.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

You understand the importance of keeping your sensitive data secret, especially when you send information over the internet. You want to know that only the right person reads your private message. How do secure systems like online banking and encrypted emails achieve this? They use a smart method called asymmetric encryption.
Asymmetric encryption, which people also call public key encryption, is a cornerstone of modern cybersecurity. It ensures safe communication because it solves a critical problem: sharing the secret needed to read the message. Unlike simpler methods, this system uses two separate keys for its job. This two-key approach makes it much more secure for sharing data with someone you might not have met before.
Let us explore this essential concept of public key asymmetric encryption. We will show you exactly how it works and why it plays a vital role in securing your digital life.
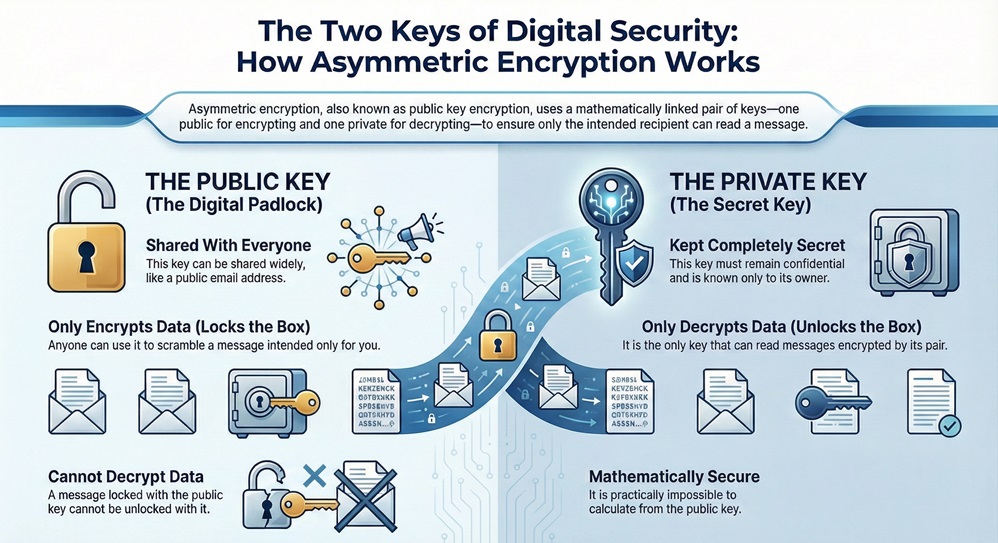
The whole idea of asymmetric encryption depends on a mathematically linked pair of keys. Every user in this system gets two distinct keys: a public key and a private key.
The public key is open for everyone to see. You can share this key widely, like a public email address. Anyone who wants to send you an encrypted message uses your public key to scramble the data. The important point is that the public key can encrypt information, but it cannot decrypt it. Think of it as a special digital padlock; anyone can put a lock on a box using the public key, but only one person holds the key to open it.
The private key is your secret. You must keep this key completely confidential. It is the only key that can reverse the encryption done by its paired public key. Since only you possess the private key, only you can read the message that others encrypted using your public key. The private key acts as the single key to open the padlock.
Asymmetric encryption relies on the fact that while the two keys are linked, it is practically impossible to calculate the private key if someone only knows the public key. This feature provides the essential security.
The process of how asymmetric encryption works is simple to understand. Let us use an asymmetric encryption example involving two parties, Alice and Bob.
In this way, the asymmetric encryption key pair ensures that even if the public key falls into the wrong hands, the data remains safe. The method ensures only the intended receiver can unlock the secret.
Now, the question arises: What is the underlying mathematics that makes this happen? Asymmetric encryption algorithms rely on mathematical problems that are simple to perform in one direction but extremely difficult to reverse. For example, the Rivest-Shamir-Adleman or asymmetric encryption RSA algorithm depends on the difficulty of factoring very large numbers.
Also Read: What Is Endpoint Detection & Response (EDR) in Cybersecurity?
You may ask, why is asymmetric encryption considered more secure than its alternative? The key advantage lies in key distribution.
Symmetric encryption uses a single, shared secret key for both encryption and decryption. This process is very fast, making it efficient for large amounts of data. However, how do the two parties securely share that initial secret key over an untrusted network like the internet? This key distribution problem is a significant weakness of symmetric asymmetric encryption models.
Asymmetric encryption eliminates this problem entirely. Since the key used for encryption (the Public Key) is openly shared and cannot decrypt, there is no need for a secret channel to distribute it. This makes secure communication scalable and much easier to initiate. The security of the data depends only on keeping the one private key confidential.
Because of this design, asymmetric encryption plays a vital role in establishing trust and security on the internet.
We now clearly differentiate between symmetric and asymmetric encryption. Both methods serve the purpose of data confidentiality, but they work on very different principles.
Key Usage
Speed and Efficiency
Key Distribution
| Basis for Comparison | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Single key for both encryption and decryption. | A key pair: Public Key for encryption, Private Key for decryption. |
| Speed | Faster; ideal for large data volumes. | Slower; computationally intensive. |
| Key Sharing | Requires a secure channel for key exchange. | Does not require a secure channel; public key is open. |
| Primary Use | Bulk data encryption (after a secure session is established). | Key exchange, digital signatures, and establishing secure channels (like SSL/TLS). |
| Known Algorithms | AES, DES, 3DES. | RSA, ECC, ElGamal. |
| Security Risk | The single key must remain secret; compromised key exposes all data. | Only the private key must remain secret. |
Also Read: Unified Threat Management (UTM): Key Security Functions
Several algorithms provide the complex mathematical framework for asymmetric encryption. These algorithms rely on mathematical problems that are easy to process in one direction but extremely difficult to reverse.
RSA (Rivest-Shamir-Adleman)
Asymmetric encryption RSA is one of the first and most widely used asymmetric encryption algorithms.
ECC (Elliptic Curve Cryptography)
Diffie-Hellman (Key Exchange)
These algorithms ensure that the complexity of how asymmetric encryption works remains a strong defense against digital attackers.
Asymmetric encryption has a dual function that goes beyond simple confidentiality. The asymmetric encryption key pair can be used in two ways.
1. Confidentiality (Encryption)
This is the standard use we already discussed.
2. Authentication and Integrity (Digital Signatures)
Asymmetric encryption also plays a vital role in confirming who sent a message and that the message has not changed.
This secondary use makes public key asymmetric encryption an indispensable tool for digital documents, code signing, and SSL/TLS certificates.
Also Read: Cloud Encryption Gateway (CEG): Keep Keys, Secure Data
You interact with asymmetric encryption every day. It underpins many secure communications on the internet.
You now have a deep understanding of public key asymmetric encryption and its vital role in digital security. We believe that robust security is not an option but a requirement in the modern digital world. By leveraging sophisticated, proven technologies like asymmetric encryption, our company ensures your data remains confidential and your communications are always authentic. You deserve the best defense against digital threats, and we deliver that security by design.
Secure Your Keys Reach our experts
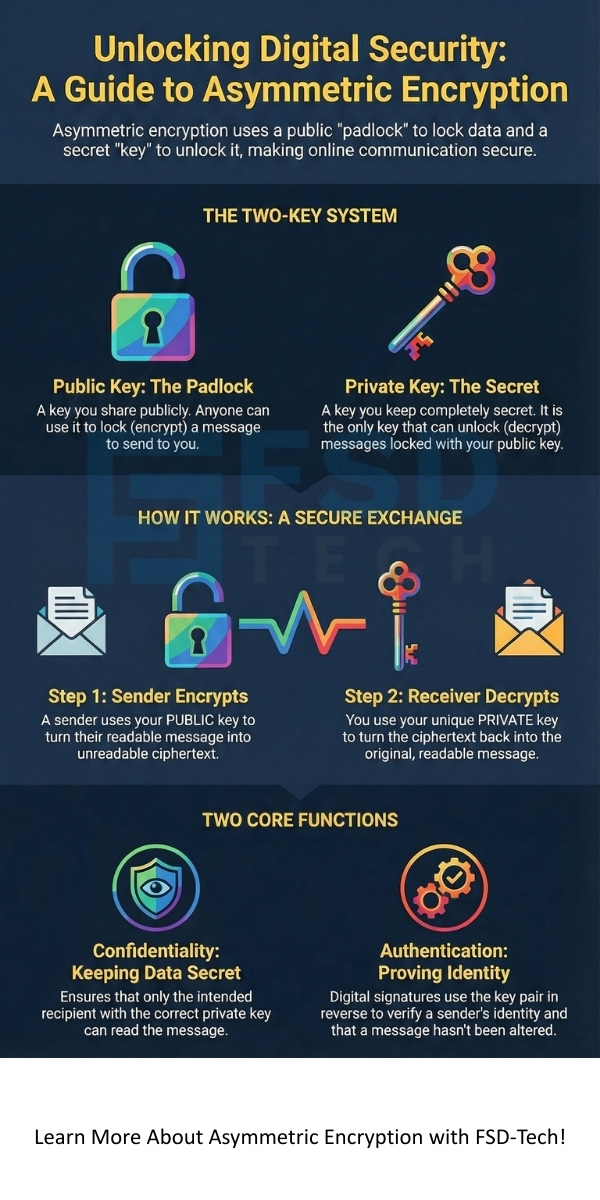
Asymmetric encryption is also known as public key encryption or public-key cryptography.
The most common algorithms providing asymmetric encryption are RSA and ECC (Elliptic Curve Cryptography). Diffie-Hellman also uses asymmetric principles for key exchange.
An accurate description of asymmetric encryption technology is a cryptographic system that uses a pair of mathematically linked keys—a public key for encryption and a private key for decryption—to secure data and verify digital identities.
In simple terms, how asymmetric encryption works is like this: You use an open, public padlock to lock your message. Only the person with the secret, private key can unlock the padlock and read the message.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts