
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how a single weak password can bring down an entire corporate network? You might feel safe behind your firewall and antivirus software. However, hackers have a quiet way to steal secrets without even touching your servers. They use a trick that hides in plain sight within the very system that logs you in every morning. This method is called Kerberoasting.
Kerberoasting is a specific type of attack that targets the Kerberos protocol in a Windows Active Directory environment. It does not require special administrative rights to start. Any user on your network can try it. Do you want to know why it is so popular among cyber criminals? It is because the attack happens mostly offline where your security tools cannot see it.
In this guide, we will look at how this threat works. You will learn how to spot it before it causes damage. We will also talk about the best ways to protect your data. This is not just technical talk. It is about keeping your digital identity safe from clever thieves.
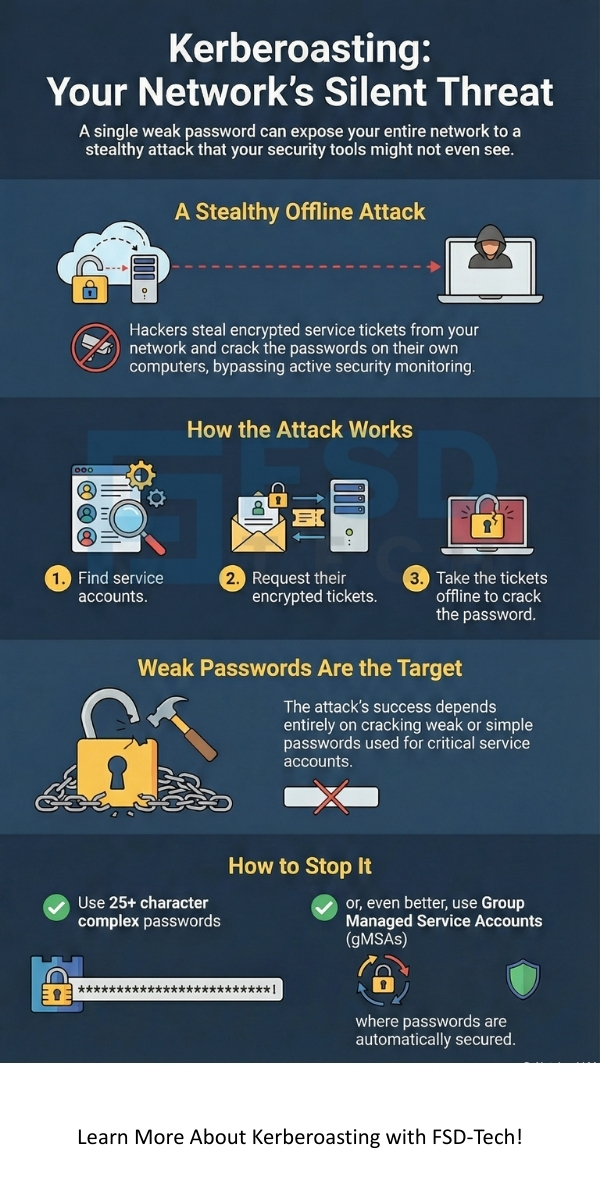
Kerberoasting is an attack where a hacker steals a service ticket from a network and tries to crack the password offline. The hacker looks for accounts that have a Service Principal Name or SPN. These accounts usually belong to services like SQL databases or web servers.
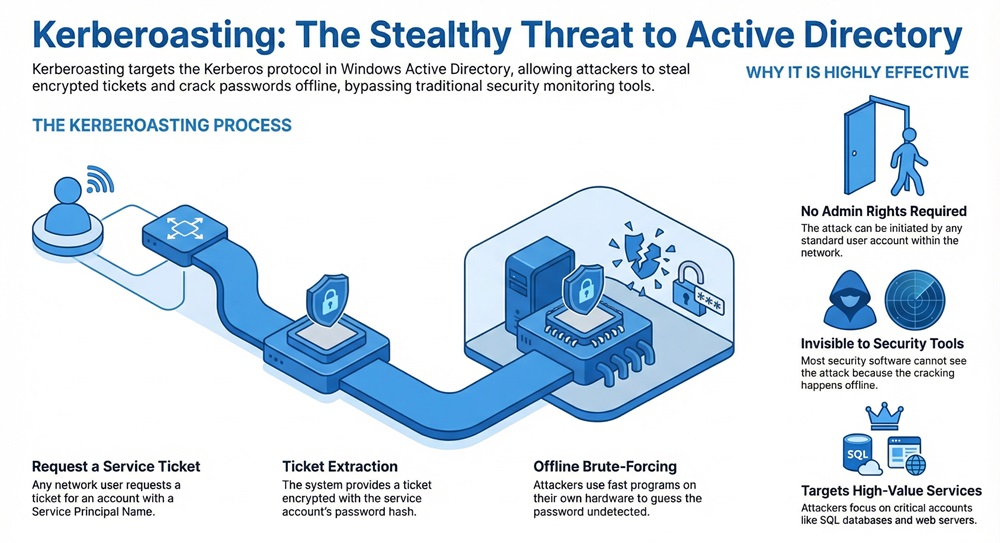
Kerberoasting exploits the way the Kerberos protocol hands out tickets. When you want to use a service, the system gives you an encrypted ticket. This ticket is encrypted with the password hash of the service account. The hacker simply asks for this ticket and then takes it to their own computer. They use fast programs to guess the password until they find a match.
It is helpful to compare this attack to other common threats. Many people confuse this with AS-REP Roasting. While they both target the same protocol, they work in different ways.
| Feature | Kerberoasting | AS-REP Roasting |
|---|---|---|
| Primary Target | Service Accounts with an SPN | User accounts without pre-authentication |
| User Rights Needed | Any valid domain user | No user login needed initially |
| Ticket Type | TGS (Service Ticket) | AS-REP (Authentication Response) |
| Visibility | Very low visibility | Easy to find in logs |
| Goal | Get the service account password | Get the user account password |
Kerberoasting works because of a design choice in Active Directory. The system wants to make it easy for users to access services. Because of this, any user can ask for a ticket for any service. The Domain Controller does not check if you actually have permission to use the service yet. It just gives you the ticket.
It relies on the fact that service tickets use the service's password for encryption. If that password is weak, a computer can guess it very quickly. Think about how many old service accounts might have simple passwords in your office. This makes it a gold mine for hackers.
Kerberoasting cannot happen without a Service Principal Name. An SPN is a unique identifier for a service instance. It links a service to a specific login account in the system. When a hacker scans the network, they look for these links.
Kerberoasting tools find these accounts easily. They look for accounts where the "servicePrincipalName" attribute is not empty. Once they find these names, they know exactly which accounts to target. These accounts often have more power than a regular user account, which makes them very valuable.
Also Read: What is Application Whitelisting in Cybersecurity?
Kerberoasting follows a simple path. It starts with a hacker getting onto a single computer in your network. They do not need to be an admin. They just need to be a regular user.
1. Finding the Targets
It begins with a search. The hacker uses scripts to list all accounts that have an SPN. They use tools like PowerView or simple LDAP queries. This step is quiet because looking up information in the directory is a normal part of how Windows works.
2. Requesting the Service Tickets
Kerberoasting then moves to the request phase. The hacker asks the Key Distribution Center or KDC for a Ticket Granting Service or TGS ticket. They ask for tickets for all the service accounts they found in the first step. The system sends these tickets back to the hacker's machine.
3. Extracting the Tickets from Memory
It requires the hacker to pull these tickets out of the computer's memory. They use tools to save the tickets to a file. These files contain the encrypted password data. At this point, the hacker can leave your network. They have everything they need on their own laptop.
4. Cracking the Password Offline
It reaches its final stage in a lab or on a powerful server. The hacker uses a tool like Hashcat or John the Ripper. These programs guess millions of passwords every second. If the service account used a simple password, the hacker finds it in minutes.
Kerberoasting is easy to do because many free tools exist for it. You can find these tools on sites like GitHub. Security researchers and hackers both use them.
Also Read: What is Biometric Authentication? Methods & Security Guide
Kerberoasting is hard to catch because it looks like normal traffic. However, you can find it if you know what to look for. You must watch your logs closely.
Monitoring Event Logs
Kerberoasting leaves a trail in the Windows Event Logs. You should look for Event ID 4769. This event happens when a user requests a service ticket. If you see one user asking for hundreds of tickets in a few seconds, it is likely an attack.
Kerberoasting detection also involves looking at the encryption type. Old encryption like RC4 is much easier to crack than newer AES encryption. If you see many requests using RC4, you should investigate immediately.
Using Machine Learning for Detection
Kerberoasting can also be spotted using smart software. Some new systems use machine learning to learn what normal behavior looks like. If a user suddenly starts acting like a hacker, the system sends an alert. This helps find attacks that humans might miss.
Kerberoasting is a serious threat, but you can stop it. Prevention is mostly about making the hacker's job too hard to finish.
Use Strong and Long Passwords
Kerberoasting depends on weak passwords. If your service accounts have passwords that are 25 characters or longer, a hacker cannot crack them. You should use random characters and symbols. Never use the same password for two different services.
Implement Managed Service Accounts
Kerberoasting becomes much harder if you use Group Managed Service Accounts or gMSA. These are special accounts where Windows handles the password for you. The passwords are very long and change automatically every 30 days. Hackers cannot crack these easily.
Move to AES Encryption
Kerberoasting is much faster if you use the old RC4 encryption. You should change your settings to only allow AES128 or AES256. These are much stronger. It takes much more computer power to crack a ticket that uses AES.
Also Read: What is Cloud Virtual Private Network (VPN)?
Kerberoasting can lead to a total network takeover. Once a hacker has the password for a service account, they can act as that service. If the service is a database, they can steal all your customer data. If the service has admin rights, they can create new users or delete your backups.
It often serves as a stepping stone. A hacker starts as a regular user and then moves to a service account. From there, they might try to get a Domain Admin password. This is why you must take this threat seriously. It is a key part of many big data breaches you see in the news.
Kerberoasting is a clever way for hackers to move through your network. It turns a simple user login into a powerful tool for theft. By understanding how it works, you can take the right steps to lock your digital doors. Always remember that your security is only as strong as your weakest password.
At FSD-Tech, we care about your safety above everything else. We work hard to stay ahead of these threats so you do not have to worry. Our team focuses on giving you clear advice and strong tools to protect your business. We believe that every client deserves a secure environment where they can grow without fear.
Prevent Kerberoasting Contact FSD-Tech today
It uses the fact that service tickets are encrypted with the service account's password hash. This allows for offline cracking.
No, you do not. Any regular domain user can request these tickets and start the attack.
Most basic antivirus tools will not stop it. This is because requesting a ticket is a normal Windows function. You need special tools that watch for weird behavior.
Yes, it is still very common. Many companies still have old accounts and weak passwords that make this attack easy.
If the password is short, it can take seconds. If the password is very long and complex, it could take years.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts