
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Threat modeling is an essential process that helps you secure your systems and applications. It aims at identifying, understanding, and mitigating potential security risks before a system goes live. If you build software without understanding the threats it faces, you risk significant and costly security breaches.
We are living in a digital world where security must be a core part of building anything. This method ensures that your team focuses on the most critical security issues early in the development lifecycle.
But, how does this process help you build stronger systems? And what makes a good threat model so vital for modern cyber security? Let us explore how you can use this technique to safeguard your business assets.
A threat model can be understood as a structured representation of all the information that affects an application’s security. Simply put, it is a living document that captures the security design of your system, identifies potential weaknesses, and determines the necessary actions to reduce risk.
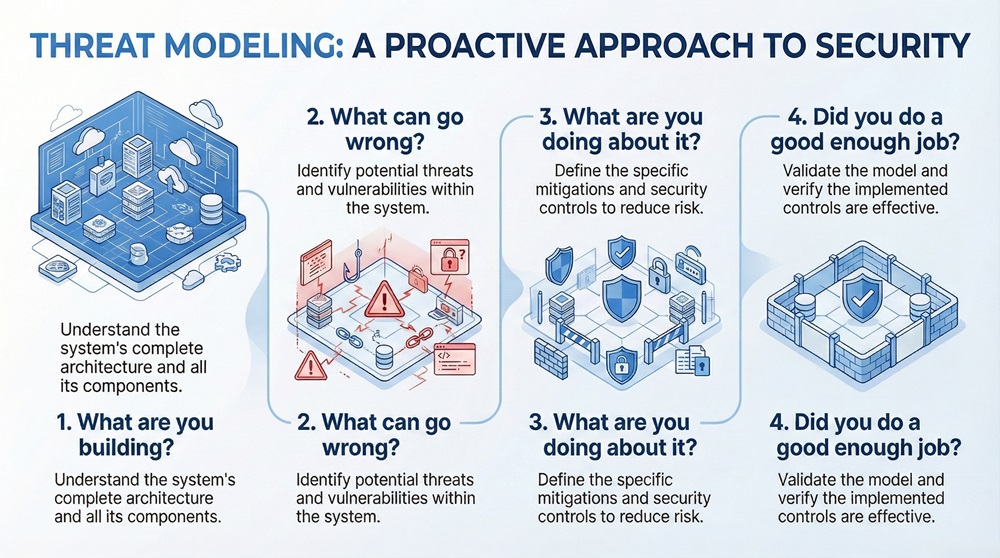
The core goal of a threat model in cybersecurity is to provide a systematic way to answer four fundamental questions about your application:
This proactive approach means you are building security in, rather than patching weaknesses later.
Proactive Security with Cato SASE
The threat modeling process systematically breaks down your system to find vulnerabilities. While different methodologies exist, the core steps remain consistent.
The process follows a logical sequence to ensure comprehensive security review. Here, we will discuss the four major steps in the threat modeling process.
1. Model the Application (What are you building?)
The first step in the threat modeling process is defining the system clearly. You cannot secure what you do not understand.
Understanding the data flow helps you see where critical data resides and how attackers might access it.
2. Identify Threats (What can go wrong?)
Once you understand the system architecture, you must ask: What are the possible threats? This step uses structured approaches to find potential security issues.
When you use a framework, you ensure that you do not miss common types of attacks.
3. Rate and Prioritize Threats (What are you doing about it?)
Not all threats present the same level of risk. Your team must focus efforts where they matter most. This involves rating the identified threats.
The result is a prioritized list of security issues. You will address the high-risk threats first, which is the most efficient way to use security resources.
4. Define and Verify Mitigations (Did you do a good enough job?)
The final step in the threat modeling process is defining and applying security controls, and then confirming their effectiveness.
In this way, the process confirms that the implemented security is adequate for the risks identified.
Also Read: Unified Threat Management (UTM): Key Security Functions
To successfully identify threats, you need a systematic method. Threat modelling methods provide this structure. They help teams think like an attacker and categorize the security vulnerabilities.
STRIDE: A Foundational Approach
The STRIDE method is one of the most popular and comprehensive threat modelling methods. It uses a mnemonic to ensure you consider six specific categories of threats:
| Threat Category | Description | Security Property Violated | Example Mitigation |
|---|---|---|---|
| Spoofing | Impersonating another user or system component. | Authentication | Implement strong authentication mechanisms. |
| Tampering | Modifying data in transit or at rest. | Integrity | Use digital signatures or encryption. |
| Repudiation | Denying an action without proof. | Non-Repudiation | Implement comprehensive auditing and logging. |
| Information Disclosure | Exposing sensitive data to unauthorized parties. | Confidentiality | Encrypt data both in transit and at rest. |
| Denial of Service | Preventing legitimate users from accessing the system. | Availability | Implement rate limiting and load balancing. |
| Elevation of Privilege | Gaining capabilities beyond those initially granted. | Authorization | Use the principle of least privilege. |
The STRIDE approach helps you systematically check for common threats associated with different elements in your system’s DFD.
DREAD: Assessing Risk
While STRIDE identifies what can go wrong, DREAD helps you assess the severity of the threat. DREAD is a simple scoring system where each factor is rated, typically from 1 (low) to 10 (high), and the scores are averaged to get a final risk rating.
When you combine STRIDE (threat identification) with DREAD (risk rating), you get a strong foundation for the threat modeling process.
What is threat modeling in SDLC (Software Development Life Cycle)? It is the practice of integrating security analysis throughout the entire development process, not just at the end. This shift is crucial for catching design flaws when they are cheapest and easiest to fix.
Integration Points
This integration makes security an ongoing task, not a final checkpoint. Threat modeling in SDLC dramatically reduces security costs and risks.
Also Read: What is an Intrusion Prevention System (IPS)?
A completed threat model is not just a list of risks; it is a structured document that guides security decisions.
What does a threat model look like in its final, usable form? It is an actionable security report that contains:
This clear, concise, and structured report is the threat model report. It serves as the single source of truth for the system's security posture.
The purpose of threat modelling is simple yet profound: to build more secure systems by adopting a proactive, attacker-focused mindset.
In essence, the process ensures you are ready for the threats your application faces.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
Threat modelling can be applied to virtually any system that processes data or performs critical functions. It is not limited to just web applications.
Considering the widespread application, threat modelling is a fundamental skill for modern security teams.
By adopting this proactive and structured approach, you ensure that security is a core element of your development. This means you are not just building software; you are building trust and resilience. We help you secure your digital assets by making security design your primary focus. If you are ready to secure your next project with a robust, clear, and actionable security strategy, reach out to us today.
Need Threat Modeling? Reach us for immediate help

Threat modeling offers a powerful and systematic way to address the complexities of modern cyber security. The methodology provides clarity on what you need to protect and how to protect it.
A DFD is essential because it visually maps the path of data, system components, and trust boundaries. It allows the team to pinpoint exactly where data is stored, processed, and transmitted, making it the ideal base for applying methods like STRIDE.
A threat is a potential harm (e.g., "A hacker tries to log in as another user"). A vulnerability is a weakness that a threat can exploit (e.g., "The application uses a weak password policy"). Threat modeling identifies both threats and the underlying vulnerabilities.
You should update the threat model report whenever a significant change occurs in the system's architecture, new features are added, or a new, critical threat is discovered in the wider security environment. The model is a living document that must evolve with the system.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts