
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026
.jpg&w=3840&q=75)
Are you worried about unauthorized access to your computer systems? Do you want to strengthen your cybersecurity defenses? You know that hackers constantly look for weak spots. One of the most dangerous attack methods they use is privilege escalation.
This term, privilege escalation, refers to a critical step in almost any successful cyberattack. You need to understand this concept completely to protect your valuable assets.
This detailed guide helps you grasp exactly what privilege escalation is. We show you the different types of attacks and explain the methods hackers use. We also provide practical defense strategies so you can secure your environment. We focus on giving you clear, actionable information—no fluff, just facts.
Let us understand privilege escalation in simple terms, a core concept in the field of cybersecurity.
Privilege escalation can be understood as the act of gaining authorization or access to resources that a user or application is not supposed to have. In other words, a cyber attacker exploits a vulnerability to move from a lower level of access (like a regular user) to a higher level of access (like an administrator or root user).
This unauthorized rise in permissions plays a vital role in most breaches. Why? Because a standard user on your system cannot do much damage. However, a user with elevated privileges can install malicious software, change system settings, access sensitive data, and even create new administrative accounts.
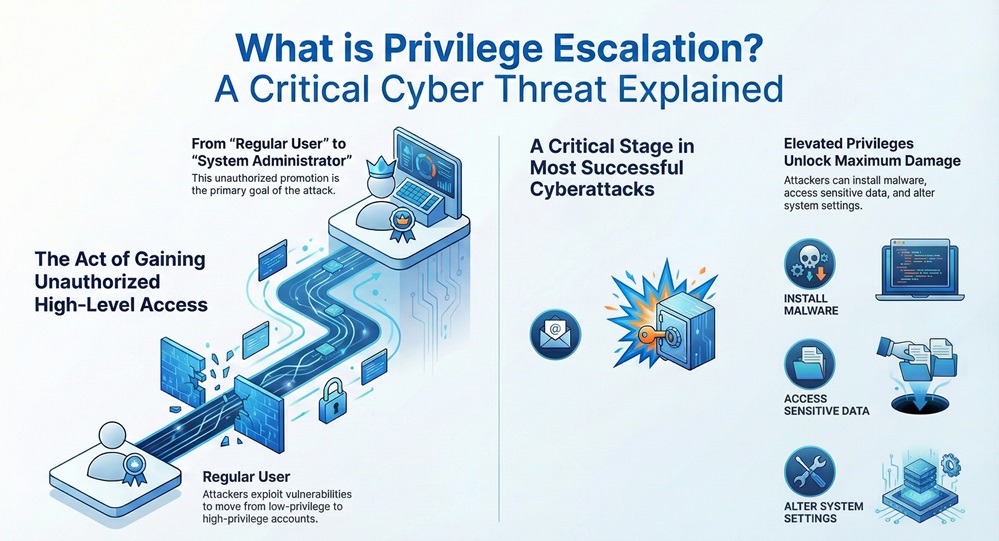
Privilege escalation is nothing but an exploitation. It aims at moving past the initial access point to gain maximum control over the target system or network. This is often the second stage in a successful attack chain, right after the hacker gains initial access.
Proactive Privilege Defense Contact our team
To understand privilege escalation deeply, you must know a few essential terms.
Also Read: What is Credential Stuffing? Detection and Prevention
When discussing privilege escalation, security experts mainly categorize the attacks into two primary types. The distinction is crucial for both attackers and defenders.
Let us explore these two types in detail.
1. Vertical Privilege Escalation
Vertical privilege escalation refers to an attack where a user gains a higher level of privilege than their current account possesses.
2. Horizontal Privilege Escalation
Horizontal privilege escalation refers to an attack where a user gains access to another user's account at the same level of privilege.
The table below clarifies the key differences between these two types of privilege escalation.
| Basis for Comparison | Vertical Privilege Escalation | Horizontal Privilege Escalation |
|---|---|---|
| Goal of Attack | Moving from low privilege to high privilege (e.g., User to Admin). | Moving from one user's account to another user's account at the same privilege level. |
| Access Gained | Superior access and control over the entire system. | Peer-level access to another specific user's data or resources. |
| Example | Exploiting an unpatched kernel vulnerability to become root. | Changing a session ID to hijack another user's shopping cart or bank session. |
| System Impact | Complete system compromise and data theft across all users. | Privacy violation and data theft specific to the targeted user. |
Attackers use several methods to perform privilege escalation. These methods rely on finding and exploiting flaws. The process generally starts with reconnaissance to identify potential vulnerabilities.
Let us now discuss the most common privilege escalation techniques.
1. Exploiting System and Kernel Vulnerabilities
Every operating system (OS) uses a kernel, which acts as the core controller. When the OS has a kernel vulnerability, an attacker can exploit it to run malicious code with the highest possible privilege.
What is the mode of exploiting unpatched systems? Attackers often use public exploit databases to find known, unpatched vulnerabilities in older software versions.
2. Misconfigurations and Weak Service Permissions
System administrators sometimes make mistakes when setting up systems, which creates openings for privilege escalation. This category is where most attacks happen.
a. File and Folder Permissions
b. Services and Scheduled Tasks
3. Password and Credential Harvesting
Attackers always look for saved passwords or reusable credentials. This technique helps in privilege escalation in a direct way.
4. DLL Hijacking (On Windows Systems)
When a Windows program starts, it often loads required support files called Dynamic-Link Libraries (DLLs). This loading process often follows a specific search path.
5. Path Interception (Linux/macOS)
In Linux and similar systems, the system searches the PATH environment variable for executable commands.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
Protecting against privilege escalation requires a comprehensive approach. You must continuously look for flaws in your configuration and ensure that system components follow the principle of least privilege.
1. Implement the Principle of Least Privilege (PoLP)
The Principle of Least Privilege (PoLP) serves as the most basic defense against privilege escalation.
2. Patching and Regular Updates
As we know that many attacks exploit known, unpatched vulnerabilities, regular patching plays a vital role in prevention.
3. Strict Permission Management
You must strictly manage the permissions on your files and system resources.
4. Application Control and Whitelisting
This defense technique involves controlling what software can run on a system.
5. Strong Password and Credential Management
Since password harvesting is a method of privilege escalation, you must use strong measures for credentials.
6. Separation of Privileges
This method works on the principle that no single process should have complete control over a system.
Privilege escalation represents a fundamental threat where an attacker seeks unauthorized elevated privileges to gain maximum control over a system. This technique, whether vertical (low to high access) or horizontal (peer-to-peer access), depends entirely on exploiting a vulnerability or a system misconfiguration. You must implement the Principle of Least Privilege (PoLP) and maintain rigorous patching schedules.
Continuous auditing of permissions and employing defense mechanisms like privilege separation are crucial steps. You need to take decisive action now. We help you secure your digital foundation by eliminating vulnerabilities that enable privilege escalation.
Contact us today to schedule a privilege escalation risk assessment and start building a truly secure environment. Your company's data security is our highest priority, and we ensure that you remain in control, always.

So, with the above discussion, we can say that privilege escalation is a severe threat, but it is one you can absolutely defend against. Remember these key points to strengthen your security posture:
We know you have many questions about privilege escalation. Let us answer the most important ones.
An exploit refers to the specific code or technique that takes advantage of a security flaw. Privilege escalation is the result or the outcome of using that exploit. You use an exploit to achieve privilege escalation.
Broken access control is the primary cause of many privilege escalation attacks. Access control determines what a user can and cannot do. When this control is "broken"—meaning the code allows a user to access resources they should not—the user has successfully performed privilege escalation. This directly relates to horizontal privilege escalation in web applications.
No. Privilege escalation can happen on any type of computing system—your personal laptop, a smartphone, network devices, and large cloud servers. The core concept remains the same: a user or process gains unauthorized elevated privileges.
The best method is to use security information and event management (SIEM) tools. These tools continuously monitor all user and process activities. They look for suspicious events, such as a low-privilege user suddenly running administrative commands or a common application attempting to access highly sensitive files. This is where continuous security monitoring plays a vital role.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts