
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025
.jpg&w=3840&q=75)
A proxy server is a server that acts as an intermediary for client requests seeking resources from other servers. This means a proxy server sits between you, the user, and the website or internet service you want to reach.
It plays a vital role in improving security, controlling access, and boosting network performance in corporate or educational environments.
It consists of two essential components: the client (your device) and the target server (the website you want to visit). The proxy server receives your request, processes it, and then forwards it to the destination, acquiring the response for you. This proxy server function is critical for managing data flow and protecting client identities on the web.
In this section, we will discuss the proxy server in detail along with its construction, types, and how this intermediary server protects your network. Proxy servers are a core part of modern computer network infrastructure.
A proxy server refers to a system that acts as an intermediary or gateway between an endpoint user and the internet. Think of the proxy server as a central hub that handles internet traffic for a group of users. When you type a website address, your request first goes to the proxy server, not directly to the destination web server. This internet gateway makes it an essential part of a layered security mechanism.
The primary function of the proxy server is to filter requests, store data in a cache, and mask the client's original IP address. For instance, in an office setting in Dubai, all employees might use a single corporate proxy to access the web. The external website sees the proxy server's IP address, not the individual employee's computer IP. This is a crucial element of network security and data protection policies.
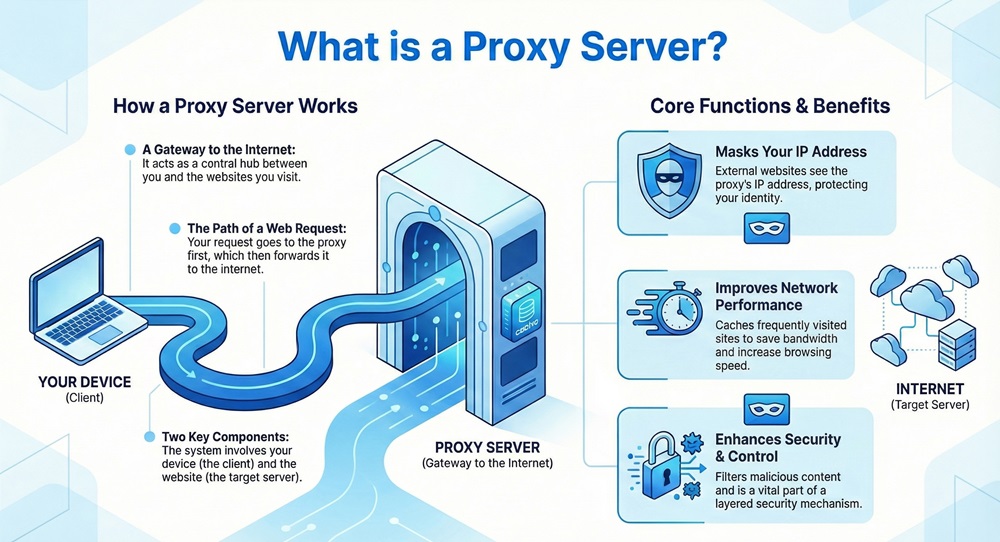
Furthermore, a good proxy server solution can help organizations in the Middle East manage their bandwidth usage efficiently. By storing frequently requested web pages, the proxy server reduces the need to fetch the same data repeatedly from the internet. This action saves bandwidth and makes browsing much faster for the end-user. Does your organization use a proxy server for all its web activities?
Need compliant, high-speed proxy for UAE & GCC regulations?
The construction of the proxy server involves software and hardware components designed to handle high volumes of network traffic. Essentially, a proxy server requires a dedicated computer system running specific software. This software manages the complex tasks of receiving, modifying, and forwarding requests.
The two essential components of a proxy server setup are:
It is composed of different network layers, and each layer handles a specific task. For example, some proxy servers operate at the application layer, which means they can look deeply into the content of a request. Other, faster proxy servers might operate at the transport layer. The configuration of the proxy server must be carefully planned to balance speed and security needs. Observe the figure given below.
Let us now understand the working of a proxy server and the steps it follows to manage your internet requests. The mechanism is simple, yet highly effective for network traffic control.
The process occurs as follows:
Simply put, the proxy server shields the internal network from direct internet exposure. The web server only knows about the proxy server's IP address, which increases the client's anonymity and cyber security. This action is vital for businesses in the Middle East that must comply with strict data sovereignty and privacy regulations.
For example, suppose a user in a Riyadh office tries to visit a news website. The proxy server intercepts this request. If the news page was recently fetched by another employee, the proxy server delivers the cached copy instantly. This speeds up browsing and reduces the load on the company’s internet link, demonstrating effective bandwidth management. This ability to improve network response time is a significant benefit of a good caching proxy.
Also Read: What is a Next Generation Firewall (NGFW)? Why UAE/GCC businesses need it?
The proxy server possesses several characteristics that make it an indispensable tool for computer network management. These features define the various uses and benefits of a proxy server in both enterprise and personal settings.
Following are the key characteristics:
It must be noted that these characteristics make the proxy server a powerful tool for controlling and securing internet usage. A well-configured proxy server acts as a single point for network traffic monitoring and access policy enforcement.
There are several types of proxy servers, each serving a distinct purpose in a network environment. Understanding these types helps in selecting the correct proxy server solution for your specific needs, whether for personal privacy or corporate security in Abu Dhabi.
Let us now discuss the major types of proxy servers:
A forward proxy is the most common type of proxy server. It is used to retrieve data from a range of servers on the internet and deliver it to a set of internal clients. Forward proxies are primarily used in private networks to allow internal users to access the public internet while providing security and administrative control.
For example:
The forward proxy server acts as a chokepoint, forcing all outgoing internet traffic through it. This centralization makes it easy to apply uniform internet access policies.
A reverse proxy works in the opposite direction of a forward proxy. It sits in front of one or more web servers and intercepts requests from external clients before they reach the web server. Reverse proxies are mainly used to improve web server performance, security, and reliability.
For example:
A reverse proxy is a critical component for high-traffic websites and web applications, offering a strong layer of defense and efficiency. This is vital for e-commerce and banking sites operating in the Middle East.
A transparent proxy is a type of proxy server that intercepts and processes client requests without the clients needing to be configured to use it. The user often does not know that their traffic is passing through a proxy server.
For example:
While transparent, this internet gateway still enforces rules and caches content, providing both control and efficiency without any client-side setup.
An anonymous proxy is a type of proxy server that hides your IP address from the website server. The website thinks the request is coming from the proxy server itself, not your device.
Using an anonymous proxy is a common technique for data privacy and bypassing geographical content restrictions.
Also Read: What Is an L3 Switch? L2 vs L3 & Why You Need Layer 3?
The deployment of a proxy server brings many significant benefits, especially for organizations focused on cyber security and network efficiency. These advantages highlight why a proxy server is considered an essential network service.
Following are the benefits of the proxy server:
These advantages demonstrate that a proxy server is not just an optional component but a vital part of a modern network infrastructure.
While the proxy server offers numerous benefits, there are also a few limitations and drawbacks that must be considered before deployment. The proxy server introduces a single point of failure and potential performance issues.
Following are the limitations of the proxy server:
It is to be noted that balancing the benefits of security and control against these performance and reliability risks is key to effective network design.
Also Read: Multi-Factor Authentication (MFA): All You Need to Know
The versatility of the proxy server allows it to be utilized in a diverse range of applications, from basic web browsing to complex corporate network security architecture. Proxy server solutions are deployed globally, including critical sectors throughout the Middle East.
Following are the diverse applications of the proxy server:
For instance, a major bank in Doha would use a combination of forward and reverse proxies. The reverse proxy protects the public-facing banking website from external attacks and distributes traffic. Simultaneously, a forward proxy ensures that employees access only secure, work-related resources.
A proxy server can be understood as an indispensable bridge between your device and the vast network of the internet. It is an essential component for any organization prioritizing network security, performance, and access control. The proxy server ensures client anonymity, offers strong filtering capabilities, and significantly boosts network speed through efficient caching.
These intermediary servers are integral to modern computer network operations, managing everything from basic user requests to complex load balancing for high-traffic websites. The right proxy server solution provides a layered defense, making networks more resilient to external threats and easier to manage.
If your business in the GCC or elsewhere requires better internet security, improved performance, and stricter control over user access, embracing a robust proxy server setup is a powerful strategic move. Our solutions are specifically designed to meet your complex data protection and network management needs.
Worried about web threats? Secure your network with enterprise-grade proxy filtering – book a free Cato SASE demo today!

A Forward Proxy is used by clients inside a private network to reach the public internet, mainly for security and access control. A Reverse Proxy is used by servers inside a network to receive requests from the public internet, mainly for performance (like load balancing) and web server protection.
A proxy server uses a technique called caching. It saves local copies of frequently requested web pages and files. When another user asks for the same resource, the proxy server delivers the cached copy instead of downloading it again from the internet, which reduces external bandwidth usage.
A proxy server offers a high degree of network anonymity because it replaces your device's IP address with its own. However, absolute anonymity is complex. A transparent proxy does not hide this fact, and a highly anonymous proxy must be used to ensure the destination server is unaware that a proxy server is even in use.
A Transparent Proxy is a type of proxy server that intercepts traffic without the user needing to configure their device to use it. Users are often unaware that their traffic is being routed through an intermediary server. This is commonly used in public Wi-Fi hotspots for authentication.
Yes, a core proxy server function is access control and filtering. Administrators can set up rules on the proxy server to restrict access to specific websites, content types, or services, which is widely used in corporate and educational networks.
Yes, a key function of an advanced proxy server is inspection. It can operate at the application layer, allowing it to look at the content of a request (like an HTTP header) to apply security and filtering rules before forwarding the request to the target server.
The biggest drawback is that the proxy server introduces an extra step in every request. Although caching usually speeds things up, the necessary process of checking, logging, and routing every uncached request can sometimes introduce latency and slow down overall connection speed.
A High Anonymity Proxy is a specialized anonymous proxy that takes extra steps to hide its own identity. It conceals the user's IP address and does not inform the destination web server that it is acting as a proxy. This offers the maximum level of IP masking.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts