
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered if someone is watching your data move across the internet? You send an email or log into a site and assume your data is safe. But what if a silent observer is catching every bit of that info? You might feel safe behind your screen. Yet, there are ways for others to see your private traffic. This happens through a process that experts call network sniffing. Do you want to know how people do this? Can you protect yourself from these hidden eyes? We will look at how this works and what it means for your privacy.
Network sniffing refers to the act of capturing and inspecting data packets as they move across a computer network. You can think of it as a way to listen to digital conversations. When you send data, it breaks into small pieces called packets. Network sniffing allows a person or a tool to grab these packets and read them.
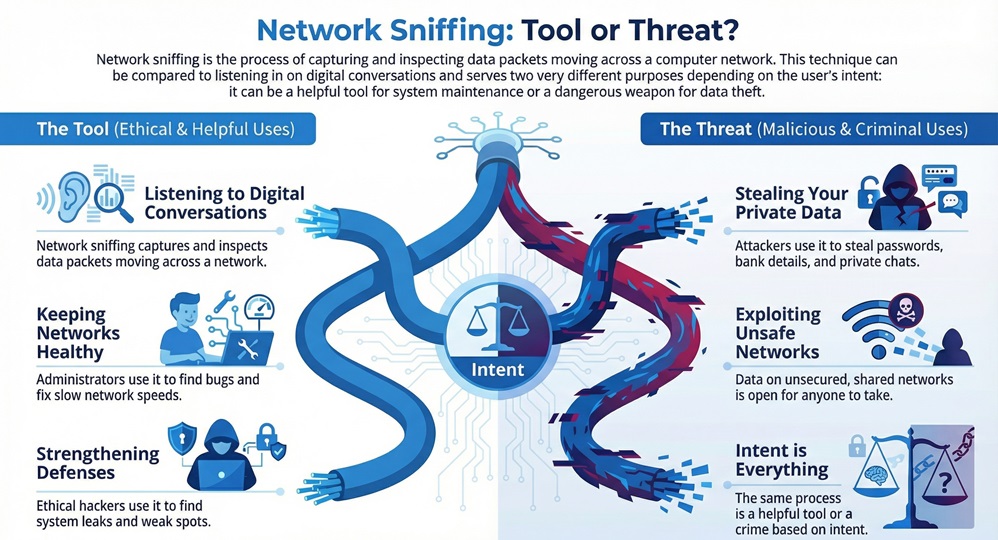
Network sniffing is a core part of how the internet stays healthy. It helps admins find bugs and fix slow speeds. But, in the wrong hands, it becomes a tool for theft. It is vital to know that this process works at the Data Link layer of the network. This is where physical hardware talks to the digital world.
Network sniffing in cyber security serves two main masters. Ethical hackers use it to test how strong a system is. They look for leaks or weak spots. On the other side, bad actors use a network sniffing attack to steal your passwords or bank details.
Network sniffing meaning changes based on intent. If you use it to fix your office Wi-Fi, it is a great tool. If a stranger uses it to read your private chats, it is a crime. Why is this so easy to do? Most data travels through shared spaces. If those spaces are not safe, your data is open for anyone to take.
To understand this topic, you must see the difference between active and passive methods.
| Basis for Comparison | Passive Network Sniffing | Active Network Sniffing |
|---|---|---|
| Network Type | Uses Hubs | Uses Switches |
| Detection | Very hard to find | Easier to spot |
| Method | Just listens to traffic | Sends packets to the network |
| Risk Level | Low risk for the sniffer | High risk of being caught |
| Hardware | Works with standard NIC | Needs special injection tools |
Network sniffing works by changing how your computer hardware sees data. Normally, a computer only looks at data meant for its own address. It ignores everything else. Network sniffing software tells the Network Interface Card (NIC) to enter "promiscuous mode."
Network sniffing in this mode means the NIC sees every single packet on the network. It does not matter who the packet is for. The card grabs it all. Once the hardware captures the packet, the software decodes it. It turns raw bits into words and images you can read.
How packet sniffing works depends on the network setup. On an old hub, every packet goes to every port. You just plug in and start reading. On a modern switch, the network is smarter. You have to trick the switch into sending you data. You might use ARP spoofing to do this. This forces the switch to think your computer is the router.
Also Read: What is an Access Control System (ACS) for your security?
Network sniffing tools are programs that make it easy to see traffic. Some are free and open-source. Others cost a lot of money and work for big companies. Do you know which tools the pros use?
Network sniffing software like Wireshark is the most famous. It lets you see every detail of a packet. It shows headers, payloads, and timing. Another tool is Tcpdump. This is a command-line tool. It is fast and works well on Linux systems.
Which of the following are network sniffing tools that you might encounter? Here is a list:
Also Read: What is Hash Function? Data Integrity and Security
Network sniffing is not just for hackers. It is a key part of IT work. Have you ever had a slow internet connection at work? Your IT team likely used network sniffing to find the cause.
Why network monitoring is important comes down to three things: speed, health, and safety. By looking at packets, admins see where the traffic jams are. They can see if one computer is using too much data. This keeps the whole system running fast for you.
It also helps find viruses. Some bad software sends data back to a hacker. A sniffer sees this strange traffic. It acts like an alarm. It tells the team that a device is sick. Without these tools, a virus could hide for months.
Network sniffing can be scary if you are the target. But you have power. You can take steps to hide your data. How do you stay safe on a public network?
Which is the best defense against network sniffing? The answer is encryption. When you encrypt data, it turns into a secret code. Even if a sniffer grabs the packet, they cannot read it. They only see random letters and numbers.
Network sniffing becomes useless when you use a VPN. A VPN creates a safe tunnel for your data. It wraps your traffic in a layer of strong security. Also, always look for "HTTPS" in your browser. This means your data is safe between you and the website.
Ways to stay safe:
Network sniffing attacks usually happen in stages. The attacker first gets onto your network. This is why public Wi-Fi is so dangerous. Once they are in, they start the software.
Network sniffing in an active attack might involve ARP poisoning. The attacker sends fake messages to your router. They want the router to send your data to them instead of the web. This is a very common way to steal login info.
How sniffing works in these cases is sneaky. You will not see a change in your speed. Your screen looks normal. But in the background, every site you visit is being logged. This is why you must never do banking on a network you do not trust.
Network sniffing allows us to see what is inside a packet. Every packet has three parts. There is the header, the payload, and the trailer.
The tools show you the header first. The header has the source and destination. It is like the address on an envelope. The payload is the actual data. This could be a piece of an image or a word from a chat. The trailer tells the receiving computer that the packet is over.
How packet sniffing works is by reading these parts one by one. If the data is not encrypted, the payload is clear. Anyone with a sniffer can see your messages. This is why modern apps use end-to-end encryption. It protects the payload from prying eyes.
Also Read: What is Security Information and Event Management (SIEM)?
Network sniffing relies heavily on the NIC. This is the hardware in your phone or laptop that talks to the router. Usually, the NIC has a filter. It says, "If this packet is not for me, throw it away."
Network sniffing software breaks this filter. It puts the card into a special state. In this state, the card keeps everything. This is the first step in any sniffing task. If your hardware does not support this mode, you cannot sniff the network.
Network sniffing is a powerful force in the digital world. It serves as a vital tool for those who maintain our systems. At the same time, it poses a real threat to those who do not take security seriously. You must understand that your data is only as safe as the network you use. By using encryption and staying alert, you can enjoy the web without fear.
Our team believes in a world where data is secure and private for everyone. We focus on providing you with the knowledge to stay safe in a complex world. Your security is our top priority. We are here to help you build a safer digital life with expert advice and the latest tools. Let us work together to keep your private information truly private.

Network sniffing is the process of watching and recording data as it moves through a network. It is like a digital wiretap.
Network sniffing is legal if you own the network or have permission. It is illegal if you use it to steal data or watch others without their consent.
Strong encryption is the best defense. Using a VPN and HTTPS ensures that sniffers cannot read your data even if they catch it.
Yes, network sniffing is very common on wireless networks. Attackers use tools like Kismet to catch packets out of the air.
Companies use these tools to find network errors. It helps them fix slow speeds and find security leaks before hackers do.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts