
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever walked past your favorite clothing store and suddenly received a discount coupon on your phone? It feels like the store was waiting for you. This is not a coincidence. It is a smart strategy that helps businesses talk to you at the right time. You might wonder how a store knows you are nearby. The answer lies in a clever tool that connects the digital world to physical locations. Let us explore this tool and see how it changes the way we use technology every day.
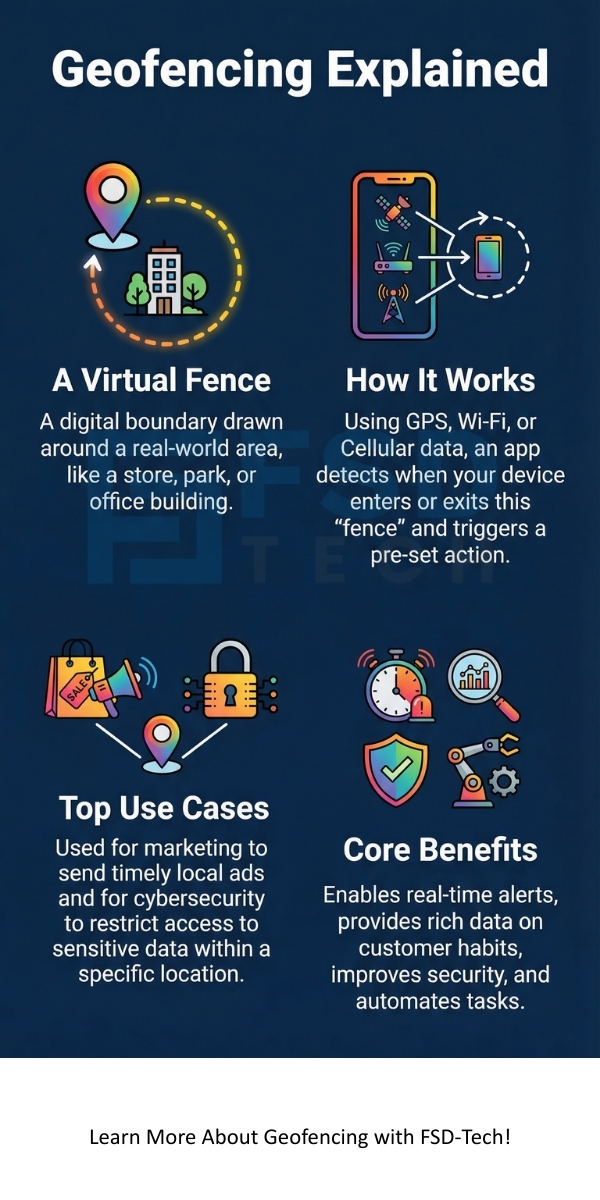
Geofencing meaning refers to the use of a digital boundary around a specific location. Imagine drawing a circle on a map. When a person with a mobile device enters or leaves that circle, it triggers a response. This response could be a text message, an app notification, or a social media ad. Geofencing creates a virtual perimeter for real-world areas.
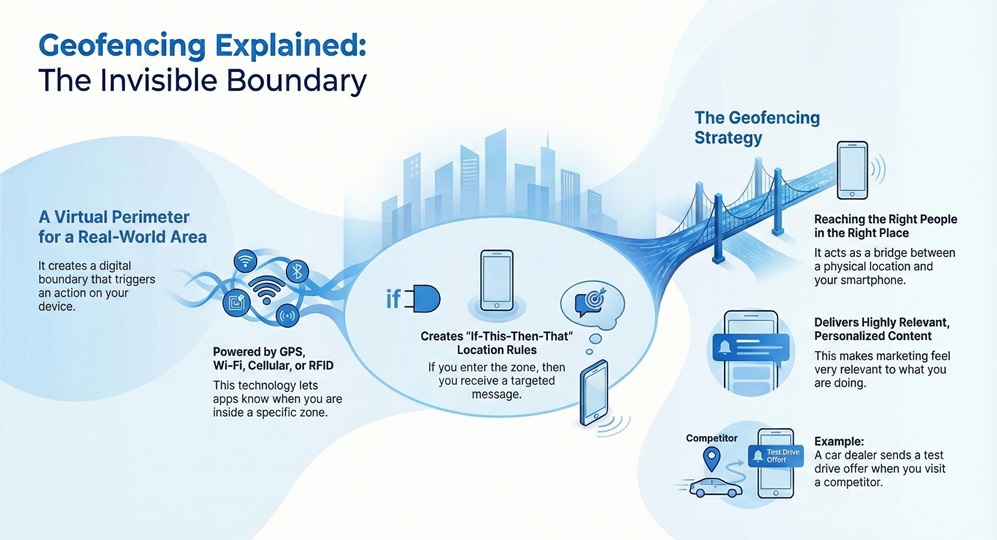
Geofencing uses global positioning system (GPS) data or cellular data to work. It can also use Wi-Fi signals or Radio Frequency Identification (RFID). This technology helps apps know when you are in a certain zone. In simple terms, it is a way to set up "if-this-then-that" rules based on location.
Geofencing strategy involves more than just drawing circles. It is about reaching the right people in the right place. Businesses use it to catch your attention when you are near their shop. It acts as a bridge between a physical space and your smartphone.
It allows companies to send personalized content. For example, a car dealership might send an invite for a test drive when you visit a competitor nearby. This makes the marketing feel very relevant to what you are doing. Now, the question arises, how does this differ from other location tools?
| Basis for Comparison | Geofencing | Geotargeting | Beacon Technology |
|---|---|---|---|
| Primary Technology | GPS, Wi-Fi, Cellular | IP Address, User Data | Bluetooth (BLE) |
| Range | Large (meters to kilometers) | City or Zip Code level | Very Short (under 50 meters) |
| Precision | Medium | Low to Medium | High (Indoor accuracy) |
| Main Use | Entering/Exiting a zone | Reaching specific demographics | Precise indoor tracking |
| Battery Impact | Moderate | Low | Low |
Also Read: What is Network Access Control (NAC)? with Process
Geofencing define helps us see it as a location-based service. In this service, an app or software uses location data to trigger a pre-programmed action. This action happens when a mobile device enters or exits a virtual boundary. These boundaries are called geofences.
It can be of different shapes. Some are simple circles around a point. Others are complex polygons that follow the exact lines of a building or a park. This flexibility allows for very specific targeting. Let us now discuss the technology that makes this possible.
Geofencing technology starts with the hardware in your pocket. Your smartphone constantly talks to satellites and cell towers. This tells the device exactly where it is on the planet. The geofencing software compares your location to the boundaries set by the user.
It relies on three main parts. First, you need a management platform to set the boundaries. Second, you need a mobile app that the user has installed. Third, you need the location services on the device to be active. When these three parts work together, the system can trigger alerts instantly.
Geofencing follows a clear sequence of events. First, an administrator creates a virtual fence in a software portal. This fence covers a specific area like a mall or an airport. Second, the software defines the action that should happen. This might be showing an ad or logging a work time.
Geofencing then waits for a device to cross the line. When you carry your phone into the fenced area, the app notices the change. It sends a signal back to the server. The server then executes the action immediately. In this way, the process is fast and automatic.
Also Read: What is Role-Based Access Control (RBAC)?
Geofencing in marketing focuses on increasing sales by being local. It helps brands talk to customers who are already in the neighborhood. This is very powerful because it targets people who can actually visit the store right now. It reduces the waste of showing ads to people who are too far away.
It also helps with "conquesting." This is when you set a fence around a competitor's store. If a customer goes there, they get a message from you instead. This is a very bold way to win new business. Does this really help the customer? Yes, because they get better deals and useful information.
Geofencing marketing offers many benefits for local shops. It provides high levels of engagement. People are much more likely to click an ad if it is for a shop they are standing next to. It also provides great data. You can see how many people walked into your store after seeing an ad.
It helps you understand customer habits. You can see which areas your customers visit most often. This helps you choose the best spots for new stores or billboards. It makes your marketing budget work much harder.
Geofencing in cyber security protects data by using location. It acts as a digital lock for sensitive information. A company can set a geofence around its office. This ensures that employees can only access certain files while they are inside the building.
It helps prevent remote hacking. If someone tries to log in from another country, the system can block them automatically. It adds a physical layer to digital safety. This is very important for banks and government offices. In this section, we see how location keeps us safe.
Geofencing cost depends on how many people you want to reach. Most providers charge based on "CPM," which means cost per thousand views. Usually, this price stays between $4 and $15. The more specific you want to be, the more you might pay.
It also involves setup fees. Some platforms charge a monthly fee to use their software. Others take a percentage of your total ad spend. You should also think about the cost of making the ads. All in all, it is often cheaper than traditional TV or radio ads.
Also Read: What is Attribute Based Access Control (ABAC)?
Geofencing technology provides many advantages across different fields. In logistics, it helps managers know when a truck arrives at a warehouse. In human resources, it helps track when employees arrive at a job site. It automates tasks that used to take a lot of time.
It also improves the user experience. Smart homes use it to turn on lights when you drive into your driveway. It makes life easier by doing things for you without you asking. The following list shows some key benefits:
Geofencing is not perfect. It can drain the battery of a phone if the app checks the location too often. If the GPS signal is weak, like inside a large metal building, the geofence might not trigger. This can lead to missed opportunities.
It also requires the user to give permission. If a user turns off their location services, the system cannot see them. There are also privacy concerns to keep in mind. You must be transparent with your users about how you use their data.
Geofencing marketing works best when you keep the fence small. If your fence is too large, you might message people who are too far away to visit. You should also make your message very clear. Give the user a reason to act right now.
It requires a strong call to action. Tell the user exactly what to do. Use phrases like "Visit us now for 20% off" or "Show this message at the desk." It is also smart to test different messages to see what people like most. Let us now look at some frequently asked questions.
Geofencing is a powerful tool that connects businesses with people in a meaningful way. It turns location data into a conversation. Whether you are trying to sell a product or protect a secret, this technology offers a smart solution. It focuses on the most important factor in any interaction: being in the right place at the right time.
At our company, we believe in using technology to build better relationships. We value your trust and focus on your success. Our team works hard to make sure every digital boundary we build leads to a real-world win for you. We are here to help you navigate the world of location-based tools with ease and honesty.
Boost Your Local Reach Reach our experts
Geofencing uses a virtual border to trigger an action for anyone inside. Geotargeting delivers content to people based on their location plus other factors like age or interests.
Geofencing that uses GPS often struggles indoors. However, if the system uses Wi-Fi or RFID, it can work very well inside malls or large offices.
Geofencing is legal as long as you follow privacy laws. You must ask users for permission to track their location. You also need to protect the data you collect.
Geofencing usually requires an app to be installed on the phone. However, some mobile web ads can use location data through the browser.
Geofencing circles for retail are usually small. Most experts suggest a radius of about 500 feet to 1,000 feet for the best results.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts