
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

Are you worried about hidden threats lurking in your network? Many cyber security teams only react to alerts their tools generate. But what about the attackers who cleverly sneak past those defenses? Proactive threat hunting changes this defensive game.
Threat hunting is nothing but a proactive, human-driven process. Threat hunting works by actively searching for malicious, unauthorized, or suspicious activities that have evaded existing security tools. Cyber threat hunting helps you find the bad actors before they cause serious damage. This approach shifts your security posture from reactive to predictive. Threat hunting in cyber security is essential because traditional tools cannot catch everything.
This guide will help you understand what threat hunting is, why it matters, and how you can implement it. We will explore the methods and tools that professional hunters use to secure your valuable data. Do not reveal all of your security secrets to the attackers; instead, let us threat hunt for them first.
Threat hunting can be understood as the practice of proactively and iteratively searching through networks and systems to detect advanced threats that target an organization. The goal of cyber threat hunting is to find hidden threats that have bypassed automated security controls, such as firewalls and antivirus software.
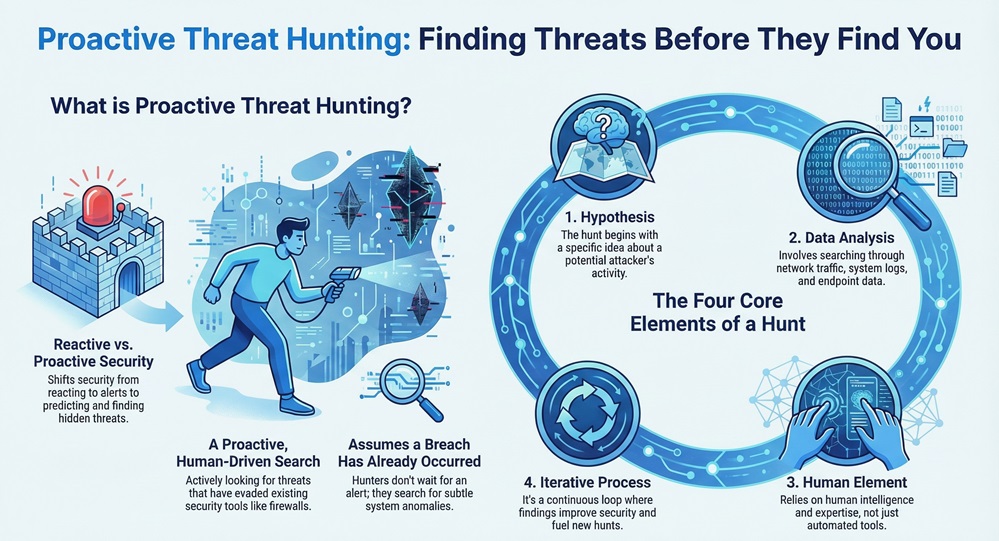
A threat hunter does not wait for a security alert. Instead, they assume a breach has already happened. The hunter uses this assumption to look for anomalies, which are small deviations from normal network and system behavior. Threat hunting primarily relies on a deep understanding of the attacker's tactics, techniques, and procedures (TTPs).
In simple words, what is threat hunting? It is like a detective systematically searching a house for a hidden intruder, even though the alarm system did not go off. This process ensures continuous improvement of your overall security system.
To understand proactive threat hunting fully, you must first know the key elements it comprises:
Often, people confuse threat hunting with threat intelligence. While both play a vital role in cyber security, they are distinct functions that complement each other. Let us now discuss the differences.
| Basis for Comparison | Threat Hunting | Threat Intelligence |
|---|---|---|
| Primary Action | Proactive search for threats already in the network. | Collection and analysis of information about potential external threats. |
| Focus | Internal network data, system logs, and anomalies. | External attacker TTPs, malware families, and campaigns. |
| Goal | To find and remove hidden threats inside the environment. | To inform security decisions and improve defenses before an attack. |
| Main Output | Newly discovered threats, indicators of compromise (IOCs). | Contextualized reports, TTPs, and actionable defensive advice. |
| Driver | Human-driven curiosity and security analyst expertise. | Automated feeds, external research, and data from third parties. |
Threat hunting relies on threat intelligence. Threat intelligence provides the context—the what and how of the attacks happening outside—which helps the threat hunter formulate better hypotheses about the where and if of an attack inside your network.
Cyber threat hunting is often based on the information provided by threat intelligence. The intelligence feeds the hunt in various ways:
Also Read: Unified Threat Management (UTM): Key Security Functions
The threat hunting process is not a random search. It is a structured methodology that ensures thoroughness and repeatability. Threat hunting is a continuous cycle.
The following are the sequential steps that constitute a complete threat hunting process:
1. Develop a Hypothesis
Threat hunting always begins with an assumption. This assumption is the hypothesis. The hypothesis typically arises from three primary sources:
2. Formulate Queries and Acquire Data
Once the hypothesis is ready, the hunter must determine what data they need to test it. The threat hunting process requires access to vast amounts of data. This stage involves:
3. Analyze Data and Investigate
This is where the actual cyber threat hunting takes place. The hunter runs the queries and starts reviewing the results.
4. Response and Remediation
When the hunter successfully discovers a malicious activity, the process must immediately shift to response.
5. Enrichment and Improvement
The final and most crucial step ensures that the hunt pays forward. This stage is about improving the security posture.
Effective threat hunting relies on a variety of techniques that allow the hunter to approach the problem from different angles. Knowing what are threat hunting techniques is essential for any security team.
1. Indicator of Compromise (IOC)-Based Hunting
This is the most basic form of threat hunting. It focuses on known bad artifacts.
2. Anomaly-Based Hunting
This technique focuses on finding any activity that deviates from what is considered normal behavior.
3. TTP-Based Hunting
This is the most advanced and effective type of threat hunting. It focuses on the attacker's methods rather than simple file names or IP addresses.
4. Statistical or Cluster Analysis
This technique involves using data science methods to group similar events and identify outliers.
Also Read: Threat Modeling in Cyber Security - Process, STRIDE & Benefits
Threat hunting in cyber security is an investment that provides significant returns beyond just finding threats. You should implement a proactive threat hunting program for many reasons.
1. Reduces the Attacker’s Dwell Time
Dwell time is the amount of time an attacker stays inside your network before you detect them. Threat hunting helps to drastically minimize this time.
2. Enhances Security Tool Effectiveness
Every successful hunt provides crucial intelligence that you can use to tune your existing security defenses.
3. Improves Organizational Understanding of Risk
By performing cyber threat hunting, you gain a real-world understanding of your network's vulnerabilities.
4. Fosters a Stronger Security Team
Threat hunting requires advanced skills, which naturally develops your security analysts.
You require specialized threat hunting tools to analyze massive volumes of security data. While the hunter's skill is paramount, the right tools make the process efficient.
1. Security Information and Event Management (SIEM)
The SIEM system is the core repository for all your log data.
2. Endpoint Detection and Response (EDR)
EDR tools focus specifically on activity at the endpoint level (laptops, servers, desktops).
3. Network Traffic Analysis (NTA) Tools
NTA tools capture and analyze all traffic flowing across the network.
4. User and Entity Behavior Analytics (UEBA)
UEBA tools use machine learning to profile the standard behavior of users and entities.
Also Read: Cyber Threat Intelligence (CTI) in Cybersecurity
Implementing an in-house cyber threat hunting team requires significant investment in highly skilled personnel, advanced tools, and ongoing training. Many organizations choose managed threat hunting as an effective alternative.
Managed threat hunting is a service where a third-party security provider performs the proactive hunting activities on your behalf. Managed threat hunting gives you access to an elite team of expert hunters and sophisticated toolsets without the high overhead cost.
Threat hunting empowers organizations to shift from passive defense to proactive offense, assuming breaches have occurred and systematically seeking hidden adversaries. By leveraging hypothesis-driven searches, behavioral analysis, and advanced tools like EDR and SIEM, hunters uncover sophisticated threats that evade automated detections.
This human-led approach reduces attacker dwell time, enhances incident response, and strengthens overall resilience. Implementing threat hunting—whether in-house or managed—transforms your security posture, minimizing risks and ensuring long-term protection. Invest in threat hunting today to stay ahead of tomorrow’s threats.
Your Security Matters Reach FSD-Tech

Cyber threat hunting is a vital role in modern cyber security. It is a proactive and human-driven process that assumes your network is already compromised and seeks to find the evidence.
The main goal of threat hunting is to proactively search for, identify, and contain malicious activity that has bypassed existing automated security measures. Its aim is to significantly reduce an attacker's dwell time in your environment.
A threat hunt starts with a hypothesis and is proactive, looking for unknown, hidden threats. An investigation starts with an alert (an IOC or a rule firing) and is reactive, determining the scope and impact of a known, confirmed incident.
Yes, you should use threat intelligence. While you can start with baseline and anomaly hunting, threat intelligence provides the necessary external context about the latest TTPs. This information helps your threat hunting team formulate high-value, specific hypotheses, making the hunts much more efficient and effective.
A professional threat hunter needs a blend of skills. They need strong analytical abilities, a deep understanding of networking and operating systems, expertise in scripting (e.g., Python), and the ability to formulate complex search queries (e.g., KQL, SPL) for SIEM systems. Cyber threat hunting is a demanding role.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts