
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

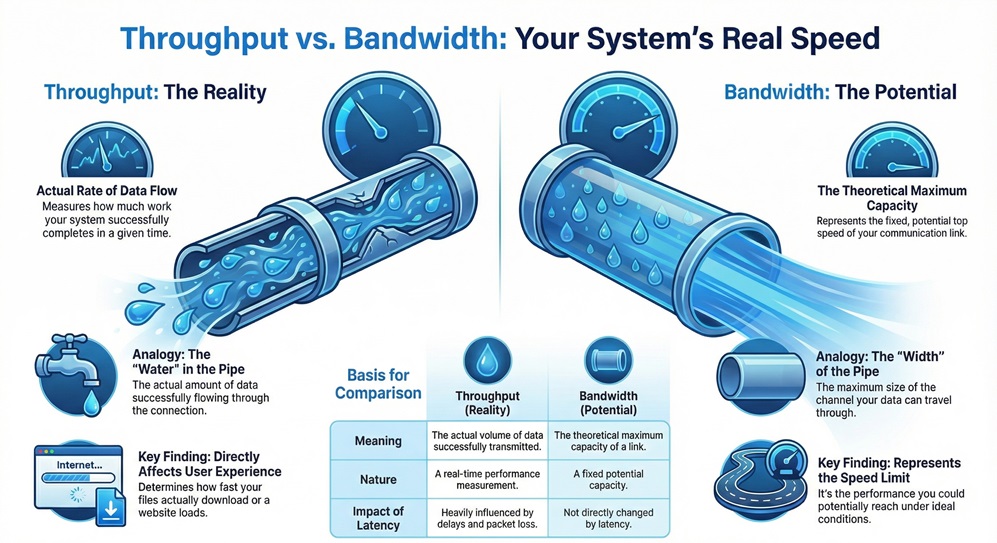
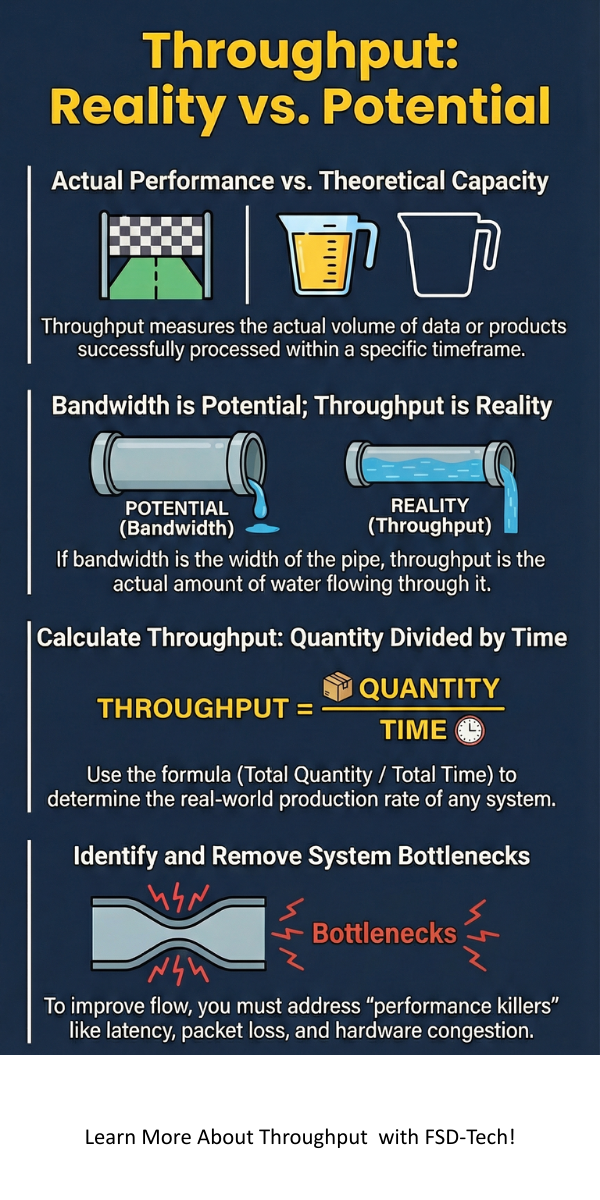
Throughput refers to the actual rate at which a system processes or moves data, products, or information from one point to another within a specific timeframe. In computing and networking, it represents the successful delivery of data packets over a communication channel. It acts as a vital measure of efficiency, showing you how much "work" a system actually completes versus its theoretical maximum capacity.
To understand this concept, you need to think about the difference between potential and reality. Many people confuse throughput with bandwidth. However, while bandwidth represents the maximum width of the "pipe," throughput measures the actual amount of "water" flowing through it at any given moment. One may wonder why a fast connection still feels slow; the answer usually lies in the difference between these two metrics.
| Basis for Comparison | Throughput | Bandwidth |
|---|---|---|
| Meaning | The actual volume of data successfully transmitted over a period. | The theoretical maximum capacity of a communication link. |
| Nature | It is a real-time performance measurement. | It is a fixed potential capacity. |
| Impact of Latency | Heavily influenced by delays and packet loss. | Not directly changed by latency. |
| User Experience | Directly determines how fast a file downloads for you. | Represents the limit of what you could potentially reach. |
| Calculation | Measured as (Total Data) / (Total Time taken). | Measured based on signal frequency and physical hardware. |
Throughput involves looking at the output of a process. In the simplest terms, it is the production rate of a system. If you operate a manufacturing plant, your throughput is the number of finished goods leaving the assembly line per hour. In the digital world, it is the number of bits that successfully arrive at their destination.
To be honest, most users care more about this metric than any other. Have you ever wondered how much traffic does a website get and why it crashes? That happens because the incoming requests exceed the system's ability to process them. When the "load" surpasses the throughput, the system starts to lag or fail. It is nothing but a reality check for your hardware and software.
Throughput in Operating System refers to the number of processes or tasks the CPU completes in a unit of time. It is a primary goal of scheduling algorithms to maximize this number. In a multi-programming environment, the OS tries to keep the CPU busy at all times to ensure that more jobs are finished quickly.
The throughput of network systems and operating systems are linked. If the OS cannot process data packets fast enough due to high CPU usage, the network performance will drop. In this context, the OS acts as a gatekeeper. If the gate is narrow or the guard is slow, the flow of data stalls.
The throughput of network systems represents the actual speed of data transfer across a local or wide area network. Here's the thing: your network is only as fast as its slowest link. Even if you have a fiber-optic cable, a congested router can kill your speed.
According to research from Tetcos, several elements define this performance:
When we talk about what throughput means in a network, we are looking at the "Goodput." Goodput is a sub-set of throughput that excludes protocol overhead and retransmitted packets. It is the "useful" data you actually receive.
Also Read: What is Latency in Networking? Definition, Causes & Solutions
The what is throughput rate question is best answered by looking at the formula:
Throughput = Total Quantity/Time
In supply chain management and order fulfillment, this rate determines how quickly a company can satisfy customer demand. A high rate suggests an efficient, lean process, while a low rate indicates "bottlenecks."
Let us discuss the components of this rate:
If you are managing a warehouse, you want your throughput rate to match your order volume. If you can’t ship items as fast as they are ordered, your "backlog" grows, and customer satisfaction drops.
In the field of biology, what is high throughput sequencing (HTS) refers to a modern technology that allows researchers to sequence DNA and RNA much faster than traditional methods. It has revolutionized genomic research by allowing millions of sequences to be processed simultaneously.
HTS is a perfect example of scaling. By parallelizing the work, scientists can map an entire human genome in days rather than years. This massive "data dump" requires significant computing power to analyze, but the throughput of the sequencing machines themselves is what opened the door to personalized medicine.
Also Read: What is a Wireless LAN Controller? Configuration & Setup 101
Throughput accounting is a principle used in the Theory of Constraints. It focuses on how much money a company makes through sales minus the "totally variable costs" (like raw materials). It differs from traditional cost accounting because it views everything as a system.
The goal here is simple:
In my experience, many businesses fail because they focus on "local efficiencies" (making one machine go fast) rather than "system throughput" (getting the product to the customer).
There are several reasons why your system might not be reaching its full potential. Let us understand these limitations:
Understanding what does throughput mean is the first step toward optimizing any system, whether it is a computer network or a manufacturing line. By focusing on the actual output rather than just the potential capacity, you can find the real "choke points" in your operations.
We are committed to helping you understand these technical concepts so you can make better decisions for your business or studies. Our goal is to provide clear, actionable insights that drive real-world results.
Master network metrics today, Contact our Experts
A: Generally, yes. However, if you push a system too hard, you might increase the error rate, which eventually causes the throughput to collapse.
A: You can use tools like iPerf or simple speed tests. These tools send a known amount of data and measure how long it takes to arrive.
A: Throughput is how much data moves; Latency is how fast a single piece of data moves. You can have high throughput with high latency (like a large truck moving slowly).

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts