.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

Intrusion Detection System (IDS) refers to a security tool or software that monitors a network or system for malicious activity or policy violations. Think of it as a digital security guard constantly watching your doors and windows. When it finds a suspicious pattern, it raises an alarm.
This system is an essential part of any strong network defense. Intrusion Detection System (IDS) acts as a crucial layer of defense, especially against threats that bypass firewalls.
In this section, we will discuss the formal definition, the different types, how it works, and the main components of an Intrusion Detection System (IDS).
An Intrusion Detection System (IDS) is a device or software application that monitors a network or system for suspicious activity and identifies potential security threats. Its main function is to observe the environment and find signs of an intrusion.
Intrusion Detection System (IDS) is often defined as the process of monitoring the events occurring in a computer system or network and analyzing them for signs of security problems. It does not actively prevent the attack, but rather detects and reports it. In simple words, an IDS is a warning system.
Note: An IDS finds the problem; it does not stop the problem. This is a crucial difference from an Intrusion Prevention System (IPS).
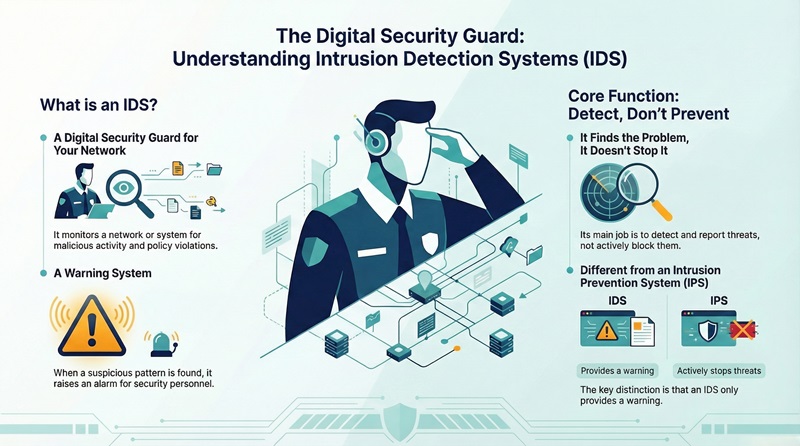
An Intrusion Detection System (IDS) plays a vital role in modern cybersecurity. It provides visibility into what is happening inside the network, a level of detail that firewalls often miss.
Intrusion Detection System (IDS) is important because firewalls are simply not enough. A firewall manages traffic flow but cannot detect an attack that uses an approved protocol, like a web server exploit.
This system helps organizations comply with security standards and provides valuable evidence after an incident occurs. For instance, if an attack happens, the logs from the Intrusion Detection System (IDS) can help trace the attacker's steps.
Activate Cato SASE IDS monitoring now!
The core process of an Intrusion Detection System (IDS) involves three main steps: data collection, analysis, and response.
Every Intrusion Detection System (IDS) is built from several functional units that work together to detect threats.
Intrusion Detection System (IDS) architecture typically includes these elements:
Also Read: What is a Firewall as a Service (FWaaS)?
Not all intrusion detection systems are created equal. They are mainly categorized based on where they are deployed and what type of data they examine. Knowing the different types of Intrusion Detection System (IDS) helps you pick the right defense.
Network Intrusion Detection System (NIDS) monitors all traffic on a specific network segment. It analyzes the header and payload of network packets passing through the network interface.
NIDS sensors are often placed at the perimeter of the network, right after the firewall, or near critical servers. Its main job is to find attacks that cross the network boundary. A single NIDS sensor can monitor traffic for many hosts.
Host Intrusion Detection System (HIDS) runs on a single host, like a server, desktop, or laptop. It monitors the internal activities of that specific system.
HIDS looks at system files, log files, running processes, and application activity. For example, a HIDS would detect if a critical system file was unexpectedly changed. This system is great at spotting attacks that originate inside the host or attempts to exploit vulnerabilities already running on the system.
A Protocol-Based Intrusion Detection System (PIDS) is a system designed to monitor and analyze the communication between devices on specific network protocols.
PIDS is often used to monitor the traffic between a web server and its users, looking for abnormal use of the HTTP protocol. This is an extra layer of protection for key services.
The way an Intrusion Detection System (IDS) detects a threat defines its capabilities and its limitations. There are two primary detection methods: Signature-Based and Anomaly-Based.
A Signature-Based Intrusion Detection System uses a database of known attack patterns, called signatures. This is much like how antivirus software works.
Signature-Based IDS checks the incoming traffic against this list. If a packet or activity matches a known signature, an alert is triggered.
An Anomaly-Based Intrusion Detection System works by first building a profile of normal network or system behavior. This profile includes typical CPU usage, usual network ports, and common connection times.
Anomaly-Based IDS then monitors live activity. Anything that deviates significantly from the established normal profile is considered an anomaly and triggers an alert.
| Basis for Comparison | Signature-Based Intrusion Detection System | Anomaly-Based Intrusion Detection System |
|---|---|---|
| Meaning | This system compares network or system activity to a vast database of pre-defined patterns, called signatures, of known attacks. | This system first establishes a model of normal behavior for a network or host and then flags any activity that deviates significantly from this established baseline. |
| Detection Target | Primarily designed to find known threats, such as malware with existing digital fingerprints or specific exploit code sequences. | Excellent at identifying unknown threats, like zero-day attacks or customized intrusions, by looking for unusual actions. |
| Detection Method | Uses straightforward pattern matching or string searching. It is a one-to-one check against the signature database. | Employs statistical methods, machine learning, or heuristic analysis to create and monitor the normal profile. |
| False Positives | Low. It rarely flags legitimate traffic as malicious because it only alerts on exact matches of known attack patterns. | Higher. Legitimate but unusual activity (like a new application install or a user logging in late) can often be flagged as a potential intrusion. |
| Zero-Day Attacks | Cannot detect. Since a signature for a brand-new, unknown (zero-day) attack does not exist yet, the attack will likely pass through unnoticed. | Can detect. Because it focuses on the behavior change (e.g., an application suddenly accessing sensitive files), it catches the novel attack action. |
| Maintenance | Requires constant, timely updates to the signature database to remain effective against the latest threats. | Requires an initial training period to build the accurate normal baseline and continuous tuning to adapt to system changes. |
| Resource Usage | Generally lower computational overhead, as pattern matching is relatively fast and simple. | Generally higher resource consumption, as analyzing behavior and maintaining complex models demands more CPU and memory. |
It is easy to confuse an Intrusion Detection System (IDS) with an Intrusion Prevention System (IPS). Understanding the difference is vital for designing security architecture.
This key distinction shows the different security objectives. The Intrusion Detection System (IDS) is for awareness and forensics, while the IPS is for real-time defense.
Also Read: Cato SASE vs Zscaler: Which Secure Access Platform Wins on Visibility, Performance, and Simplicity?
While an Intrusion Detection System (IDS) is a powerful tool, it has both strong points and weak points.
Let us consider a few examples to see how the Intrusion Detection System (IDS) works in real-life scenarios.
For example, imagine a large company network.
In both cases, the Intrusion Detection System (IDS) did its job: it monitored, it analyzed, and it reported.
Also Read: Understanding Threat Prevention Policies in Cato
Building a strong defense is not just about blocking threats, but also about understanding them. We believe in providing you with clear, educational content so you can make informed decisions about your digital security. The Intrusion Detection System (IDS) is a powerful sentinel, a necessary tool for visibility and quick response in today's threat landscape.
You should use these systems to move beyond simple walls and start actively monitoring the heart of your operations. Our focus is to deliver clarity in a complex world, ensuring that your security knowledge is as strong as your defense systems.
Achieve effortless IDS defense - Schedule Cato SASE consultation.
We know that understanding the nuances of an Intrusion Detection System (IDS) can lead to more specific questions. Here are ten common questions to help clarify the core concepts of intrusion detection.
A Firewall acts as a traffic police officer. It blocks or allows network traffic based on pre-set rules (like IP address or port number). An Intrusion Detection System (IDS) is a security camera. It watches traffic that has already been allowed by the firewall to see if the activity itself is malicious or suspicious. The IDS alerts; the firewall blocks.
No, an Intrusion Detection System (IDS) is fundamentally a passive tool. When it finds an intrusion, it logs the event and sends an alert to an administrator or another security system. It does not actively block the traffic. To actively stop an attack, you need an Intrusion Prevention System (IPS).
A signature is a unique digital fingerprint or pattern that identifies a specific, known attack. Think of it as the specific code sequence or header data that a particular type of malware uses. The Intrusion Detection System (IDS) compares incoming traffic to this list of signatures to find a match.
A False Positive happens when the Intrusion Detection System (IDS) mistakenly flags normal, harmless activity as a security threat or intrusion. This is a big problem because if the system generates too many false alerts, security teams might become overwhelmed. They could start ignoring the alerts, which means a real attack could be missed.
The two main types are the Network Intrusion Detection System (NIDS) and the Host Intrusion Detection System (HIDS). NIDS monitors all traffic flowing across a network segment. HIDS runs directly on a single device (like a server) and monitors the internal activity of that specific host, such as system calls and file changes.
Yes, this is the biggest strength of the Anomaly-Based Intrusion Detection System. Because this system is trained to recognize normal behavior, any significant deviation from that established baseline is flagged as a potential intrusion. It doesn't need a signature for the attack; it just needs the behavior to look strange.
The NIDS sensor should be placed at a point where it can see all the traffic you want to monitor. A common spot is behind the firewall, often right at the boundary between your external network and your internal network. This ensures it monitors any traffic that the firewall permitted to enter.
The Intrusion Detection System (IDS) helps with compliance (like GDPR or HIPAA) because it provides a complete audit trail. If an intrusion occurs, the IDS logs show exactly what happened, when it happened, and what data might have been accessed. This record-keeping is often a mandatory requirement for regulatory standards.
Running an Intrusion Detection System (IDS) is resource-intensive. HIDS consumes CPU and memory on the host device. NIDS requires significant bandwidth and storage to process and keep records of all the network traffic. Both systems also require expert human resources to constantly update signatures, tune the system, and analyze the complex alerts.
A Zero-Day Attack is an attack that exploits a software vulnerability for which the vendor has zero days of warning or a patch. Since a signature-based Intrusion Detection System (IDS) relies on a known pattern, it has no signature to match against. Therefore, the new, unknown intrusion will pass through undetected until the signature database is updated.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts