
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Do you ever wonder how your computer finds a specific photo among thousands in seconds? Or how a library organizes millions of books so you can find one by a specific author? The secret lies in a hidden layer of information that most people never see. This silent helper organizes our digital world. But what happens when we look closer at this hidden data?
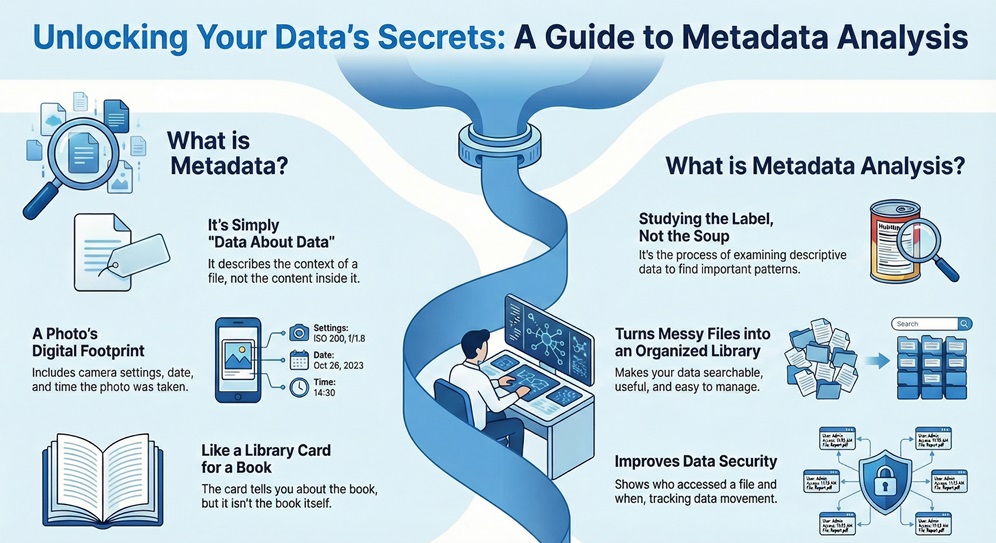
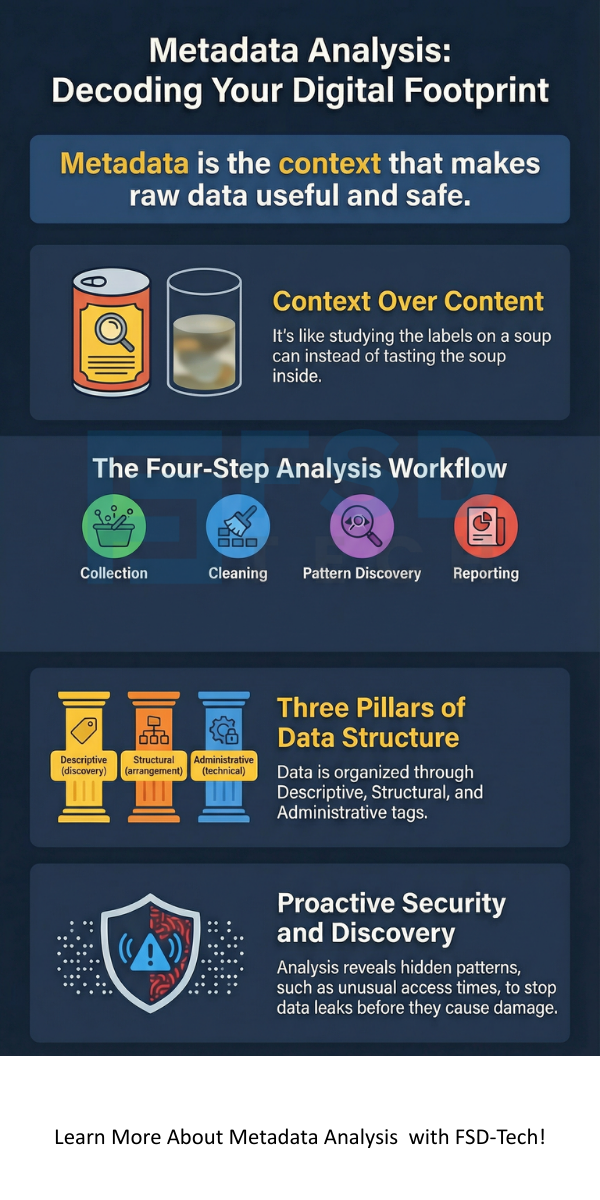
Metadata analysis is the process of examining information about your data rather than the content itself. Think of it as studying the labels on a soup can instead of tasting the soup. You look at file sizes, creation dates, and author names to find patterns.
This analysis helps you organize files and improve security. By checking these digital footprints, you see how data moves through your system. It tells you who accessed a file and when. Metadata analysis turns a messy pile of files into a searchable, safe, and useful library for your business.
To understand metadata analysis, you first need to know what metadata is in its simplest form. Most experts define it as data about data. It does not show the content of a file. Instead, it describes the context. For example, a digital photo has metadata that tells you the date, time, and camera settings. The photo itself is the data. The details about the photo are the metadata.
When you perform a meta analysis meaning in the context of data science, you examine these descriptions to find patterns. You are not reading the book; you are studying the library cards to see which authors are popular this year. Does this help you see the bigger picture? By focusing on these summaries, you gain insights that raw data alone cannot provide.
You might ask, why is metadata important if it does not contain the actual content? Imagine a giant warehouse with millions of boxes but no labels. You would never find anything. Metadata acts as the label on those boxes. It provides the structure needed for discovery and management.
Metadata analysis helps organizations ensure their data is accurate and safe. It allows systems to talk to each other. Without these digital labels, your data remains a messy pile of useless bits. You need these labels to sort, filter, and protect your information.
Also Read: What is Zero Knowledge Proof (ZKP)? Blockchain Technology
People often confuse these two terms. While they sound the same, they serve different goals. Are you looking at a single dataset or a collection of studies?
| Feature | Metadata Analysis | Meta-Analysis |
|---|---|---|
| Primary Goal | Examining file attributes and context | Combining results from multiple studies |
| Data Source | File headers, logs, and tags | Published research papers |
| Common Use | File management and cybersecurity | Medical and social science research |
| Focus | How data was created and stored | Statistical trends across findings |
Are meta analysis primary sources? No, they are secondary sources. They summarize existing research. In contrast, how to analyze metadata often involves looking at primary system logs.
You should understand how metadata works to use it effectively. Most files have a header. This header contains the metadata. When you save a document, the system automatically adds the author name and the save date.
Metadata analysis happens in the final stages. You look at these indexes to find trends. Are most of your files created on Mondays? Do certain users access sensitive files more often? The metadata tells you the story.
Also Read: What is Network Access Control (NAC)? with Process
Learning how to analyze metadata requires a systematic approach. You do not need to be a coding genius to start.
Step 1: Collection
You must gather the metadata from your sources. This might include email headers, file properties, or website tags. Tools like ExifTool or cloud-based data catalogs help with this.
Step 2: Cleaning
Metadata can be messy. Different systems use different labels. You need to standardize these labels so you can compare them.
Step 3: Pattern Discovery
Metadata analysis truly begins here. You look for clusters. For example, in cybersecurity, an analyst might notice many files being edited at 3 AM. This pattern suggests a potential security breach.
Step 4: Reporting
You turn your findings into a visual report. This helps stakeholders understand the health and security of their data environment.
To perform a deep meta analysis meaning check, you should know the three main types:
Metadata analysis often focuses on administrative data for security and descriptive data for marketing. Which one matters most to you?
Also Read: What is Role-Based Access Control (RBAC)?
It powers your search results on Google and helps Netflix recommend movies based on genres you like.
Yes, but you must follow privacy laws like GDPR. While metadata is not content, it can sometimes identify a person.
You can "scrub" metadata from files before sharing them to protect your privacy.
Metadata analysis is the key to mastering your digital landscape. It turns a chaotic sea of files into a well-oiled machine. By understanding what metadata is and how metadata works, you stop guessing and start knowing. You gain the power to find, protect, and use your data better than ever before.
We believe that data should work for you, not against you. Our team focuses on giving you the tools to see clearly through the digital fog. We value your privacy and your need for speed. Are you ready to see what your data is really telling you?
Proactive Metadata Defense Contact our team
Metadata analysis is the process of examining the properties and context of data files. Instead of reading the text inside a document, you look at the file size, the author, and the last edit date. This helps you understand how data moves through your system.
Metadata analysis reveals hidden patterns that might signal a threat. For example, if a user downloads thousands of files at midnight, the metadata flags this unusual behavior. You can stop a data leak before it causes real damage.
Search engines use metadata analysis to rank websites. They look at tags like titles and descriptions to decide if a page matches your search. Without these tags, the search engine would not know what a page is about.
No, they are not. If you are looking at a meta analysis meaning in a scientific sense, it is a secondary source. It summarizes data that already exists in other primary studies to find a broad conclusion.
You can start by right-clicking any file on your computer and selecting "Properties" or "Get Info." This shows you the basic metadata. For larger sets, you use software that can read thousands of these summaries at once to find trends.
Marketers use it to track how people interact with digital content. By looking at when a file was opened and on what device, they can tailor their messages to your habits. It makes their work more personal for you.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts