.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Let us understand a powerful security model that protects your data with intelligence and flexibility. You probably already know about simple security rules. But as companies grow, these old rules often fail. We are talking about Attribute Based Access Control (ABAC). This is a logical access control system.
It controls access to objects based on the attributes of the user, the resource, and the environment. You are seeking a modern way to manage who can see what. ABAC provides a sophisticated answer.
ABAC uses policies that consider many factors, unlike simpler methods that only look at a user’s role or name. This allows for very fine-grained control. Attribute Based Access Control is a next-generation security solution. It ensures only the right people get access under the right conditions.
Attribute Based Access Control can be understood as a logical access control method. This method regulates access to resources based on the evaluation of attributes. These attributes belong to four distinct categories: user, resource, environment, and the action requested.
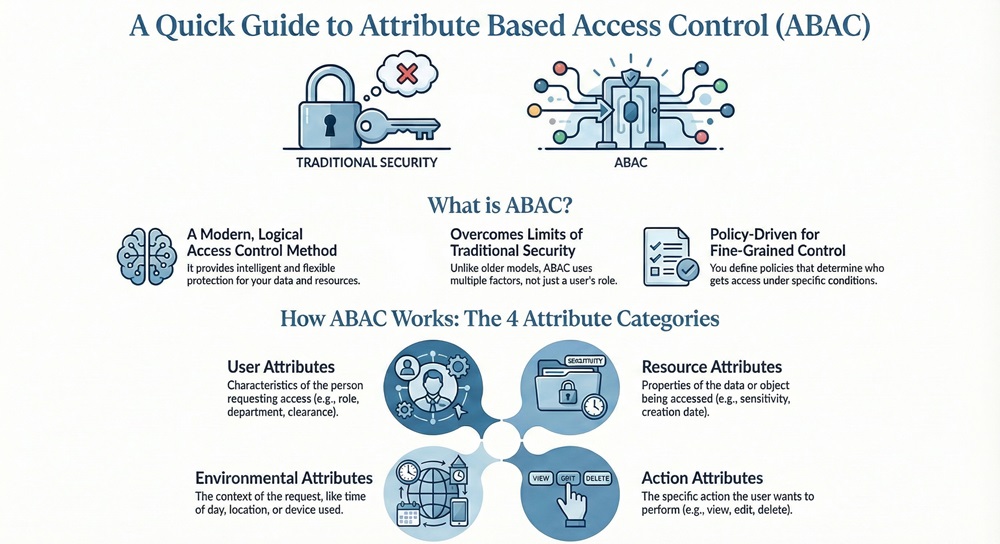
Simply put, ABAC is an access control model that evaluates a set of attributes and context before allowing or denying a user’s access request. It is a policy-driven model. This means that you define policies. These policies determine the access permissions.
The core idea is to move beyond fixed roles. This system enables decision-making based on who you are, what you are trying to access, how you are trying to access it, and when/where you are doing it.
To understand this better, let us compare Attribute Based Access Control with its predecessors, Discretionary Access Control (DAC) and Role-Based Access Control (RBAC).
| Basis for Comparison | Attribute Based Access Control (ABAC) | Role-Based Access Control (RBAC) | Discretionary Access Control (DAC) |
|---|---|---|---|
| Primary Focus | User, resource, and environment attributes | User's role within the organization | User's identity and resource owner |
| Control Granularity | Very Fine-Grained (Dynamic and context-aware) | Medium-Grained (Static roles and permissions) | Coarse-Grained (Owner controls access) |
| Policy Basis | Rules defined using attributes (e.g., job title, security clearance, time of day) | Permissions tied to specific roles (e.g., 'Manager,' 'Engineer') | Access granted by the resource owner |
| Scalability | High: Scales well with a large number of users and resources by managing fewer policies | Medium: Can become complex with too many roles or role-permission mappings | Low: Management becomes difficult as the number of users and resources increases |
| Implementation Complexity | High | Medium | Low |
Also Read: What is Business Email Compromise (BEC)? How to Prevent?
The Attribute Based Access Control model comprises several essential parts. These parts work together to determine access. Understanding these components helps in proper Attribute Based Access Control implementation.
Attributes are nothing but characteristics. These characteristics describe a user, a resource, an action, or the environment. They are the fundamental building blocks of an ABAC policy. The system uses them to evaluate access requests.
ABAC utilizes four main types of attributes:
The Policy Enforcement Point is the gatekeeper. It acts as an intermediary between the user and the resource. When a user attempts access, the PEP intercepts the request.
The PEP's role is critical. It sends the access request and relevant attributes to the Policy Decision Point (PDP). The PEP then enforces the final decision—allowing or denying access—that it receives back from the PDP.
The Policy Decision Point is the brain of the Attribute Based Access Control system. It receives the access request from the PEP.
The PDP then evaluates the request against the defined set of Attribute Based Access Control policies. To do this, it requests the necessary attribute values from the Policy Information Point (PIP). The PDP determines the final access decision—Permit or Deny—and sends it back to the PEP for enforcement.
The Policy Information Point is the source of all attribute values. It serves as the point of contact for the PDP.
The PIP's function is to collect the required attribute data from various external sources. These sources often include corporate directories, identity management systems, databases, or environmental sensors. It provides the necessary context for the PDP to make an informed decision.
The Policy Administration Point allows administrators to create, manage, and update the Attribute Based Access Control policies. This component ensures the policies are accurate and current. PAP defines the rules that govern access throughout the system.
Also Read: What is Patch Management? Securing Your Digital Assets
An Attribute Based Access Control policy is the rule set that the PDP uses to evaluate access. It is not tied to a specific user or role. Instead, it relies on logical expressions built from the attributes.
A policy often follows a structure like: "If [User Attribute] AND [Resource Attribute] AND [Environment Attribute], then [Permit/Deny] the [Action Attribute]."
Attribute Based Access Control example of a policy:
Policy: If the User's Department is 'Finance' AND the Resource's Classification is 'Confidential-Financial' AND the Action is 'Read' AND the Time of Day is between 9:00 AM and 5:00 PM, THEN Permit access.
This simple Attribute Based Access Control example shows how the system can automatically deny access to a Finance user attempting to view the same file at 10:00 PM. This is because the Environment Attribute condition is no longer met.
Attribute Based Access Control implementation is a structured process. It ensures the model is correctly deployed and effectively manages access.
Step 1: Identify and Define Relevant Attributes
First, you must identify the critical attributes in your environment. This involves understanding your users, resources, and operational context.
Step 2: Develop the ABAC Policy Set
Next, you create the actual ABAC policies. This involves translating your organization's security requirements into attribute-based logical rules. Developing a robust Attribute Based Access Control policy set requires deep consultation with stakeholders.
Policies should be comprehensive. They cover all necessary access scenarios. You use the identified attributes to build the "If... Then..." statements.
Step 3: Integrate and Configure ABAC Components
This step involves setting up the technical framework. You integrate the PEPs into the applications and systems where access needs control.
You then configure the PDP to receive requests and connect the PIP to all attribute data sources. A properly configured PDP is vital. It ensures accurate and timely access decisions.
Step 4: Test, Review, and Refine Policies
After deployment, you must thoroughly test the ABAC system. Testing involves simulating various access requests. You must verify that the policies produce the intended access decisions.
Continuous review and refinement are essential. The system must adapt as organizational attributes, like new departments or resource classifications, change.
Also Read: What is a Network Switch? Core of Modern Networking
Attribute Based Access Control in cyber security plays a vital role in modern security architectures. It moves beyond simple perimeter defense. It supports the principle of Zero Trust.
ABAC provides a key feature: dynamic access control. This means access decisions are made in real-time, at the moment of the request. This capability allows the system to respond instantly to changes in the environment or user status.
Attribute Based Access Control Database Design
Designing a system for Attribute Based Access Control database design involves a few key tables. These tables maintain the attribute information that the PIP collects.
The structure of the data ensures that the system can quickly retrieve the needed attributes. Fast retrieval is crucial for real-time access decisions.
Your data’s security is our highest priority. We believe that modern access control should be intelligent, flexible, and fully aligned with your business operations. Our solutions focus on empowering you with robust, fine-grained access management systems.
This ensures that you can move forward with confidence, knowing your critical information is protected precisely as your policies dictate. We commit to providing you with the necessary expertise. This expertise allows you to implement Attribute Based Access Control efficiently and maintain a strong security posture.
Worried About Access Risks? Reach us for immediate help

The main benefit is its flexibility and fine-grained control. ABAC allows security teams to create policies that are much more precise than those in traditional models. This precision reduces security risk by only granting the minimum necessary access.
ABAC does not always replace RBAC completely. Often, it augments or extends RBAC. However, in complex, dynamic environments, ABAC is superior. It avoids the role explosion problem where too many roles make RBAC management impossible. ABAC uses a smaller set of attributes to manage a much larger number of access scenarios.
Initial Attribute Based Access Control implementation is more complex than RBAC. This is because defining the attributes and initial policies requires careful planning. Once deployed, however, a well-structured ABAC system reduces the ongoing administrative burden. You only update the policy or the attribute values, not individual permissions.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts