
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever used the exact same password for many different online accounts? Almost everyone has done this at some point. Maybe you use the same email and password for your favorite shopping site, your bank, and a streaming service. This makes logging in easy, right?
But this common habit creates a huge problem, and criminals know all about it. They use a simple yet powerful trick called Credential Stuffing. You might feel safe now, but what happens when one of your accounts gets hacked, and the thieves try those login details everywhere else?
In this comprehensive guide, you will get to know about these tricky attacks in clearer terms. We will explain exactly what Credential Stuffing is, how these attacks happen, and, most importantly, how to stop them. Take a read of this to learn how to keep your personal information and your company's systems safe from credential stuffing attacks.
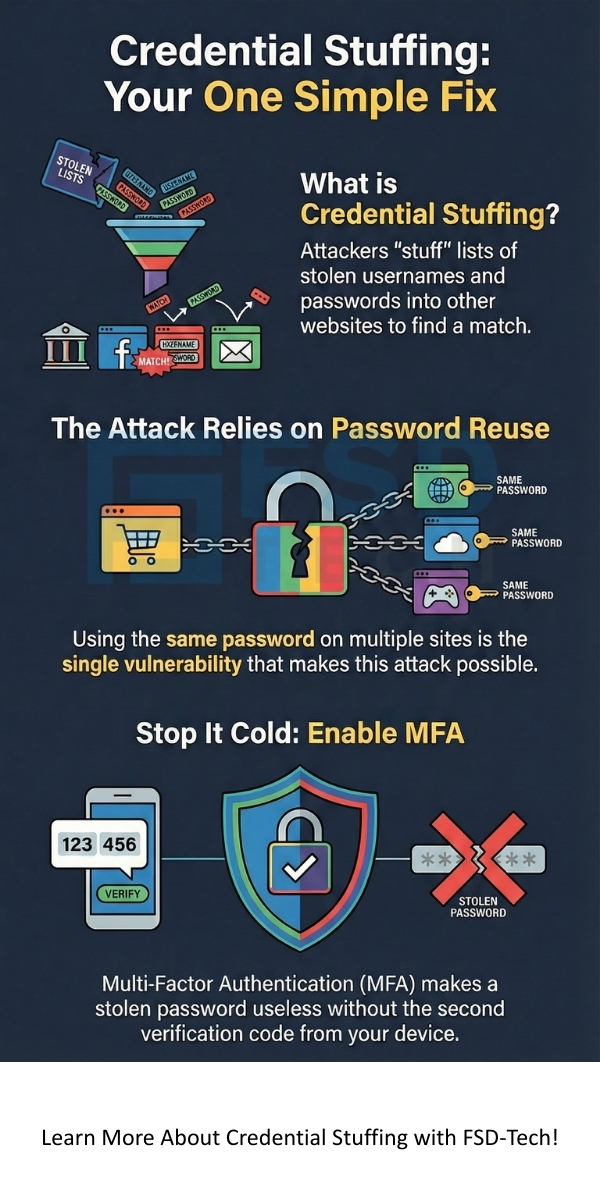
Credential Stuffing refers to a specific type of cyberattack. It can be understood as a large-scale automated attempt by bad actors to gain access to user accounts. They do this by "stuffing" or inputting lists of stolen usernames and passwords into login forms on various websites.
It is to be noted that criminals do not hack the websites they are attacking. Instead, they use login details—the credentials—that they already stole from a different, usually smaller, data breach. Credential stuffing is possible because many people reuse the same username and password across multiple sites. The core concept is simple: if the stolen credentials work on one site, there is a good chance they will work on another.
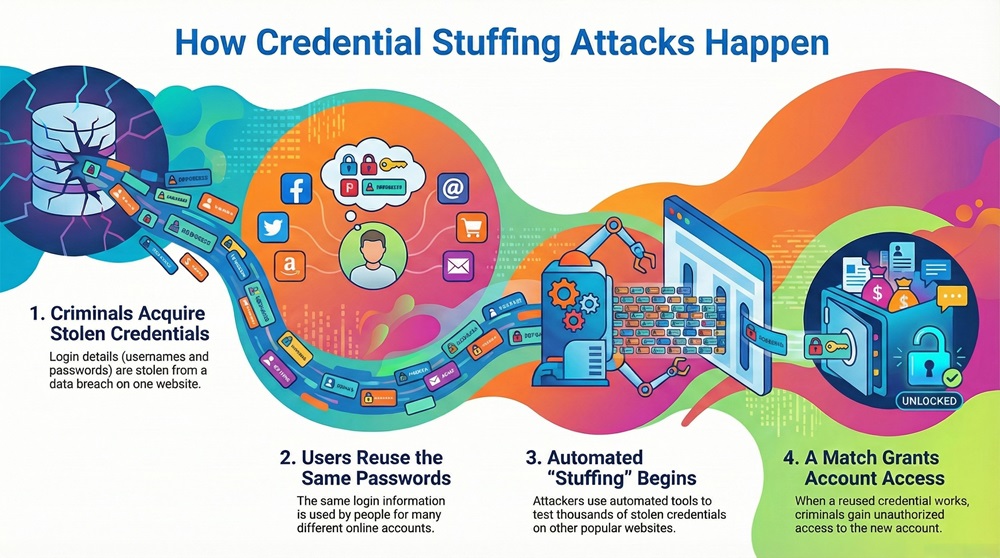
Further, these attackers use tools that automate the login process. These tools can try thousands of stolen credential pairs per minute. This lets them target many accounts quickly, which makes preventing credential stuffing attacks a major challenge for security teams.
To understand Credential Stuffing in clearer terms, let us look at how it is different from other attacks.
| Feature | Credential Stuffing | Brute Force Attack | Dictionary Attack |
|---|---|---|---|
| Input Data | Real, stolen username/password pairs from a data breach. | Systematically generated, all-possible character combinations. | Pre-compiled list of common words, phrases, or leaked passwords. |
| Core Principle | Exploits user password reuse across different websites. | Attempts to guess the password through sheer volume of attempts. | Exploits user tendency to pick simple, common, or dictionary words. |
| Likelihood of Success | High efficiency per attempt, as the credentials are known to be valid somewhere. Success rate depends on reuse. | Low efficiency per attempt. Success rate depends on password length and complexity. | Medium efficiency; faster than Brute Force but fails against unique, complex passwords. |
| How It Works | Attackers take a list of stolen login credentials and automatically "stuff" them into the login forms of an unrelated target website. | Attackers use software to try every single possible combination of characters (letters, numbers, symbols) until the correct one is found. | Attackers use a program to cycle through a list of human-chosen words, phrases, and common patterns (e.g., password123, summer2024). |
| What It Targets | Typically targets many accounts on many different websites simultaneously. | Often targets a single, specific high-value account with high intensity. | Targets either a single account or many accounts using common passwords (like password spraying). |
| Key Defense | Multi-Factor Authentication (MFA) and Bot Management solutions. | Account lockout policies and rate limiting (limiting attempts per minute). | Strong password policies and blocking common/leaked passwords. |
| Detection Difficulty | Harder to detect because successful logins appear as valid, authenticated requests, often from rotating IP addresses. | Easier to detect due to the high volume of failed login attempts from the same IP address. | Easier to detect through monitoring repetitive failed attempts using a known list of words. |
Credential stuffing is far more efficient than brute force or dictionary attacks. Why? Because the attackers are not guessing; they already have a list of real, verified login credentials. They are simply testing them in a new location.
Also Read: Dictionary Attack in Cybersecurity - How it Works and How to Stop?
A Credential Stuffing attack has a clear sequence of steps. Understanding this process helps businesses and users in preventing credential stuffing attacks.
There are four key steps in a typical credential stuffing attack:
1. Acquiring the Credentials
Initially, the attacker needs a list of username and password pairs. They get these login credentials from a data breach on an unrelated website. For example, a gaming forum or a small retail site might get hacked. The attacker then dumps the list of stolen accounts. These lists are called "combos" and are bought and sold on the dark web.
2. Preparing the Attack Tools
Next, the criminals use specialized software tools. These programs are designed to mimic real human login attempts. They can:
3. Executing the Credential Stuffing
The attack software starts to repeatedly post the stolen credentials to the target website's login page. This happens at high speed and high volume. The software tries one set of credentials after another. When a login attempt is successful, the software marks that account as "valid." This is the moment when the criminal gets unauthorized access.
4. Monetizing the Stolen Accounts
Eventually, the attacker takes control of the newly accessed accounts. Now, they can use the accounts in several ways:
Always remember that the ultimate goal of any credential stuffing attack is to make money, either through direct theft or by selling the compromised accounts.
Credential stuffing has become a serious security epidemic. Several factors contribute to why this type of attack is so common and successful.
The Problem of Password Reuse
Now, let us discuss the biggest reason: password reuse. Credential Stuffing relies entirely on people using the same password everywhere. When a user creates a new account, they often choose a password they already know, making them vulnerable. One security failure on a single site gives attackers the master key to many accounts.
Availability of Stolen Credential Lists
Also, vast quantities of login credentials are now available. Data breaches happen often, and the stolen information is cheap to buy. A simple web search can lead a criminal to databases containing billions of records. This easy access to fresh lists of stolen credentials fuels the ongoing attacks.
Sophisticated Automation Tools
Further, the tools attackers use are highly effective. Due to which, these automated bots can bypass basic security measures. They are designed to look like human users, making them tough for traditional security systems to detect. The sheer volume of traffic from a single credential stuffing campaign can overwhelm a website.
Low Risk, High Reward
From the criminal's perspective, this attack is low-risk. They do not need to be master hackers. They simply need lists and tools. The reward, on the other hand, is high. They get access to user accounts containing payment info, personal data, and more. This makes preventing credential stuffing attacks a top priority for any organization.
Also Read: Spear Phishing: Learn About #1 CEO fraud
Preventing credential stuffing attacks requires a layered approach. Companies must put defenses in place, and users must change their habits. Both parties play a role in making a system safer.
Credential Stuffing Protection for Businesses
Organizations must focus on technical and behavioral defenses. Among these, the implementation of strong security protocols is essential.
1. Implement Strong Multi-Factor Authentication (MFA)
This is the single most effective way to stop credential stuffing. If an attacker successfully uses a stolen username and password, MFA stops them cold. It requires a second form of verification, such as:
If you have MFA turned on, the stolen credentials alone are useless to the attacker.
2. Utilize Bot Detection and Management
Use specialized security solutions that can identify bot traffic. These tools check for things like:
These systems can block or challenge suspicious traffic, effectively stopping the credential stuffing attempts before they succeed.
3. Enforce CAPTCHAs and Behavioral Analysis
CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) tests are simple steps that can slow bots down. However, modern bots can sometimes bypass simple ones. It is better to use advanced behavioral analysis, which looks at how a user moves their mouse, types, or navigates the site. If the behavior is too mechanical, it flags the login as a risk.
4. Monitor and Block Known Bad IP Addresses
Maintain a list of known sources for credential stuffing attacks, such as anonymous proxy networks or TOR exit nodes. By blocking traffic from these sources, you can immediately reduce the volume of malicious login attempts.
5. Monitor and Blacklist Stolen Credentials
Some companies actively monitor the dark web for lists of stolen usernames and passwords. When they find a list, they can proactively block those login credentials on their site. If a user tries to log in with a known compromised password, the system can force a password reset.
Even the best company security can fail if users are not careful. You, the reader, have the power to stop these attacks by changing your habits.
1. Stop Reusing Passwords
This is the most important step. Always remember to use a unique, strong password for every single account you own. If one account is breached, the attacker will only get access to that one account and no others. This makes credential stuffing impossible against your other services.
2. Use a Password Manager
So, how do you remember hundreds of unique passwords? Use a password manager. This tool creates, stores, and fills in long, complex, unique passwords for all your sites. You only need to remember one master password. This is a crucial defense against credential stuffing.
3. Turn On Multi-Factor Authentication (MFA) Everywhere
Make sure you enable MFA on every site that offers it, especially your email, bank, and social media. Even if an attacker steals your login credentials, they cannot get into your account without that second code. This offers a powerful shield against a credential stuffing attack.
4. Create Long, Complex Passwords
Always remember to create a password that is long and contains a mix of letters (upper and lower case), numbers, and symbols. A longer password is much harder to guess or crack.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
A successful defense against credential stuffing uses multiple technologies working together. To understand this in clearer terms, let us look at the key components involved.
1. Web Application Firewall (WAF):
2. Behavioral Analysis Tools:
3. Risk-Based Authentication (RBA):
4. IP Reputation Services:
So, in summary, you now know that Credential Stuffing is a serious and simple attack that relies on a single, common user mistake: reusing passwords.
When dealing with the threat of credential stuffing, businesses must utilize Risk-Based Authentication and strong bot management tools. Preventing credential stuffing attacks ultimately depends on adopting a "defense-in-depth" strategy, using multiple layers of security.
For you, the user, the guidance is clear: Never reuse passwords, and always turn on Multi-Factor Authentication for your critical accounts.
When you choose to protect your accounts with unique passwords and MFA, you break the chain of the credential stuffing attack. You make the hacker's stolen list of credentials worthless, ensuring your information stays secure. Take control of your digital security now. Protect your online accounts and ensure your data remains safe.
Reach us now for a free consultation
Credential stuffing is a complex topic, but many people have the same questions about it. We address those concerns here.
If a criminal gets access to your account through credential stuffing, several bad things can happen:
Yes, they absolutely can. While your password reuse makes the attack possible, a company's robust security can stop it. For instance, if the website uses strong bot detection or forces Multi-Factor Authentication, the attack will fail, even if the password is correct.
Yes, credential stuffing is a crime. It is considered unauthorized access to a computer system and data theft. The individuals and groups that run these operations are committing serious cybercrimes, often across international borders.
There are free online services, like "Have I Been Pwned," that you can use. You can enter your email address to see if it was included in any known data breaches. Always remember to change your password immediately on any site where your email has appeared in a breach list.
Businesses are the main targets because they hold the value. The accounts on shopping sites have payment information. Bank accounts hold money. Streaming services are sold for profit. Attackers go where the money and data are, making preventing credential stuffing attacks vital for business stability and customer trust.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts