.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Every modern business uses software applications to run operations, connect with customers, and store sensitive data. These programs, from a simple mobile app to a complex enterprise resource planning (ERP) system, are essential. As we know, cybersecurity threats continue to rise. This means protecting these applications is now a vital business requirement.
You might ask, What is Application Security (AppSec)? It refers to the processes, features, and practices that make applications more resistant to security threats. This proactive approach focuses on protecting the software itself. It is a critical layer of defense within the broader cybersecurity discipline.
We will now discuss the core concept of Application Security, explore its essential components, and explain why implementing application security best practices is non-negotiable for your business.
Application Security can be understood as the process of applying security controls to software applications. This happens throughout the entire application lifecycle—from the initial design and development phases all the way to deployment and eventual maintenance.
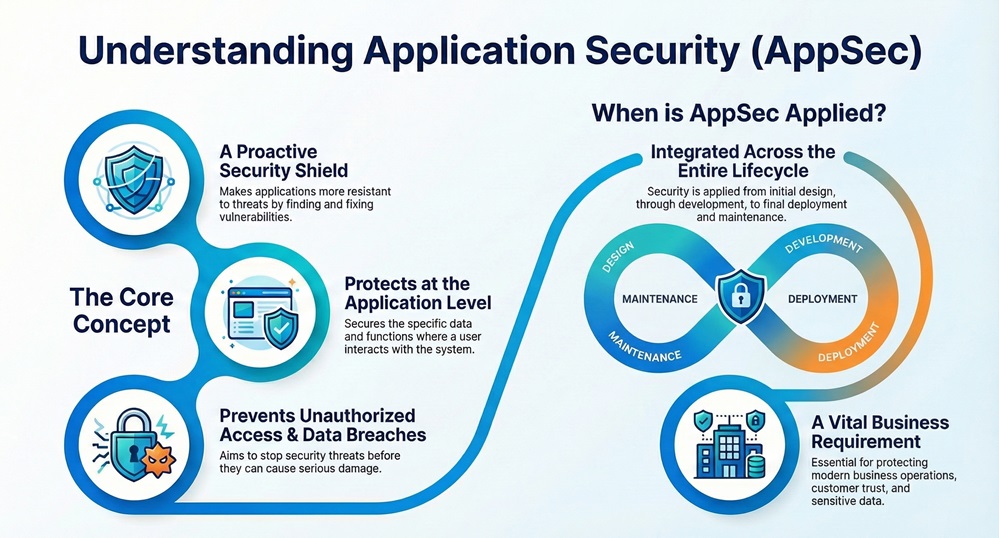
This process aims at preventing unauthorized access and data breaches by identifying, fixing, and shielding against vulnerabilities within the application code and its surrounding environment. The focus lies on protecting data and functionality where the user interacts with the system.
Application Security provides protection at the application level. This ensures that the application performs its intended functions securely and correctly.
Considering the increasing complexity of modern applications and the sensitive data they handle, the question of why application security is important becomes clear. Failing to secure applications creates huge risks.
Due to the critical nature of these applications, neglecting security means you risk serious financial loss, legal issues, and loss of customer confidence.
Also Read: What is API Security and Why it matters for your Business?
Many people confuse Application Security with Network Security. While both are essential components of cyber security, they deal with different areas of protection. Let us now understand the key differences.
| Basis for Comparison | Application Security | Network Security |
|---|---|---|
| Focus Area | The software application itself, including the source code, libraries, and logic. | The network infrastructure, including firewalls, routers, and network access points. |
| Primary Goal | To prevent attackers from exploiting code vulnerabilities to gain unauthorized access or corrupt data. | To prevent attackers from infiltrating the network and moving across systems. |
| Methods/Tools | Application security testing tools (SAST, DAST, IAST), secure coding practices, access controls within the app. | Firewalls, intrusion detection/prevention systems (IDS/IPS), Virtual Private Networks (VPNs). |
| What it Protects | Data within the application, application logic, and user functionality. | Data in transit, servers, endpoints, and the overall network perimeter. |
| Threat Focus | Cross-Site Scripting (XSS), SQL Injection, broken authentication, and business logic flaws. | Denial of Service (DoS), unauthorized network ports, eavesdropping, and malware. |
While a network firewall protects the perimeter of your network, Application Security protects what lies inside that perimeter—the critical software. Both are absolutely required for a comprehensive security posture.
Effective Application Security work is not a single tool or a one-time event. It comprises a collection of integrated practices implemented across the entire software development lifecycle. These practices are commonly divided into four main pillars.
1. Secure Design and Architecture
Security starts right at the design phase. If the architecture has flaws, even perfectly written code cannot fix the underlying issue.
2. Secure Development
This pillar focuses on training developers and using tools to write code free of common flaws.
3. Application Security Testing (AST)
This is where you actively look for flaws in the application using specialized application security testing tools. What is application security testing? It is the practice of running tests to identify security weaknesses in the code and deployed application.
The following are the main types of testing:
4. Security Operations and Monitoring
After deployment, Application Security does not stop. Continuous monitoring is vital to catch emerging threats.
Also Read: What is Zero Trust Security Model? All You Need to Know
Application Security in cybersecurity represents the shift from a perimeter-focused defense to a depth-in-defence approach. If a motivated attacker bypasses your network defences, the application layer must stand firm.
Application Security Services are often utilized by companies to implement these complex security practices. These services can include security audits, managed testing, and developer training.
You must follow certain application security best practices to keep your digital assets safe.
Also Read: What is an Email Security Gateway? Protecting Your Inbox
The right application security software is essential for implementing a robust AppSec program. This software is often a suite of tools categorized by the testing type they perform.
Choosing a security solution requires considering your specific needs, such as whether you need a cloud application security solution or a tool focused on mobile apps.
Application Security is an investment, not an expense. It is a fundamental practice that protects your digital foundation and ensures the trust of your customers. Developing software requires prioritizing security from the first line of code to the last deployment.
We explored what is Application Security, highlighting its primary goal of preventing breaches through continuous vigilance. Remember that securing your applications requires a holistic approach that utilizes people, processes, and technology, including various application security testing tools.
You must implement strong Application Security practices today. Protect your assets, maintain your reputation, and secure your future. Are you ready to strengthen your defenses and ensure your applications stand firm against all threats? Talk to our experts about a comprehensive application security assessment to secure your software and provide peace of mind.

The most common threats often involve flaws in input validation. These include SQL Injection and Cross-Site Scripting (XSS). Attackers exploit these flaws to manipulate the application's logic or steal user data.
This question usually refers to securing the mobile device itself. For securing the applications you develop, you need professional application security testing tools and development practices. For protecting your personal mobile device, standard mobile security apps typically offer antivirus, anti-phishing, and anti-theft protection.
The application security manager oversees the entire AppSec program. This role includes defining security policies, managing the team of security analysts, selecting and deploying application security software, and ensuring the development teams follow all security guidelines.
No. A traditional network firewall primarily controls traffic based on ports and protocols. While a firewall prevents network-level intrusions, it cannot understand the inner logic of an HTTP request. Application-layer attacks (like SQL injection) bypass a regular firewall. This is why you need a Web Application Firewall (WAF) and internal application security controls.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts