.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

The world of networking feels huge, but controlling who accesses your services is vital for security. You need a reliable gatekeeper—a system that ensures only authorized users step inside your digital home. What if a single, proven standard could handle all the authentication, authorization, and accounting for your entire network, from Wi-Fi to VPNs?
This guide will walk you through the inner workings of the Remote Authentication Dial-In User Service (RADIUS) protocol. You will learn exactly how this foundational technology manages access control. We will discuss its components, how it secures information, and why it remains an essential, vital, critical tool for network professionals globally. By the end, you will understand the clear advantages this system offers your network security posture.
The RADIUS protocol is a networking standard that provides centralized Authentication, Authorization, and Accounting (AAA) management for users connecting to a network service. This protocol ensures that only authorized users access network resources. RADIUS protocol usage began in the early 1990s as a solution for dial-up access but quickly adapted for modern networks.
Is RADIUS a protocol?
Yes, it is. The RADIUS protocol defines the rules and format for messages exchanged between network devices and a central server. This robust structure enables effective security management. The RADIUS protocol is nothing but a mechanism that governs the user access process. It is important to note that the Internet Engineering Task Force (IETF) defines the RADIUS protocol rfc, specifically RFC 2865, which sets the standard for its operation.
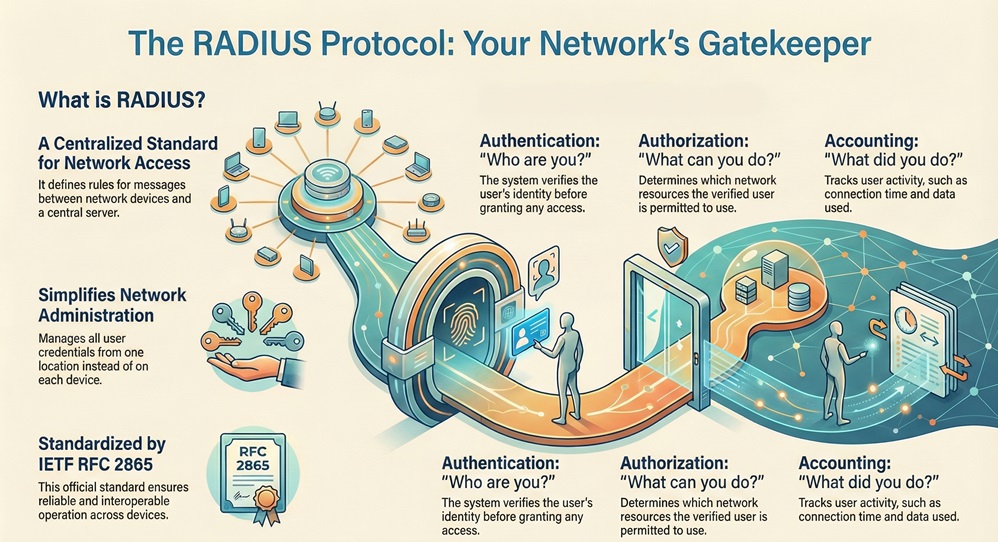
RADIUS primarily serves three distinct functions:
The design of the RADIUS protocol separates the core access functions from the Network Access Server (NAS). This separation allows you to manage all user credentials from one location—the central RADIUS server. This approach vastly simplifies network administration and secures your environment.
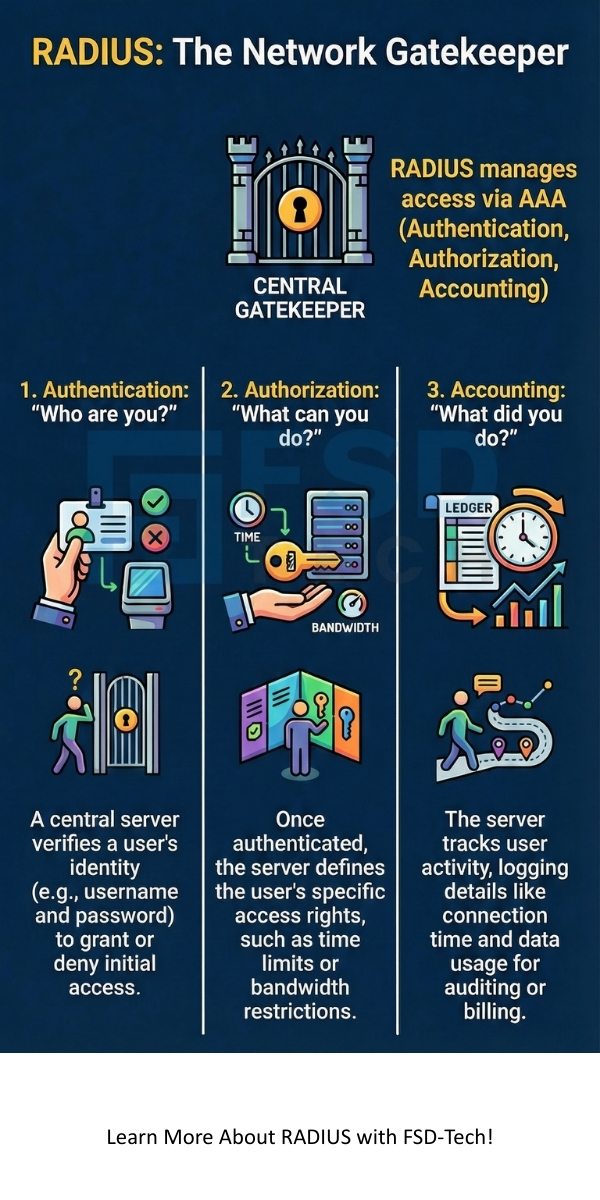
To secure your network, the RADIUS protocol relies on a clear, three-part process known as AAA. You must understand this sequential pattern to grasp the flow of network access.
The access process follows these steps:
How RADIUS authentication works effectively determines whether a user is who they claim to be. This process is crucial for preventing unauthorized entry into your infrastructure.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
The RADIUS protocol operates on a basic client-server model. This model ensures the central server handles all sensitive operations.
When a user tries to access the network, the client forwards the request, and the server provides the answer. This clear division of labor ensures that the authorization logic resides securely on the server, away from the access points.
RADIUS authentication begins when the user provides a username and password to the NAS. The NAS does not directly verify these credentials. Instead, the NAS sends an Access-Request message to the RADIUS server.
The RADIUS server performs the following actions:
RADIUS authentication relies on a shared secret key configured on both the client and the server. This secret key ensures that no third party can easily listen to or tamper with the communication.
Also Read: What is Web Application Firewall? | WAF Explained
Once the user authenticates successfully, authorization begins. RADIUS authorization determines what resources the newly connected user can access.
The RADIUS protocol itself is an application-layer protocol, but it relies on a transport layer protocol to move its messages across the network. What protocol does RADIUS use for transport? It uses the User Datagram Protocol (UDP).
UDP is a connectionless protocol. This means that the server does not establish a persistent connection before sending a response. It simply sends the data. The RADIUS protocol uses UDP primarily for efficiency and speed, which are essential when managing many simultaneous access requests.
RADIUS typically operates over the following UDP ports:
Some older systems may still use the original ports 1645 (Authentication/Authorization) and 1646 (Accounting). RADIUS protocol implementations often support both sets, but modern networks primarily rely on ports 1812 and 1813. Since UDP does not guarantee delivery, the RADIUS client implements its own retransmission and timeout mechanisms.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
A RADIUS server is the cornerstone of any network implementing centralized access control. Its functionality comprises more than just checking usernames and passwords. It acts as a policy engine for the entire network.
The RADIUS server performs several roles:
What radius server solution you choose often depends on the scale and complexity of your network. Both open-source options, like FreeRADIUS, and commercial solutions are available to handle these critical tasks. The RADIUS server plays a vital role in network security and operations.
RADIUS protocol security is a significant consideration, especially since the messages often carry sensitive authentication details. While the protocol uses UDP (which is inherently insecure), the RADIUS protocol has built-in mechanisms to provide necessary protection.
Shared Secret Mechanism
The shared secret is the foundational layer of RADIUS protocol security. This shared secret is nothing but a text string known only to the NAS (client) and the RADIUS server.
Message Format and Attribute Value Pairs (AVPs)
All communication in the RADIUS protocol uses a specific message format. This consistent structure includes a Code, Identifier, Length, and Authenticator field.
The actual data is contained in the Attribute-Value Pairs (AVPs). The AVP is a powerful and flexible concept.
The flexibility of AVPs allows vendors to add custom attributes. This adaptability makes the RADIUS protocol a comprehensive tool for various network needs, facilitating a smooth exchange of necessary details.
The RADIUS protocol defines specific message types used to perform the AAA functions. These messages are vital for sequential information flow.
| Code | Message Type | Purpose |
|---|---|---|
| 1 | Access-Request | Client asks the server for user authentication. |
| 2 | Access-Accept | Server confirms successful authentication and authorization. |
| 3 | Access-Reject | Server denies user access. |
| 4 | Accounting-Request | Client sends accounting data (start, stop, or interim). |
| 5 | Accounting-Response | Server confirms receipt of accounting data. |
| 11 | Access-Challenge | Server requests additional information from the client. |
When you use the RADIUS protocol, the system must correctly process these codes to ensure that network access is granted or denied accurately.
While the RADIUS protocol is the dominant standard, another system, Terminal Access Controller Access-Control System Plus (TACACS+), serves a similar function. Understanding the differences helps you determine the best solution for your network security.
| Basis for Comparison | RADIUS Protocol | TACACS+ Protocol |
|---|---|---|
| Transport Protocol | UDP (Ports 1812/1813) | TCP (Port 49) |
| Encryption | Only the user password is encrypted; other data (AVPs) are visible. | The entire packet body is encrypted. |
| Separation of AAA | Combines Authentication and Authorization functions. | Separates Authentication, Authorization, and Accounting. |
| Vendor | Open Standard (IETF RFCs). | Cisco proprietary, but widely supported. |
| Authorization Detail | Less granular, limited command authorization. | Very granular, extensive command authorization. |
Here are the key distinctions you should keep in mind:
If you require high-security control over specific device commands, TACACS+ often provides a better fit. However, for general network access, the ubiquity and simplicity of the RADIUS protocol explained make it the most common choice.
Also Read: What is Phishing Simulation? Benefits & Best Practices
The RADIUS protocol is an open standard, meaning no single company or entity fully owns or controls it. Who regulates the RADIUS protocol? The protocol is governed by a series of Request for Comments (RFCs) published by the Internet Engineering Task Force (IETF).
The IETF is the primary standards organization for the internet protocol suite. It is important to note that the IETF maintains the core specifications, ensuring interoperability and setting the rules for vendors. This open standard approach has been a major factor in the widespread adoption of the RADIUS protocol. Since its core specifications are publicly available, multiple vendors and developers can create compatible implementations, which benefits you by preventing vendor lock-in.
The RADIUS protocol is not just for dial-up anymore. Its flexibility and centralized AAA capability have made it essential across a wide range of modern networking services.
RADIUS protocol explained clearly how a centralized system can manage diverse access points. This concentration of management significantly reduces the effort required to maintain a secure and auditable network environment.
We have discussed how the RADIUS protocol serves as the essential, vital backbone for centralized network access control. You now understand that it provides the critical AAA services—Authentication, Authorization, and Accounting—that your organization needs. By using a secure, central RADIUS server, you effectively manage all user access points, from Wi-Fi to VPNs. Therefore, the protocol helps you enforce strong security policies and track all user activities reliably.
Implementing the RADIUS protocol means you are choosing a proven, industry-standard solution governed by IETF RFCs. This decision ensures that your network access management is efficient, secure, and ready to scale with your organization's growth. We focus on providing you with tools and knowledge that guarantee network integrity and client focus. Secure access to your network resources is nothing but our commitment to your operational success.
Proactive RADIUS Defense Contact our team
RADIUS server software comprises both commercial and open-source options. For example, you can choose solutions like Microsoft NPS (Network Policy Server) or FreeRADIUS. The choice depends on your operating system environment and the complexity of your requirements.
RADIUS provides security through the shared secret and password encryption, but it does not encrypt the entire message body. Due to this limitation, RADIUS protocol security often requires the addition of other transport security layers, such as IPsec, to fully protect all information.
If the RADIUS server is unavailable, the client (NAS) will fail to authenticate new users. To prevent a complete service outage, network designs generally include redundant, secondary RADIUS servers. This conditional pattern ensures that if one server fails, the client automatically attempts to connect to the next one.
RADIUS manages authorization using the same authentication message exchange. The Access-Accept message sent back from the server includes specific Attribute-Value Pairs (AVPs). These AVPs determine the specific access rights, such as VLAN assignment or bandwidth limits, thereby defining the authorization level.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts