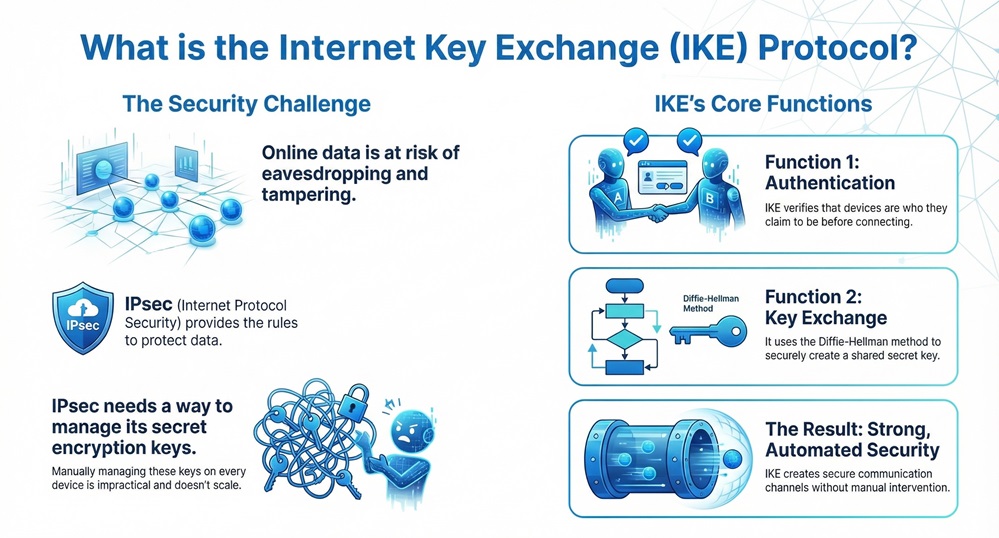
What is the main role of the internet key exchange protocol? It provides two primary functions:
This system ensures that even if an attacker listens in on the key setup process, they still cannot figure out the final secret key. This is why the internet key exchange protocol is essential for strong, automated security.
People often talk about Internet Key Exchange (IKE) and IPsec together. However, they serve different, specific purposes.
| Basis for Comparison | Internet Key Exchange (IKE) | IPsec (Internet Protocol Security) |
|---|---|---|
| Primary Purpose | Key management, authentication, and setting up Security Associations (SAs). | Providing security services, such as confidentiality and integrity, to IP packets. |
| Layer of Operation | Operates primarily in the application/transport layer for key management. | Works directly at the Network Layer (IP Layer). |
| Function | IKE helps to negotiate and establish the necessary security parameters. | IPsec applies the security services using the keys and algorithms set by IKE. |
| Protocols Included | IKE is a single protocol. | IPsec comprises two protocols: Authentication Header (AH) and Encapsulating Security Payload (ESP). |
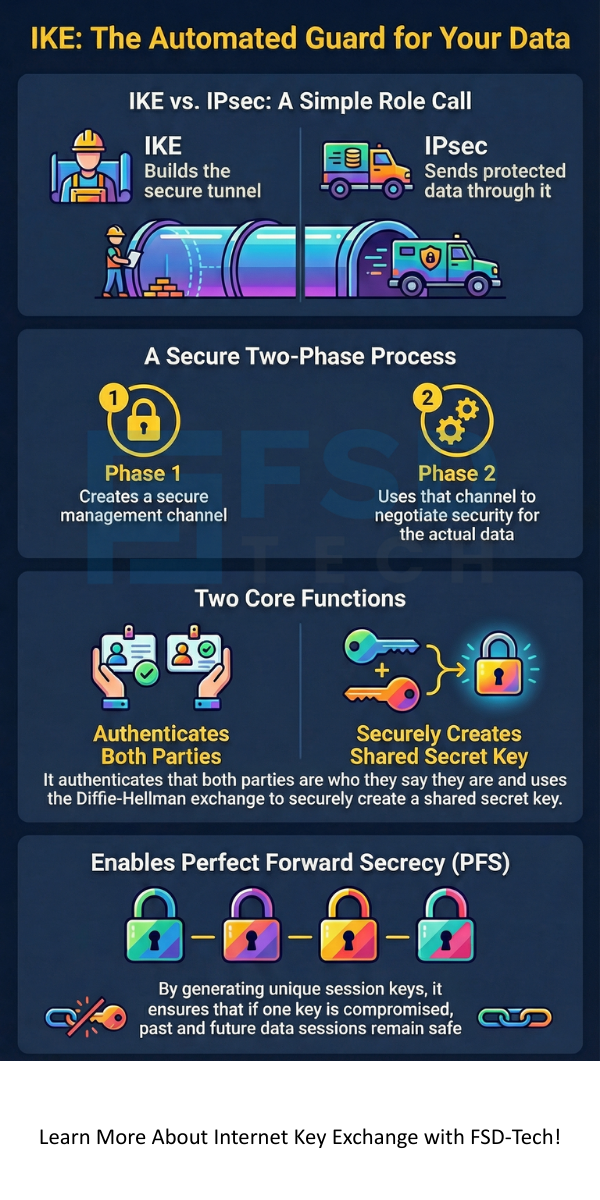
Internet Key Exchange (IKE) literally manages the keys, while IPsec uses those keys to protect your data. IKE creates the tunnel; IPsec sends the secure traffic through it.
Also Read: IPSec Explained: Protocols, Modes, IKE & VPN Security
The internet key exchange in network security follows a structured two-phase approach. This structured approach helps in separating the complex task of establishing a secure management channel from the simpler task of creating specific data-protection channels.
How does internet exchange work? The process is sequential. First, the two devices establish a secure channel for management, and then they use that channel to create multiple channels for data.
In the first phase, the two devices, called peers, focus on setting up a highly protected channel for themselves. This channel is known as the IKE SA, or Internet Security Association and Key Management Protocol (ISAKMP) SA.
What is the goal of IKE Phase 1? The main goal is to establish a secure, authenticated, and secret communication path. This path will protect the messages exchanged during Phase 2.
IKE Phase 1 includes the following key steps:
This phase results in a secure channel. This secure channel ensures that the more critical key exchanges in Phase 2 are fully protected.
IKE Phase 1 has two distinct modes of operation: Main Mode and Aggressive Mode.
Once the secure IKE SA is active, the peers move to the second phase. This phase is simpler and faster because all messages are protected by the Phase 1 IKE SA.
What happens in IKE Phase 2? The peers negotiate and set up one or more IPsec SAs. These SAs define the exact security parameters for the actual user data traffic.
IKE Phase 2 includes these steps:
This phase uses a single mode called Quick Mode. Quick Mode allows the rapid establishment of IPsec SAs under the protection of the existing Phase 1 tunnel.
Also Read: What is a Network Interface Card? How Does NIC work?
The internet key exchange in cryptography and network security represents a significant advance in automated key management. Before IKE, network administrators had to perform key management manually. This task was difficult, time-consuming, and introduced human errors, creating security holes.
IKE implements several important cryptographic principles:
What specific security services does IKE facilitate? It directly facilitates the creation of a secure environment that allows IPsec to deliver the following services:
The internet key exchange in network security is clearly the brain behind IPsec's brawn.
The internet key exchange in IPsec is absolutely essential. IPsec provides security for the Internet Protocol (IP), the fundamental protocol of the internet. Without IKE, IPsec would be extremely difficult to deploy and manage on a large scale.
IKE addresses the two most challenging parts of setting up an IPsec connection:
Therefore, the internet key exchange (IKE) protocol guarantees that IPsec can run smoothly and securely without manual intervention.
We can now clearly say that the internet key exchange protocol is an essential part of modern networking security. It is nothing less than the automated, intelligent backbone that makes IPsec effective and scalable. Internet Key Exchange (IKE) provides the necessary authentication and key management that protect your data from eavesdroppers and attackers. The clear separation of tasks in the two phases—first creating a secure management channel and then creating protected data channels—ensures both efficiency and a high level of security, particularly through the use of Perfect Forward Secrecy (PFS).
If your business relies on secure communication, understanding and correctly implementing the internet key exchange in IPsec is not just a technical detail—it is a business necessity. Our focus is on providing you with the comprehensive knowledge and solutions you need to keep your networks protected. We believe in building secure, transparent, and trustworthy digital relationships with you.
Contact us today; we will help you implement and maintain the highest standards of network security.
Here are the five essential takeaways regarding the internet key exchange protocol:
Here, we will discuss some common questions about this key management protocol.
Internet Key Exchange (IKE) mainly uses User Datagram Protocol (UDP) port 500. For its newer version, IKEv2, it also uses UDP port 4500 for NAT traversal.
There are two main versions: IKEv1 and IKEv2. IKEv2 is an improvement over IKEv1. IKEv2 is simpler, uses fewer messages, and is more resilient to network disruptions.
"SA" stands for Security Association. This is a document or agreement between two devices. It defines the specific security rules, such as the encryption key, the cryptographic algorithms, and the lifetime of the connection. IKE is responsible for managing these SAs.
Perfect Forward Secrecy (PFS) is critical because it ensures that a new, temporary key protects each session. This means that if an attacker manages to compromise the main, long-term key, they still cannot use it to decrypt past data. This process limits the damage from a security breach.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts