
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

A Cloud Encryption Gateway (CEG) is an on-premises or cloud-based security enforcement point that sits between your organization's users and their cloud service provider (CSP). A CEG provides essential functions like encryption, tokenization, and centralized key management for data before it leaves your network perimeter. This security layer is vital because it gives you control over your sensitive information, even when it resides in an external, shared cloud environment.
It consists of several essential components working together to protect your cloud data. The two essential components are the encryption engine and the policy enforcement module. It also relies on a secure connection, often using a proxy server approach, to inspect and manage data traffic. Cloud encryption gateways connect your security policies to the cloud, ensuring compliance and data protection, a critical need in today's multi-cloud world.
To know more about Cloud Encryption Gateways, their functions, benefits, and how they secure your data in the cloud, read below. We will discuss the working mechanism and the key advantages of using a CEG solution in detail along with the core components.
A Cloud Encryption Gateway (CEG) can be understood as a security tool or service that intercepts data traffic moving between an enterprise's local network and a cloud service. This solution encrypts or tokenizes the data before it is uploaded to the cloud, ensuring that the cloud data is always protected by your organization's security controls.
Cloud encryption gateways act as a critical control point. They are the gatekeepers that ensure your data security policies are enforced before the information reaches the potentially less secure shared public cloud infrastructure. This process is essential for maintaining data privacy and regulatory compliance, especially for highly sensitive information. It must be noted that the CEG solution manages the encryption keys, which are vital for decryption, keeping them separate from the data itself and under your direct control.
In simple words, the cloud encryption gateway means that even if a threat actor accesses your data in the cloud, they will only find unreadable, scrambled information because it was secured before leaving your control. This is a huge benefit for businesses leveraging Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). Cloud encryption gateways simplify the complex task of securing data across diverse cloud environments.
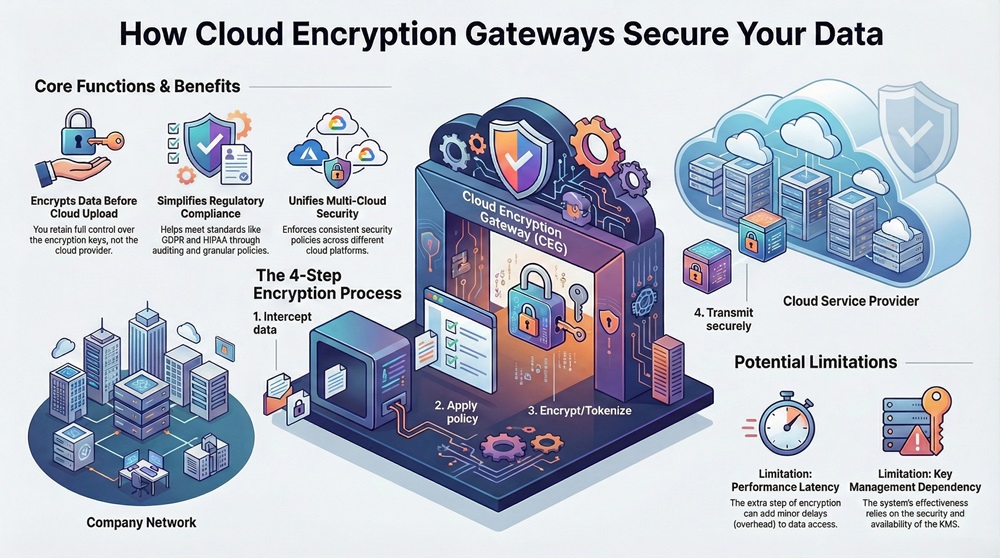
Let us now understand the key functions of the cloud encryption gateway. The primary function is to secure data-at-rest in the cloud. However, this technology also helps with data leakage prevention and visibility into cloud services usage. Simply put, a CEG solution gives you back the security control you might feel you lose when moving to the cloud.
Also Read: Cloud Security Posture Management: CSPM Vs CWPP
Cloud encryption gateways matter because they bridge the security gap created by the shared responsibility model of cloud computing. As we know that, the cloud provider secures the infrastructure, but you, the user, are responsible for securing your data within that infrastructure. So, how do you manage that?
Cloud encryption gateways give you complete ownership of the encryption process and the crucial encryption keys. This separation of duties is a fundamental security principle. If the cloud provider holds the keys, a large-scale breach on their side could expose your data. By maintaining the keys, you ensure that only your authorized systems can unlock the information, a vital point for any organization.
Moreover, the CEG solution helps solve major compliance challenges. Regulatory frameworks like HIPAA, GDPR, and CCPA require strict controls over personal and sensitive data. Since cloud encryption gateways offer detailed auditing and policy enforcement, they become indispensable tools for meeting these regulatory demands. This allows businesses to confidently adopt cloud storage and cloud services without fear of compliance violations.
Cloud encryption gateways are also essential for simplifying the security management of multiple cloud platforms. If you use AWS for one application and Azure for another, managing different encryption methods is complex. The CEG solution provides a single, uniform point for all your security policies, dramatically simplifying operations and reducing the chance of human error. It is also important to consider the underlying network security that a CEG provides.
| Basis for Comparison | Cloud Encryption Gateway (CEG) | Traditional VPN/Proxy |
|---|---|---|
| Meaning | Specialized security control that encrypts and manages data before it enters the cloud. | General networking or security tool for secure tunneling and access control. |
| Nature | Data-centric security, focused on content protection (encryption/tokenization). | Network-centric security, focused on secure connection (transport layer). |
| Definition | A policy enforcement point between the user and the cloud service, primarily for data protection. | Creates a secure, encrypted tunnel for all network traffic between two points. |
| Examples | Protecting data in SaaS apps, enforcing corporate encryption standards on cloud uploads. | Secure remote access to an internal network, site-to-site connectivity. |
| Function/Purpose | Maintain control of the encryption keys, enable corporate policy enforcement, and ensure cloud data is secure at rest. | Provide secure, private network access over a public network. |
| Characteristics | Performs field-level or file-level encryption, provides tokenization, manages encryption keys externally. | Encrypts the entire data package/session, focused on identity and network access. |
| Based on | Data classification policies and user access roles. | Network addresses and user credentials for connection authorization. |
| Advantages | Offers granular data control, facilitates compliance, separates encryption keys from cloud data. | Simple to deploy for network access, secures data in transit. |
| Limitations | Only protects data at rest in the cloud, and does not secure the network itself. | Does not provide control over the data once it is stored in the cloud. |
To understand Cloud Encryption Gateways properly, it is necessary to go through their core elements. A CEG is not a single piece of software but a system built from several specialized parts. Cloud encryption gateways rely on the tight integration of these components to provide robust data security.
The Essential Components of Cloud Encryption Gateway
The four essential components of a typical CEG solution are:
Let us now understand the role of the Key Management System (KMS) in more detail. The KMS ensures that the keys are never exposed to the cloud environment. For example, if a CEG uses AES-256 for encryption, the KMS stores the 256-bit key on your premises, or in a secured, external Hardware Security Module (HSM), ensuring maximum security.
The figure below shows a simplified view of the cloud encryption gateway architecture. Observe that the data is secured at the gateway before it is transmitted over the network to the cloud storage. This architecture ensures that the cloud provider never sees the data in its original, readable form.
Also Read: IPSec Explained: Protocols, Modes, IKE & VPN Security
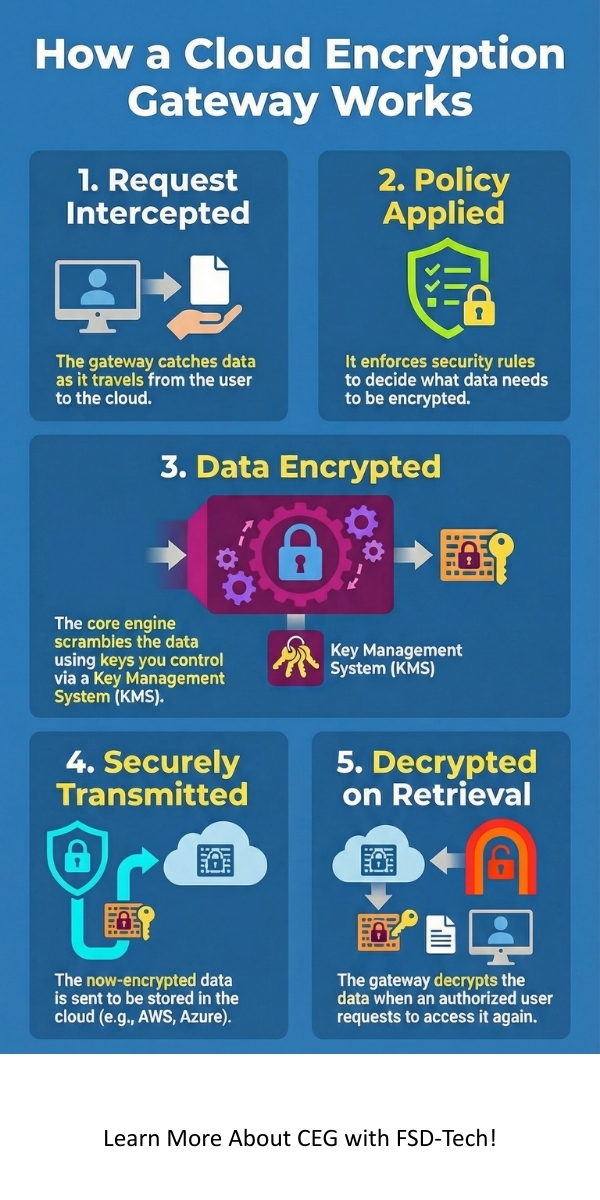
Here, we will see how a Cloud Encryption Gateway actually works step-by-step. The process of securing your data through a CEG solution is efficient and happens in near real-time, making it seamless for the end-user.
The typical process begins when a user tries to access or upload data to a cloud service.
For example: Suppose an employee tries to upload a document containing customer credit card numbers to a cloud storage service. The Cloud Encryption Gateway intercepts the upload. Its policy identifies the sensitive data and uses its tokenization engine to replace the card numbers with unique, non-sensitive tokens.
Only these tokens are uploaded to the cloud, while the actual card numbers are secured in a separate, highly protected token vault managed by the KMS. This way, the card numbers are never stored in the public cloud environment, a robust method of cloud data protection.
Cloud encryption gateways ensure that the decryption key is only available to the authorized CEG, which is under your control, and never to the cloud provider. This is the cloud security benefit you are buying into.
Cloud encryption gateways possess a set of distinctive characteristics that define their function and utility in modern cloud security. These features are what set them apart from simple network security tools.
Following are the key characteristics:
Additionally, many modern cloud encryption gateways offer Data Loss Prevention (DLP) features. These capabilities help prevent sensitive data from being uploaded to unauthorized cloud services in the first place, or from being shared improperly by an employee. The use of a CEG solution is vital for a comprehensive cybersecurity strategy.
Also Read: What is Datagram Transport Layer Security (DTLS)? How it works?
Adopting a Cloud Encryption Gateway provides significant benefits, fundamentally changing how you approach cloud data security. Cloud encryption gateways enable greater cloud adoption while minimizing risk.
Furthermore, the implementation of a cloud encryption gateway offers enhanced visibility into cloud usage, often categorized as a Cloud Access Security Broker (CASB) capability. This allows security teams to monitor employee access to sanctioned and unsanctioned cloud applications.
While Cloud Encryption Gateways offer powerful cloud security benefits, they are not without limitations. It is vital to understand these constraints before fully relying on a CEG solution.
Cloud encryption gateways also typically cannot secure data created directly within a cloud service unless that service is configured to route the data back through the gateway. Therefore, proper user education and policy enforcement are essential to ensure all sensitive data flows through the CEG.
Cloud encryption gateways have diverse applications across various industries, primarily focused on cloud data protection and regulatory adherence.
For instance: Consider a financial firm using a third-party CRM (Customer Relationship Management) system in the cloud. The firm's Cloud Encryption Gateway is configured to identify all fields containing customer account numbers. As data is entered, the gateway automatically tokenizes these numbers, sending only the tokens to the CRM.
The original account numbers remain secured in the firm's private key vault. The CRM can function normally with the tokens, but the actual sensitive data is safe, even if the CRM's system is breached. This ensures strong network security and data control.
A Cloud Encryption Gateway is an essential tool in your modern cybersecurity arsenal, especially as you increase your reliance on cloud services. It is more than just an encryption tool; it is your organization’s command center for cloud data control, ensuring that your sensitive information is never fully at the mercy of an external provider. Cloud encryption gateways deliver the ultimate security by allowing you to keep the encryption keys close while your data is securely stored far away.
Thus, implementing a comprehensive CEG solution will enable you to confidently embrace the agility and cost benefits of the cloud while satisfying the most stringent regulatory requirements. By adopting this technology, you are making a commitment to superior data security and demonstrating a proactive approach to protecting your most valuable asset: your data. We are dedicated to helping you secure your journey to the cloud, making complex security simple, transparent, and absolutely controlled by you.
Multi-cloud chaos? Enforce one encryption policy everywhere with Cato CEG – talk to our UAE/GCC experts today!
A CEG is a component that often falls under the broader CASB category. A Cloud Access Security Broker (CASB) provides four pillars of functionality: visibility, compliance, data security, and threat protection. The cloud encryption gateway (CEG) specifically handles the data security pillar by focusing on encryption and key management.
No, it does not replace the cloud provider's encryption. It complements it. The cloud encryption gateway provides your encryption using keys you control, before the data even reaches the cloud. The cloud provider's encryption, while useful, uses keys they control, which means the data is readable by them.
A Cloud Encryption Gateway can be deployed as either a physical network appliance, a virtual appliance running on your premises or in your infrastructure (IaaS), or as a pure software-as-a-service (SaaS) solution. Its function, however, is always to act as an intermediary, a cloud gateway, for data transmission.
Tokenization is a feature of the cloud encryption gateway that replaces sensitive data (e.g., credit card numbers) with a non-sensitive placeholder called a token. The original data is kept in a secure vault under your control. This is often preferred over encryption for specific compliance scenarios, as the token is not mathematically reversible.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts