
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how your private data stays safe when you send it across the internet? You type your password or credit card number into a website and hit enter. In that split second, a complex system of digital locks and keys guards your information. Without this system, hackers could easily steal your identity or money. This invisible shield is the reason you can trust online shopping and banking.
Do you want to know the secret behind this digital trust? It involves a clever mix of math and security rules that keep the world connected.
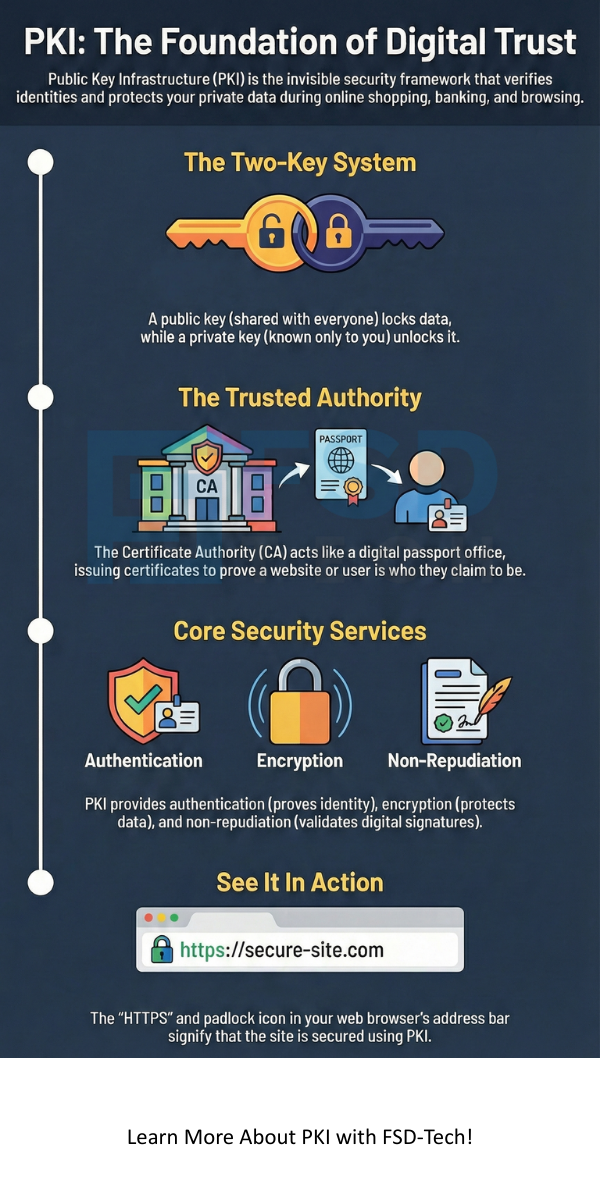
Public Key Infrastructure refers to a framework of roles, policies, and hardware used to manage digital certificates. It creates a secure way to exchange information over an unsecure network. You can think of it as the digital version of a passport system. It proves that a person or a website is who they say they are. In the world of tech, we call this electronic identity verification.
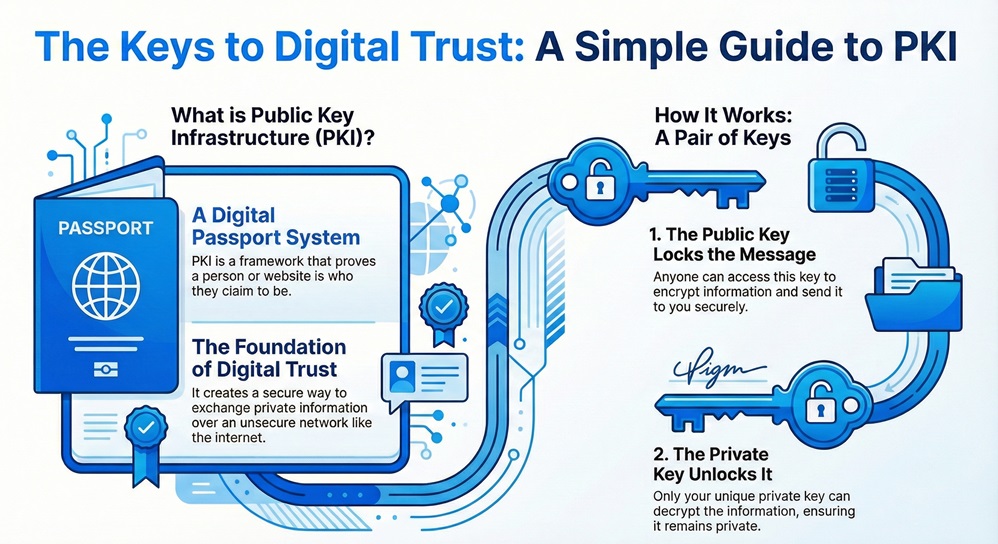
Public Key Infrastructure provides the foundation for secure electronic transfer of information. It uses a pair of keys to protect data. One key is public and anyone can see it. The other key is private and only you keep it. These keys work together to encrypt and decrypt your messages. If someone sends you a message using your public key, only your private key can open it. This ensures that your private conversations stay private.
Public Key Infrastructure uses asymmetric encryption, but it is helpful to see how it differs from symmetric encryption. Many people get confused between these two methods.
| Feature | Symmetric Encryption | Public Key Infrastructure (Asymmetric) |
|---|---|---|
| Number of Keys | One single key for both tasks | Two distinct keys (Public and Private) |
| Key Distribution | Difficult to share the key safely | Easy to share the public key |
| Security Level | Lower for large networks | Higher for large-scale internet use |
| Speed | Very fast | Slower due to complex math |
| Main Use | Bulk data encryption | Secure key exchange and signatures |
| Authentication | Does not provide non-repudiation | Provides strong digital signatures |
Also Read: What is Asymmetric Encryption? Keys and How It Works
Public Key Infrastructure technology relies on several key parts to work correctly. Each part has a specific job to do. If one part fails, the whole system of trust can break down.
Public Key Infrastructure ensures that all these pieces talk to each other. When you visit a website, your browser checks the site's certificate against a list of trusted CAs. If the CA is trusted, you see a green padlock in your browser bar. This simple icon tells you that the system is working to keep you safe.
How public key infrastructure works involves a clear sequence of events. It starts when a user wants a digital identity. You cannot just make your own certificate and expect people to trust it. You must follow a specific process to gain trust.
How public key infrastructure works also covers what happens when you send a message. When you want to send an encrypted email, you find the receiver's public key in a directory. You use that key to lock the file. Once the file is locked, nobody can open it except the person with the matching private key. This is the core of how public key encryption works in daily life.
Also Read: What is Security Information and Event Management (SIEM)?
Public Key Infrastructure authentication is the process of proving your identity to a computer system. It is much stronger than using just a username and password. Passwords can be guessed or stolen easily. A digital certificate is much harder to fake. Many big companies use this to let employees log into private networks.
Public Key Infrastructure services also include something called non-repudiation. This is a fancy way of saying that a person cannot deny they signed a document. Because only you have your private key, a signature made with it must be yours. This makes digital contracts legal and binding. It provides a digital paper trail that you can trust in court.
Public Key Infrastructure definition can be broad, so let us look at the specific terms you need to know. Understanding these terms will help you master the topic.
Public Key Infrastructure uses these terms to build a wall of security around your data. It turns the internet from a wild frontier into a safe place for business. Have you noticed how almost every website now starts with "HTTPS"? That "S" stands for secure, and it means the site uses this technology.
Public Key Cryptography algorithms are the math rules that create the keys. These rules are so complex that even the fastest computers would take millions of years to break them.
Public Key Cryptography algorithms must stay ahead of hackers. As computers get faster, the math must get harder. This is why you might hear about "quantum-resistant" math in the news lately. Security experts are always working on the next generation of locks.
Also Read: Quantum Cryptography - QKD, Security & Future Guide
Public Key Cryptography examples are all around you. You use them every single day without even thinking about it.
Public Key Cryptography examples show that this is not just for tech experts. It is a vital part of modern life. It keeps your bank account safe and your private messages away from prying eyes. Can you imagine a world where anyone could read your private texts? That is what the internet would be like without these tools.
Public Key Cryptography news often focuses on how we can make things even safer. One big trend is the move toward automation. In the past, people had to manage certificates by hand. This led to many mistakes. Now, systems like "Let's Encrypt" do this automatically. This has helped make almost the entire web secure for free.
Public Key Cryptography news also talks about the threat of quantum computers. These future machines might be able to break current RSA codes very quickly. Because of this, scientists are creating new types of keys that even a quantum computer cannot crack. This shows that security is a race that never ends. We must always be one step ahead of the people trying to break in.
Public Key Infrastructure acts as the backbone of digital trust in our modern world. It allows us to share ideas, buy products, and connect with others without fear. By using smart math and strict rules, it keeps our most private information hidden from those who would do harm. We believe that everyone deserves a safe and secure digital experience. Our team is dedicated to providing you with the best security knowledge to help your business thrive.
We focus on your success by making sure your digital identity remains solid and unshakeable. Trust is the most valuable thing you can own in the digital age, and we are here to help you protect it.
Start PKI Setup Contact FSD-Tech today
Public Key Infrastructure is a complex topic, but the main points are simple to remember.
The main goal is to manage keys and certificates so people can trust digital identities. It ensures that when you talk to "Bank A," you are actually talking to "Bank A" and not a fake site.
You share your public key with the whole world. It is like your home address. Anyone can send you mail using it. Your private key is like the key to your mailbox. Only you have it, and only it can open the mail sent to your address.
Yes, you should use it. You can get an SSL certificate for your website to protect your customers. You can also use digital signatures to sign business contracts without using paper.
If you lose your private key, you can no longer open messages sent to your public key. You must tell the Certificate Authority to cancel your old certificate and issue a new one. This is why keeping your private key safe is so important.
No, they are different. A VPN creates a secure tunnel for your internet traffic. Public Key Infrastructure is the system that provides the certificates and keys used to make that tunnel secure. They often work together, but they serve different purposes.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts