.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Managing a global network often feels like a puzzle with missing pieces. You might wonder if there is a way to see everything in one place without the stress. In early 2025, a big change arrived that fixed many old problems for tech teams. This update changes how you work with your sites and security rules every day.
The new CMA interface is broken down into six intuitive tabs: Home, Network, Access, Security, Resources, and Account. Here’s how each one supports key jobs:
This is your mission control. It offers live dashboards for: - Application Analytics: Spot latency issues or app-specific slowness - Experience Monitoring: Get a real-time view of user, app, and site performance - Threats & XDR Stories: Understand the full path of a potential breach
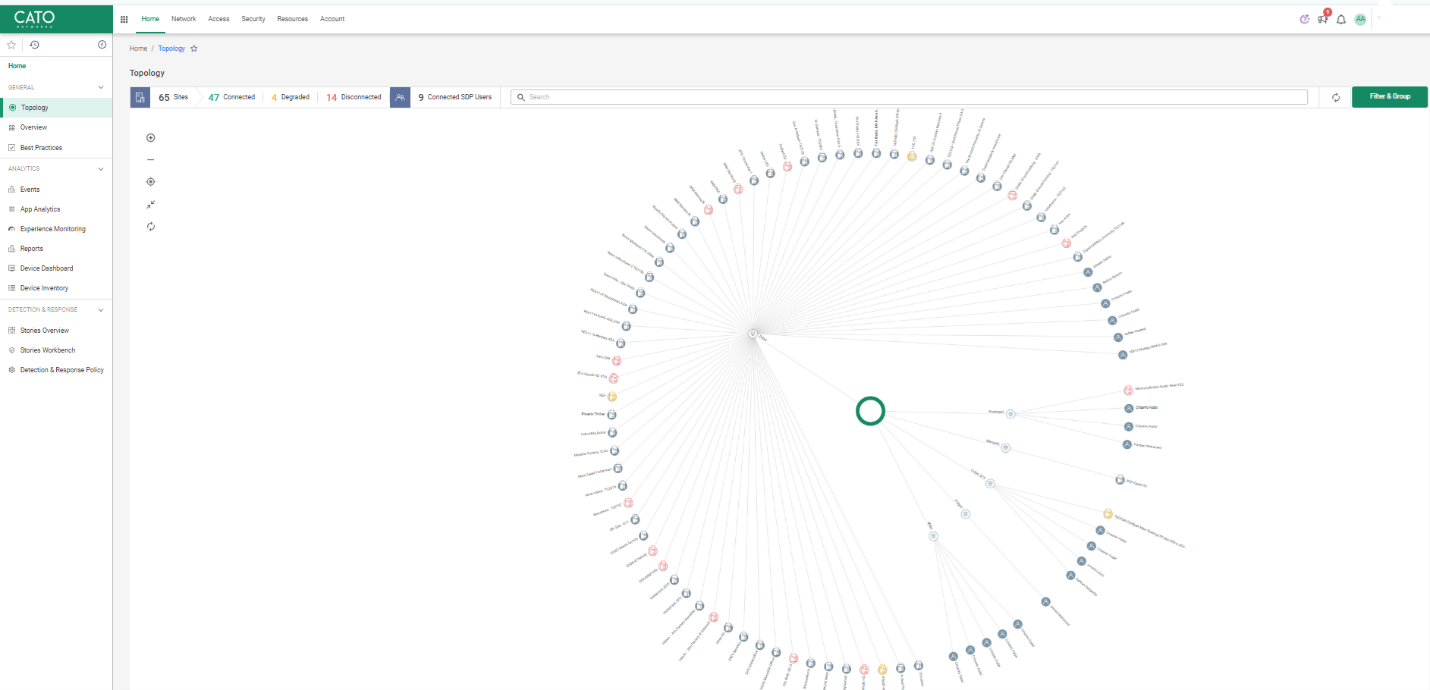
Pro tip: Use Home > Experience Monitoring when users complain about slowness—it saves time compared to checking each site manually.
This tab is for setting up and maintaining your infrastructure. You’ll: - Add and manage Sites (Socket, vSocket, or cloud-only) - View and edit your Topology and routing - Use tools like Ping, Traceroute, and Site Snapshots for troubleshooting
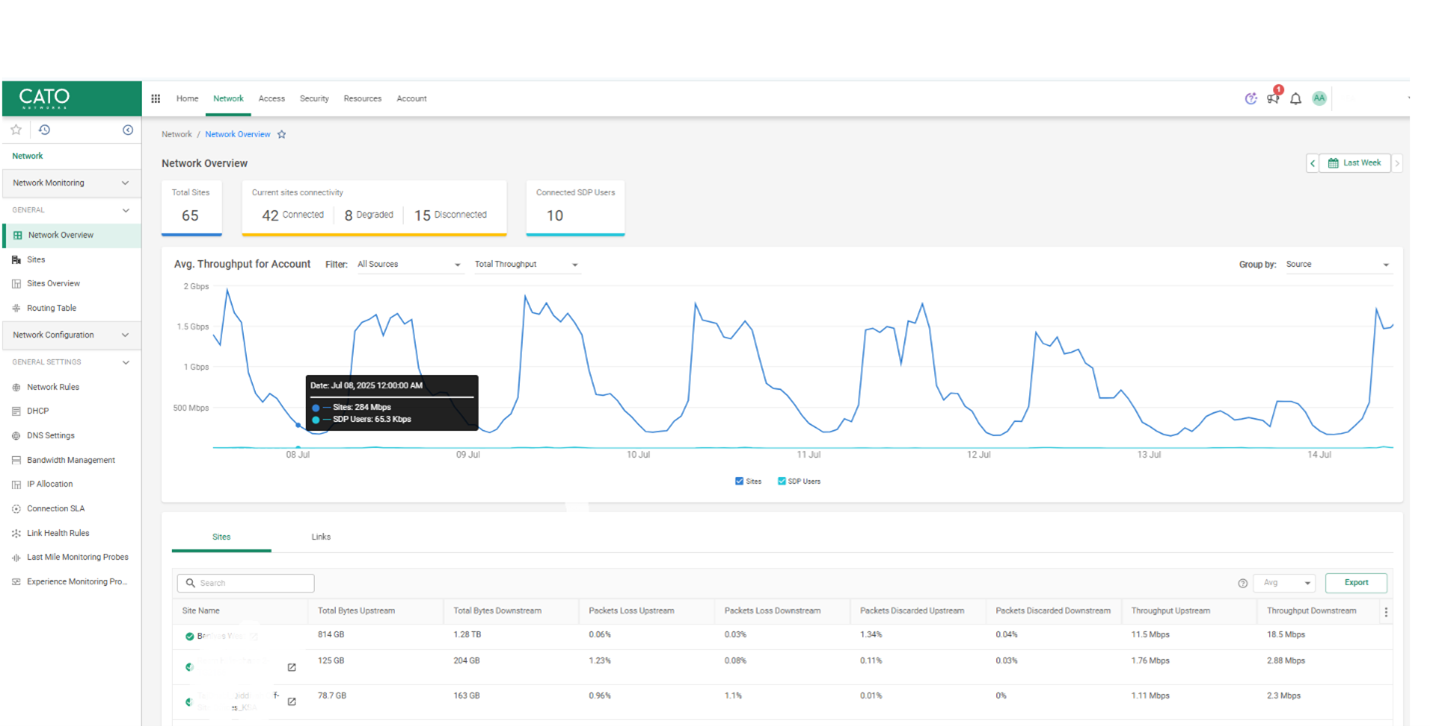
Use case: Just added a branch office in Dubai? Create a site, assign PoPs, and validate connectivity within minutes.
Manage users, clients, and Zero Trust policies: - Onboard remote users with Cato Clients (Windows, macOS, iOS, Android) - Integrate with IdPs (Azure AD, Okta, etc.) - Monitor live sessions to spot anomalies
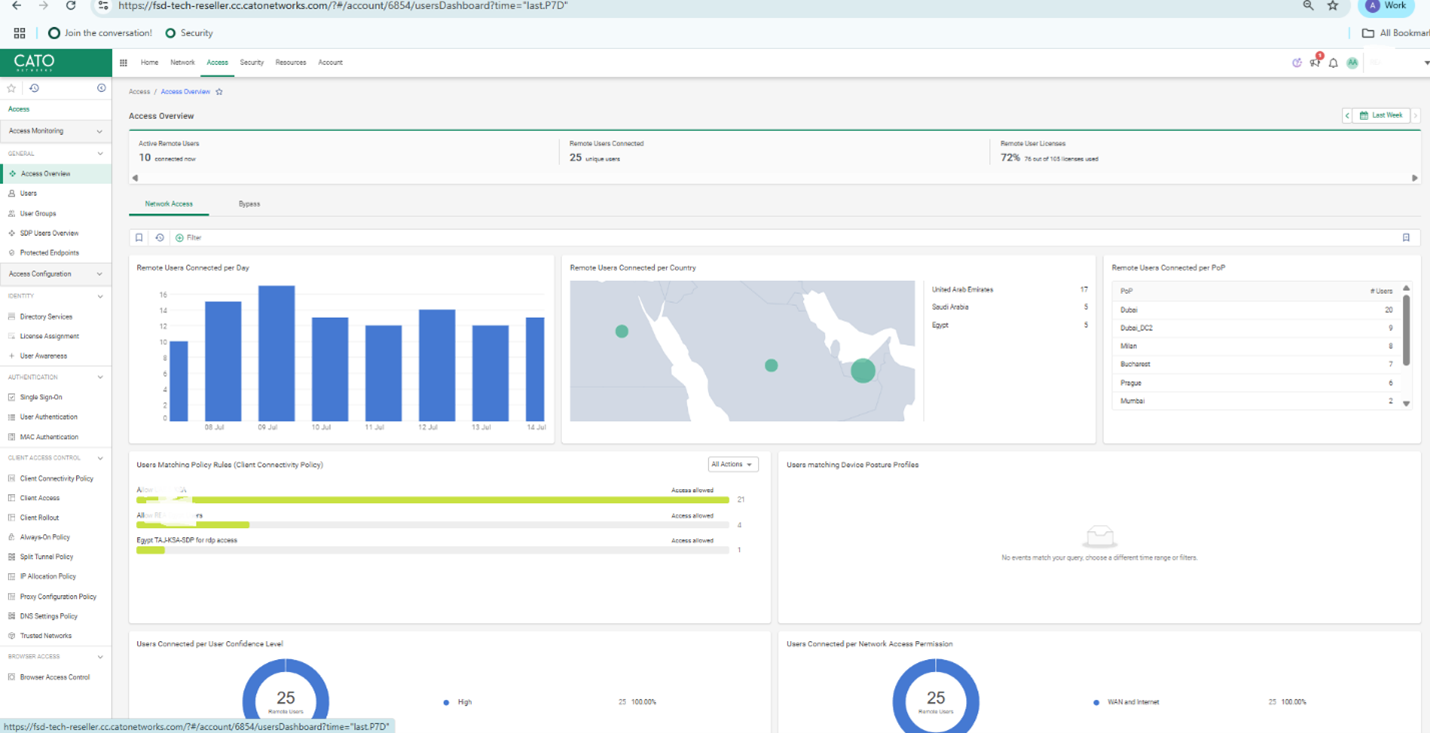
Real-world tip: If you see spikes in client disconnects, check the “Client Sessions” view to identify patterns.
All your protection rules in one place: - Set Internet and WAN Firewall rules - Enable IPS, Anti-Malware, DLP, and Tenant Controls - Review blocked flows and drill into threats directly
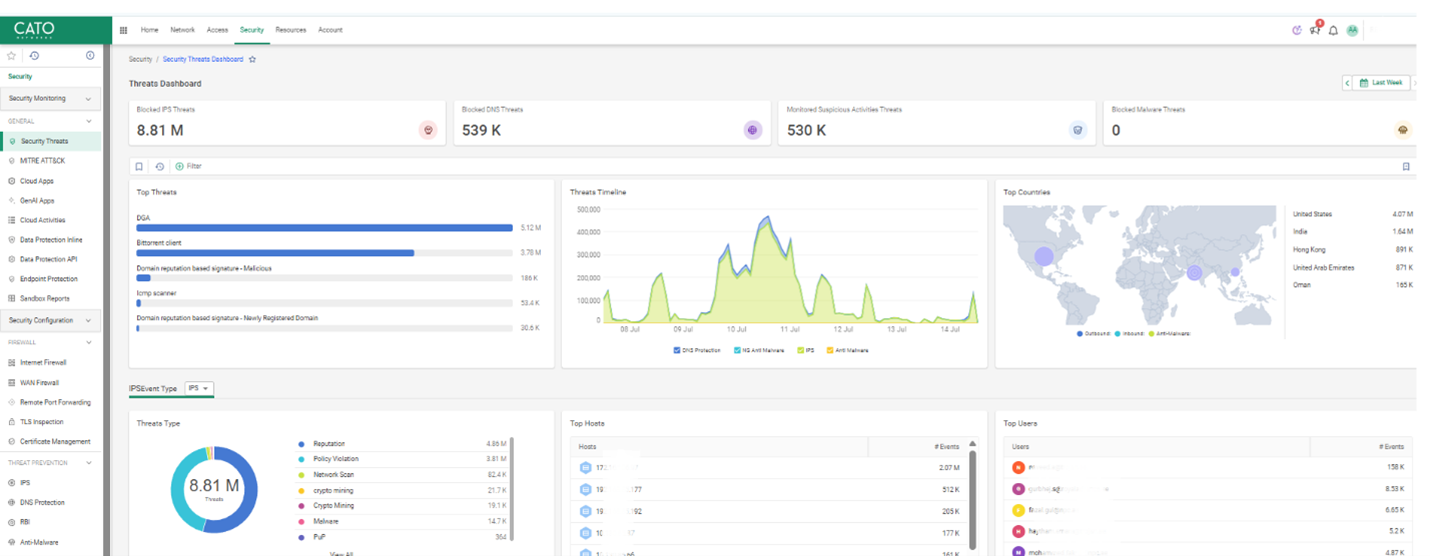
Example: After a recent phishing alert, use the Threat Event Log to trace how the payload attempted to travel internally.
Think of this as your policy toolkit: - Define shared objects (IPs, ports, groups, apps) - Manage App Catalogs for CASB enforcement - Reuse policies across the environment

Guidance: Use consistent naming for objects to avoid duplication across admins.
Configure access and governance settings: - Set up RBAC and audit trails - Customize SSO and branding - Generate API tokens and assign licenses
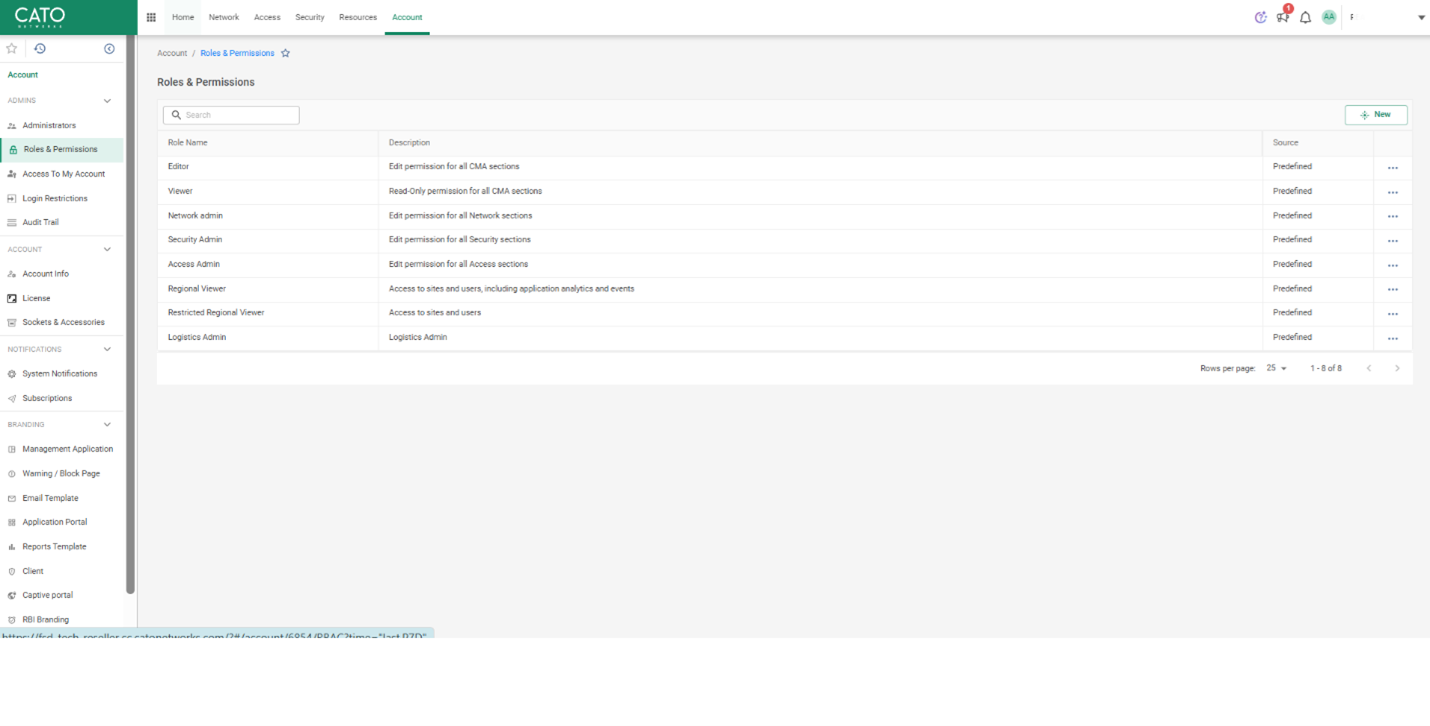
Best practice: Regularly audit role permissions under “Users & Roles”—especially before handing over projects to new IT staff.
Also Read: Preventing Insider Threats and Unauthorized Access with Cato SASE’s Context-Aware Security
Let’s say you’ve just been assigned to deploy a new office branch. Here’s a quick flow that mirrors how many admins operate:
This experience-first interface reduces steps, eliminates guesswork, and helps you complete onboarding in under an hour.
Follow this sequence to get oriented quickly:
Log in to your CMA portal and start with the Home tab. Familiarize yourself with analytics and experience dashboards. Try clicking through site tiles and using filters. From there, move sequentially through each tab and note how workflows naturally guide you. Click Here To Know More
Also Read: Reducing Network Latency and Enhancing User Experience Globally with Cato SASE
Yes. Go to Account > Settings and toggle the “Use legacy navigation” option.
Go to Access > Client Sessions to view real-time user data.
These are available under Home > Threats or Security > Event Log.
Admin settings can be found under Account > Users & Roles.
Yes, click the Help icon at the top-right corner to access AI-powered assistance.
The onboarding process is simplified through hands-on guidance from FSD-Tech, which aligns the CMA’s tabbed interface with real-world IT workflows to help admins get productive from day one.
Absolutely. With FSD-Tech’s implementation support, shared objects like IP groups, app lists, and port sets are organized for consistency—reducing policy duplication and simplifying management inside the Resources tab.
New branches can be brought online quickly with help from FSD-Tech, who guide the full process—from site creation and bandwidth setup to client deployment and initial security policy application.
FSD-Tech uses built-in tools like Experience Monitoring and Client Sessions in CMA to quickly identify patterns behind latency or frequent disconnects, saving admins from time-consuming manual checks.
Zero Trust access is enforced by integrating identity providers and applying role-based controls—tasks that FSD-Tech handles through the CMA’s Access and Security tabs to secure every user and device.
Yes. FSD-Tech enables real-time threat tracking by leveraging dashboards under Home > Threats and the Security > Event Log, helping teams drill into alerts and understand how threats propagate.
Admin permissions, SSO, and audit settings are configured as part of FSD-Tech’s deployment process using the Account tab, ensuring secure access control and governance from day one.
Troubleshooting tools such as Traceroute, Ping, and Site Snapshots are used by FSD-Tech to quickly isolate network issues, verify PoP connectivity, and resolve performance degradation.
Yes. FSD-Tech adapts CMA workflows to match enterprise IT structures, whether centralized or distributed, ensuring the platform fits into how your teams already work.
After setup, FSD-Tech delivers custom runbooks, alerting strategies, and admin coaching to ensure your team is fully equipped to manage the environment confidently through the CMA interface.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts