
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

Hello! Have you ever wondered how all the devices in your office or home talk to each other so fast? The truth is, a network switch is nothing but the essential component that makes this communication possible. It plays a vital role in building and managing local computer networks. You, the reader, need to understand this device because it directly affects your internet speed and network stability.
We will not immediately reveal all the secrets of network switching. First, let us build a solid understanding of this core networking component. We aim at simplifying this complex topic, helping you grasp exactly what does a network switch do and why it is so crucial. By the end, you will know how to pick the right ethernet network switch for your specific needs.
A network switch can be understood as a networking hardware device. This device connects multiple devices on a computer network. Put it another way, a switch is a central meeting point for all your wired network devices.
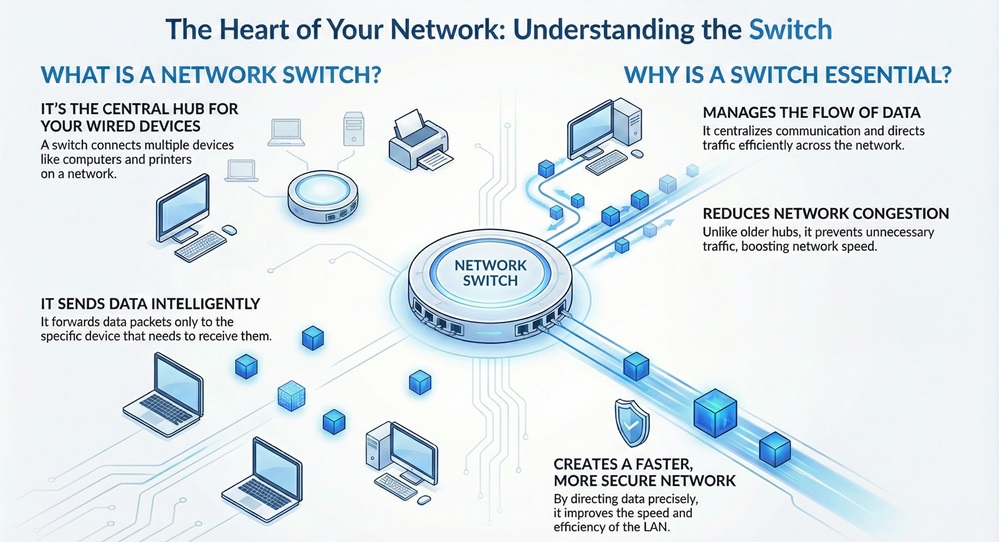
The switch works on the principle of receiving a data packet from one connected device and then forwarding that packet only to the device for which it is specifically intended. This process ensures efficient use of network bandwidth.
What is the purpose of a network switch? The primary goal is to centralize communication. Before switches, devices like hubs would broadcast data to every device. This method created a lot of unnecessary traffic and reduced network speed.
A network switch solves this problem. It aims at providing a faster, more secure, and more efficient way for devices to communicate within a Local Area Network (LAN). A typical network switch helps in:
Also Read: What Is an L3 Switch? L2 vs L3 & Why You Need Layer 3?
To fully appreciate the network switch, let us now understand how it differs from similar networking hardware. We will focus on the Hub and the Router. Always start with clear comparison charts when contrasting concepts.
| Basis for Comparison | Network Switch | Hub | Router |
|---|---|---|---|
| Primary Function | Connects devices within a single LAN and manages data flow. | Connects devices within a single LAN; broadcasts all traffic. | Connects different networks (LANs and WANs); routes data between them. |
| How It Works | Uses MAC addresses to send data to a specific port. | Simply repeats data signal to all ports indiscriminately. | Uses IP addresses to send data to different networks. |
| Data Transmission | Unicast (one-to-one), Multicast (one-to-many), Broadcast (one-to-all). | Broadcast (one-to-all) only. | Routing between networks. |
| OSI Layer | Works mainly at Layer 2 (Data Link) and sometimes Layer 3 (Network). | Works at Layer 1 (Physical). | Works at Layer 3 (Network). |
| Network Efficiency | High efficiency; reduces collisions and bandwidth waste. | Very low efficiency; causes high collision rates. | Moderate; optimizes path selection for inter-network traffic. |
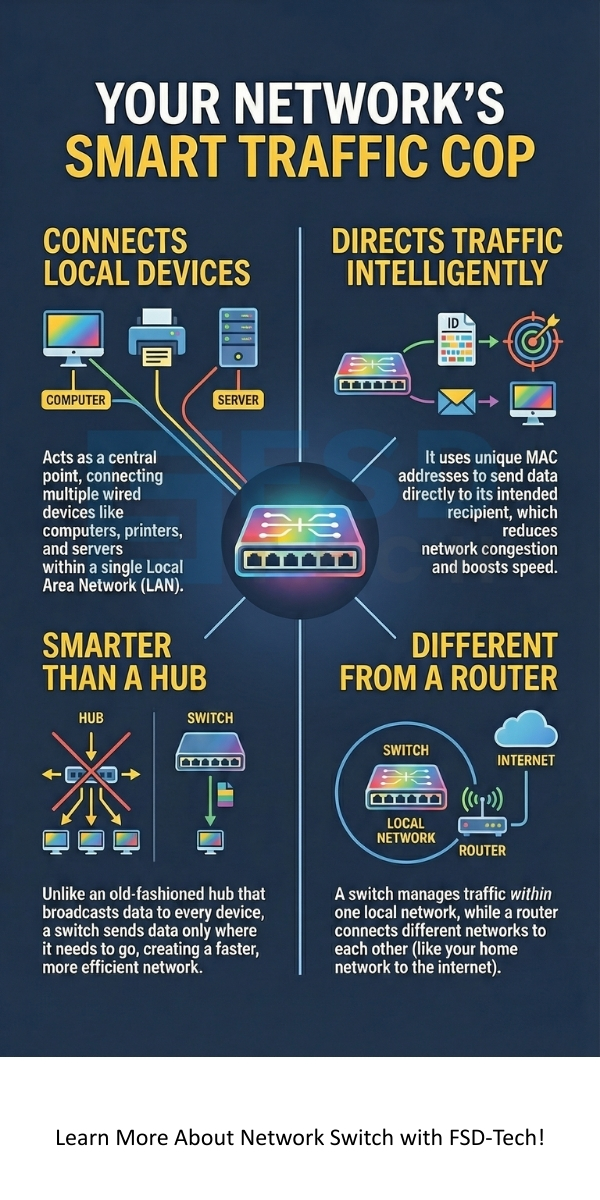
Now, the question arises, how network switch works to achieve such efficiency? The entire operation is based on MAC addresses (Media Access Control addresses). Each device connected to a network has a unique MAC address that permanently identifies it.
The Learning Process of a Network Switch
When you power up an ethernet network switch, it is essentially an "empty book." It must learn where each device is located. This is the learning process.
Also Read: What is Social Engineering? Types, Examples & Prevention
The Forwarding Process: Directed Traffic
Once the network switch builds its MAC table, it begins the crucial forwarding process.
The switch implements this process so as to minimize network collisions and maximize throughput. This method is the fundamental difference between a smart network switch and a simple hub.
The modern market offers many types of network switches. Knowing the distinctions helps you choose the right device for your network needs. How many types of network switch exist? We generally classify them based on their management capabilities and their functionality.
1. Based on Management
2. Based on Functionality
3. Based on Power
A common question that arises is about the term "wifi network switch." It is important to clarify this terminology.
A network switch deals only with wired connections using Ethernet cables. Wi-Fi is the technology that uses radio waves for wireless communication.
So, while there is no device called a "wifi network switch," the wired switch is a vital part of the network infrastructure that the Wi-Fi system relies on. Simply put, the ethernet network switch gives the WAP a wired connection to the internet.
Also Read: What is a Network Interface Card? How Does NIC work?
Sometimes you face a situation when network is not working. A problem with the network switch or its connections is often the cause. Here are some common switch-related issues:
The solution tends to be simple: start by checking all your physical cables and then restarting the switch to clear temporary errors.
All in all, the network switch stands as the critical foundation of any modern local network. You now understand that it is nothing but an intelligent device. It moves beyond simply connecting devices; it actively manages data flow by using MAC addresses to direct traffic precisely where it needs to go.
This efficiency is why your data transfers are fast and your network remains stable. Whether you need a simple unmanaged switch for your home or a powerful, configurable ethernet network switch for your business, selecting the right one directly impacts your performance.
Thus, we assure you that choosing a reliable network switch is the single best way to maximize your wired network's speed and efficiency. We are here to ensure your network infrastructure supports your goals.
Secure Your Network Reach our experts
So, with the above discussion, we can say that the network switch is the silent, essential powerhouse of any wired network.
A switch connects devices within a single network (like your office LAN) using MAC addresses. A router connects different networks (like your home network to the internet) using IP addresses. The router acts as the network's gateway, while the switch acts as the local traffic cop.
A good quality network switch does not slow down your internet. Modern switches operate at high speeds, often Gigabit Ethernet (GbE) or faster. They actually speed up your local network by efficiently directing traffic, thereby reducing congestion and collisions.
Yes, you can certainly connect network switches together. This action is called stacking or cascading. It allows you to expand the number of ports available for your devices. You use a standard Ethernet cable (or a special stacking cable) to connect a port on one switch to a port on the next.
For a small business, a network switch enables all computers, servers, printers, and VoIP phones to share resources and the internet connection efficiently. It provides the stable, high-speed wired backbone that business operations rely on.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts