
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

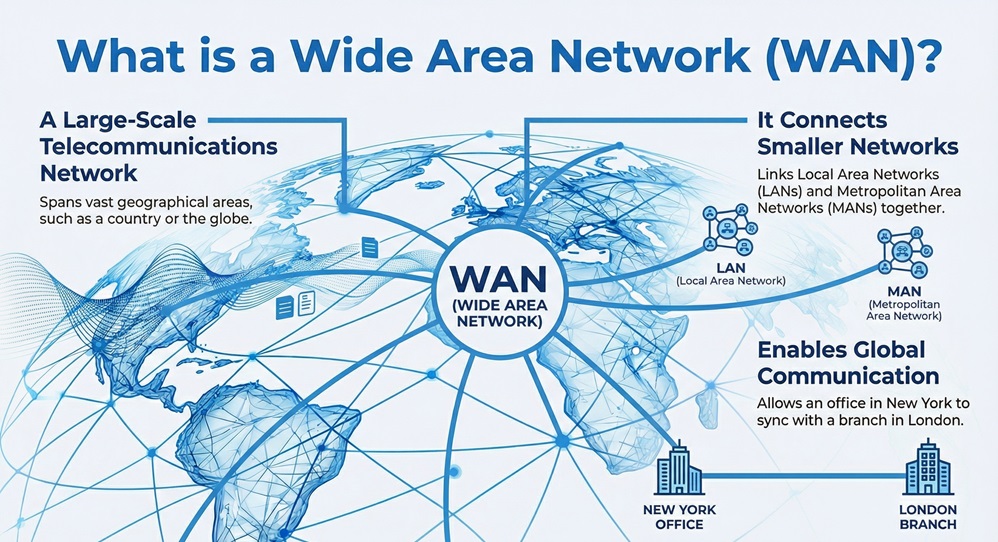
A Wide Area Network (WAN) is a large-scale telecommunications network that spans a vast geographical area, such as a city, country, or the entire globe. It connects smaller networks, like Local Area Networks (LANs) and Metropolitan Area Networks (MANs), ensuring that computers in one location can communicate with those in another.
To be honest, most of us use a Wide Area Network (WAN) every single day without even thinking about it. Have you ever wondered how an office in New York stays synced with a branch in London? Or how you can access a server halfway across the world in seconds? That is the power of a WAN at work. In my experience, understanding this technology is the first step toward grasping how the modern internet actually functions.
Understanding a Wide Area Network (WAN) becomes much easier when you compare it to a Local Area Network (LAN). While one stays within a room, the other crosses borders.
| Basis for Comparison | Local Area Network (LAN) | Wide Area Network (WAN) |
|---|---|---|
| Meaning | A network connecting devices within a small area like a home or office. | A network covering a large distance, often connecting multiple countries. |
| Geographical Area | Very limited (1-2 km). | Vast (100 km to thousands of km). |
| Ownership | Usually private (owned by an individual or organization). | Usually public or leased (Telecom providers). |
| Speed | High data transfer speeds (up to 1000 Mbps). | Lower speeds compared to LAN (varies by provider). |
| Error Rate | Low error rates due to short cable distances. | Higher error rates due to complex routing. |
| Technology used | Ethernet, Wi-Fi. | Leased lines, Fiber optics, Satellite, MPLS. |
| Cost | Low setup and maintenance costs. | High setup and monthly recurring costs. |
A Wide Area Network (WAN) serves as the backbone of global communication. If a LAN is a private conversation in a room, a WAN is the international postal system. It exists to bridge the gap between distant local networks. According to academic resources from Basu.org.in, a WAN is often used by businesses to share data across branch offices located in different regions.
Wide Area Network (WAN) systems don't just happen by accident. They require specialized hardware like routers, switches, and even satellites. Here is the thing: the internet itself is the largest and most complex Wide Area Network (WAN) in existence. It links millions of private and public networks together using the TCP/IP protocol suite.
One might wonder, why not just use a long LAN cable? In reality, physical and regulatory hurdles make that impossible. Instead, a Wide Area Network (WAN) uses service providers to lease communication lines. This allows data to travel over public infrastructure while maintaining a sense of privacy for the user through encryption.
To be honest, setting up a Wide Area Network (WAN) isn't just about plugging in routers. It is about creating a stable bridge for your data to cross oceans and borders. In my experience, many companies struggle with lag and security because their network architecture wasn't built for scale. Have you noticed your remote offices lagging during video calls? That is often a sign that your Wide Area Network (WAN) is hitting a bottleneck.
A Wide Area Network (WAN) functions by using a "Store and Forward" mechanism. When you send a packet of data, it doesn't go in a straight line. It hops through multiple intermediate nodes or routers. Each router receives the packet, stores it briefly to check for errors, and then forwards it to the next best path.
The working of a Wide Area Network (WAN) involves two distinct parts: the Communication Subnet and the Host Machines. The hosts are the computers where applications run. The subnet is the collection of transmission lines and routers that carry the data.
When a host wants to send a message, it breaks the data into small chunks called packets. Each packet contains the destination address. As these packets travel through the Wide Area Network (WAN), routers use routing tables to decide the most efficient path. Does the path change if one line is busy? Absolutely. This dynamic routing makes the network resilient.
Also Read: What is a Wireless LAN Controller? Configuration & Setup 101
To build a functional Wide Area Network (WAN), you need several key pieces of hardware. Without these, the network would just be a pile of disconnected wires.
1. Routers
A router is the most critical device in a Wide Area Network (WAN). It acts as a traffic cop. It examines the destination IP address of incoming data and sends it toward its final destination. In large setups, routers connect different LANs to the main WAN backbone.
2. WAN Switches
While LANs use switches for local devices, a Wide Area Network (WAN) uses high-speed switches to handle data transfer over long-distance circuits. These switches often operate at the Data Link layer of the OSI model.
3. Modems and CSU/DSU
Since many Wide Area Network (WAN) connections use digital lines, you need a Channel Service Unit/Data Service Unit (CSU/DSU). This device converts the signals from the router into a format that the service provider's line can understand. If you are using an older analog line, a modem performs the digital-to-analog conversion.
4. Communication Links
These are the actual paths data takes. A Wide Area Network (WAN) might use fiber optic cables, copper wires, or wireless microwave links. For extremely remote areas, satellite links are the primary choice.
Not all Wide Area Network (WAN) setups are the same. Depending on the budget and the need for speed, organizations choose different technologies to stay connected.
Leased Lines
A leased line is a dedicated point-to-point connection between two locations. It offers high security and fixed bandwidth. However, it is also the most expensive way to run a Wide Area Network (WAN) because you pay for the line even when you aren't using it.
Circuit Switching
Think of this like a traditional phone call. In this Wide Area Network (WAN) type, a dedicated physical path is established for the duration of the connection. It is great for voice but can be inefficient for data that comes in bursts.
Packet Switching
This is the most common technology for a modern Wide Area Network (WAN). Data is broken into packets, and each packet can take a different route. This maximizes the use of the available bandwidth. Technologies like Frame Relay and X.25 fall into this category, though they are being replaced by newer standards.
MPLS (Multi-Protocol Label Switching)
Many businesses prefer MPLS for their Wide Area Network (WAN) needs. It uses labels instead of long network addresses to route data. This makes the process much faster and allows the network to prioritize certain types of traffic, like video calls, over others, like email.
Also Read: Metropolitan Area Network (MAN) - Meaning & Examples
Using a Wide Area Network (WAN) offers several benefits that smaller networks simply cannot provide. Let us look at why companies invest so much in this technology.
While a Wide Area Network (WAN) is powerful, it is not without its headaches. There are several challenges that network administrators face daily.
A Wide Area Network (WAN) is nothing but the glue that holds our digital world together. Without it, we would be stuck in isolated bubbles of information. While it comes with high costs and security risks, the ability to communicate across the globe in an instant is a necessity for any modern organization.
At our firm, we believe that understanding the backbone of your technology is the only way to use it effectively. We focus on providing clear, actionable insights so you can make informed decisions about your networking needs. Whether you are a student or a business owner, knowing how a Wide Area Network (WAN) functions gives you a significant advantage in a connected world.
At our company, we don't just provide technical advice; we build long-term partnerships. We prioritize your connectivity because we know that when your network stays up, your business grows. We value transparency and client success above all else.

Ready to optimize your global connectivity? Our team is standing by to help you design a Wide Area Network (WAN) that is fast, secure, and ready for the future. Contact us today for a network audit and let’s get your team connected the right way!
1. Is the Internet a WAN?
Yes, the internet is the most famous example of a Wide Area Network (WAN). It is a public network that connects billions of devices globally.
2. What is the main difference between WAN and the Cloud?
WAN is the physical and logical infrastructure that connects locations. "The Cloud" refers to the services and storage that you access through that network.
3. Can a small business use a WAN?
Absolutely. Most small businesses use a Wide Area Network (WAN) whenever they connect their office to the internet or use a VPN to let employees work from home.
4. How is a WAN secured?
A WAN is usually secured using VPNs (Virtual Private Networks), firewalls, and end-to-end encryption to prevent unauthorized access.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts