
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Cyberattacks are growing more sophisticated, and protecting your network requires more than just traditional firewalls. Cato SASE integrates advanced threat prevention policies natively into its global backbone. These policies combine next-generation firewalling, IPS (Intrusion Prevention System), Anti-Malware, DNS Security, and cloud-delivered intelligence to stop threats before they reach your users or applications.
This blog explores how to configure and manage Cato’s threat prevention policies, leverage Managed Threat Intelligence, monitor blocked traffic, and align controls with your organization’s security posture.
Cato delivers multi-layered security across all traffic (WAN and internet) with the following engines:
These engines operate inline, enforcing policies without adding noticeable latency.
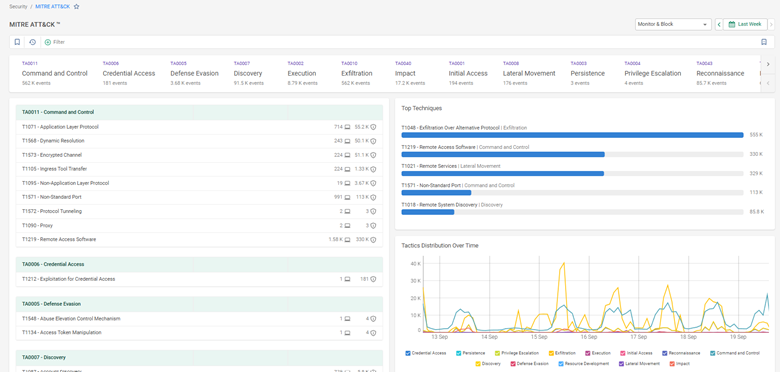
Cato’s backbone leverages Managed Threat Intelligence (MTI) to strengthen prevention:
This intelligence directly feeds IPS, DNS Security, Anti-Malware, and XDR for proactive protection.
Threat prevention in Cato is profile-driven. Each site, socket, or user can inherit a prevention profile, which defines:
Apply the profile to sites, users, or groups.
Sometimes, legitimate applications may trigger false positives. To handle this:
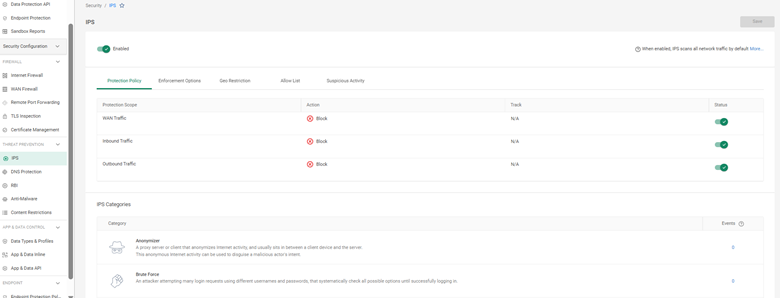
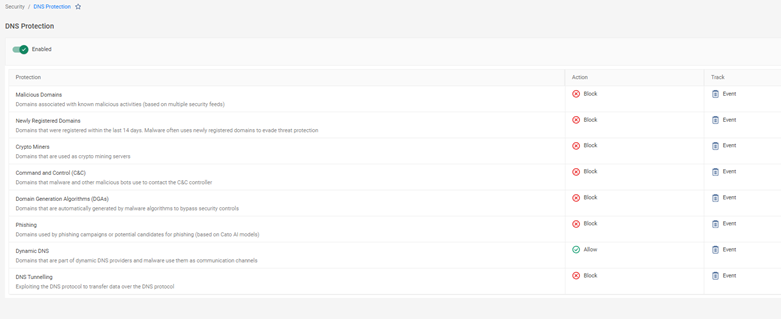
Cato’s IPS policy includes DNS protections for advanced control:
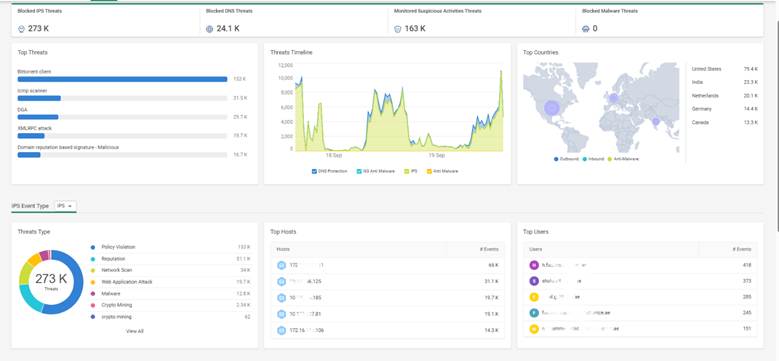
Cato provides detailed visibility into all blocked or allowed threats via:
A financial services firm in Dubai deployed Cato SASE with IPS + Anti-Malware + DNS Security enabled. Within days:
The SOC team used Threat Analytics to review all blocked attempts and reported zero successful breaches.
Book a free consultation with our experts to explore how Cato’s IPS, DNS Security, and TLS inspection can safeguard your network. Book Now

Cato ingests ~250 sources, totaling ~20 million IOCs. After filtering false positives, ~18 million validated IOCs are enforced, updated automatically every ~3 hours.
Yes. IPS can be configured to alert without blocking, useful for testing before enforcement.
When a domain is sinkholed, the malicious query resolves to an internal IP, enabling administrators to trace the compromised host and respond quickly.
You can allow trusted domains, file hashes, or applications in the Anti-Malware policy. Exceptions should be reviewed regularly to avoid exposure.
Yes. TLS inspection enables detection of hidden exploits, malware downloads, and stealth tunneling protocols inside encrypted traffic.

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts