
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026
.jpg&w=3840&q=75)
You probably think your online chats and transactions are private, right? Well, a Man-in-the-Middle attack in cyber security works by secretly inserting itself into the communication path between you and the service you are using. This allows the attacker to spy on, and sometimes even change, the information you send.
MITM attack meaning can be understood as a scenario where a malicious party (the "Man-in-the-Middle") covertly intercepts and relays messages between two parties who believe they are communicating directly with each other. This silent interception happens without either legitimate party knowing about the intrusion.
To understand this better, it is important to note that this type of attack exploits the trust between two communicating systems. We will explore how these attacks work, look at the various types, and show you exactly how to prevent Man-in-the-Middle attack attempts to protect your sensitive data.
A Man-in-the-Middle attack is nothing but an eavesdropping attack which is also active in nature. Active attacks signify that the attacker does not just listen (passive) but actively impersonates one or both parties. The primary objective is stealing data, such as usernames, passwords, credit card numbers, and other sensitive information.
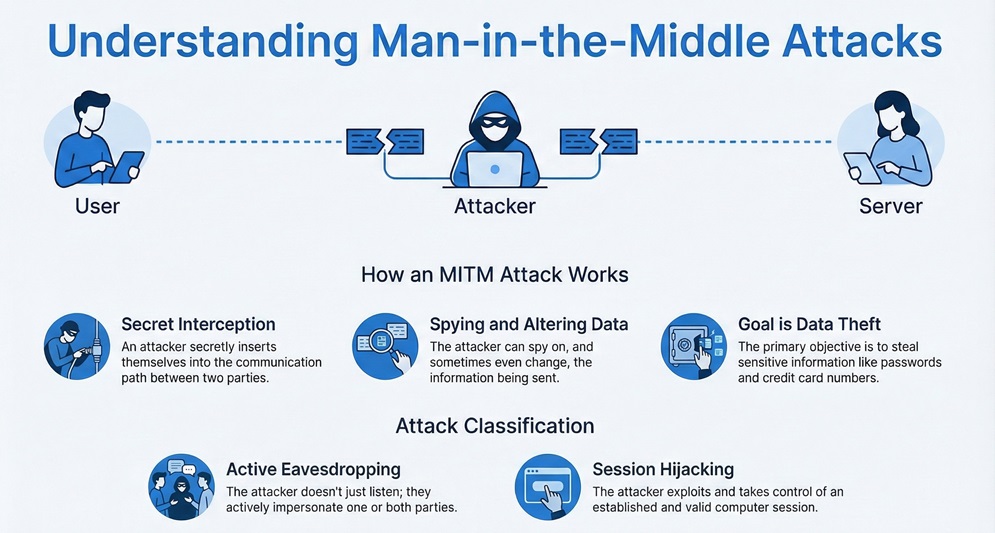
This type of attack is also categorized as a session hijacking technique. Session hijacking refers to the exploitation of a valid computer session, where the attacker takes control of the established connection. The attacker manages to capture the communication traffic between the two systems.
To get a clearer picture of an MITM attack, we compare it with two other common digital threats: Eavesdropping and Distributed Denial of Service (DDoS).
| Basis for Comparison | Man-in-the-Middle (MITM) Attack | Eavesdropping Attack | Distributed Denial of Service (DDoS) Attack |
|---|---|---|---|
| Primary Goal | Intercept, read, and modify communication. | Intercept and read communication secretly. | Overwhelm a system to disrupt service. |
| Activity | Active (impersonates one or both parties). | Passive (only listens to traffic). | Active (sends excessive traffic). |
| Impact on Data | Confidentiality and Integrity are compromised. | Only Confidentiality is compromised. | Availability is compromised. |
| Target | The communication channel (e.g., Wi-Fi, network session). | The communication channel or link. | The specific target server or service. |
| Nature of Attack | A form of session hijacking and impersonation. | A form of spying or wiretapping. | A form of system resource exhaustion. |
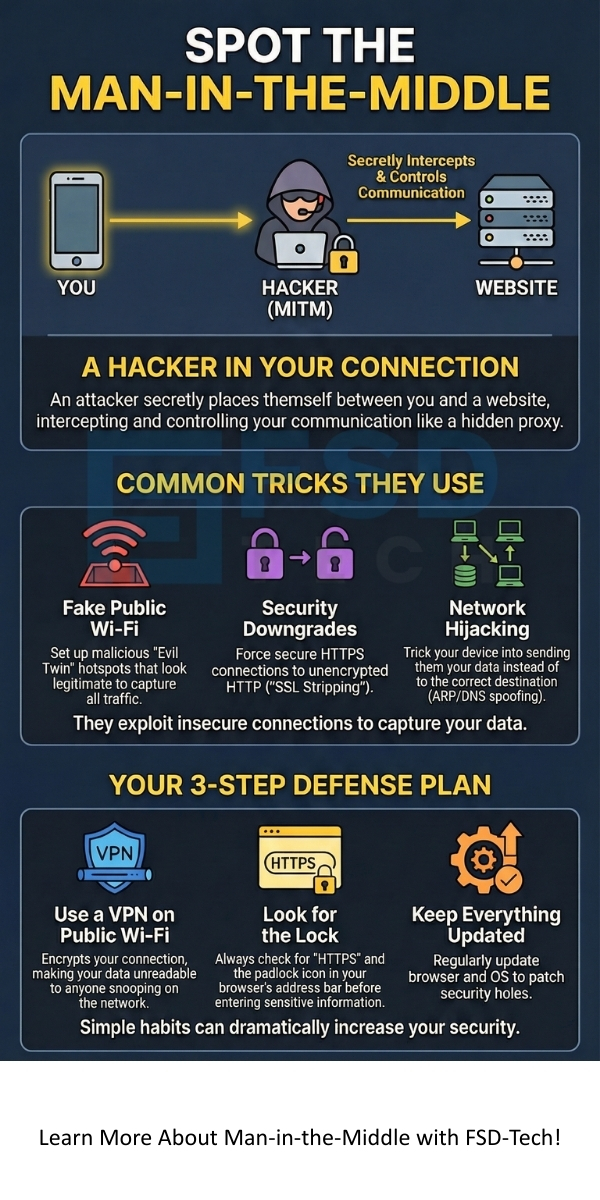
To understand how to stop Man-in-the-Middle attack, you must first know the steps the attacker follows. The attack relies on the attacker secretly positioning themselves between your computer and the legitimate destination, like a bank website.
The MITM attack generally follows a sequential pattern involving three main phases: Interception, Decryption, and Impersonation/Relay.
1. Interception Phase
First, the attacker needs to insert themselves into the communication path. This action is the interception phase. The attacker often exploits insecure connections or protocols.
2. Decryption Phase
Once the connection is intercepted, the attacker receives the encrypted data intended for the original recipient. If the communication uses protocols like HTTPS, the data is encrypted, which means the attacker needs to perform decryption. This is where the term Man-in-the-Middle attack in cryptography comes into play.
3. Impersonation and Relay Phase
Finally, the attacker impersonates the other party. They receive your decrypted data, read it, and then re-encrypt it using the legitimate server's certificate (in a true MITM scenario).
Also Read: What Is Endpoint Detection & Response (EDR) in Cybersecurity?
Several specific techniques fall under the broad umbrella of an MITM attack. Here are some of the most critical Man-in-the-Middle attack types you should know about.
1. ARP Spoofing/Poisoning
ARP Spoofing means the attacker sends forged Address Resolution Protocol (ARP) messages over a Local Area Network (LAN). These malicious messages link the attacker's MAC address with the IP address of a legitimate network device, such as the gateway or another computer.
Due to this, all network traffic intended for that device is instead sent to the attacker. This action leads to a successful MITM setup within the local network.
2. DNS Spoofing/Poisoning
The Domain Name System (DNS) translates human-readable domain names (like google.com) into computer-readable IP addresses. DNS Spoofing corrupts this translation process.
When you try to visit a website, the attacker intercepts the DNS request and sends back a false IP address. This result is that you are unknowingly directed to a malicious website designed to look exactly like the real one.
3. IP Spoofing
IP Spoofing involves creating Internet Protocol (IP) packets with a forged source IP address. This technique is often used to conceal the attacker's identity or to impersonate another device on a network.
The fraudulent packet appears to originate from a trusted host. While primarily used for denial-of-service attacks, IP Spoofing can be a component in more complex MITM schemes.
4. SSL/TLS Hijacking and Stripping
As discussed earlier, these attacks focus on the Secure Sockets Layer/Transport Layer Security (SSL/TLS) protocol, which is the foundation of HTTPS.
5. Wi-Fi Eavesdropping (Evil Twin)
This tactic relies on users' desire for convenience and free internet. An attacker sets up a malicious access point (AP) that mimics a legitimate, popular Wi-Fi network (e.g., "Free Airport Wi-Fi").
When you connect to this "Evil Twin," your traffic does not go to the real internet gateway; it goes through the attacker's device. This gives the attacker a direct pipeline to your data.
Also Read: Domain Name System (DNS) Security | Threats, DNSSEC & Best Practices
Taking into account the various methods an attacker uses, you can implement multiple layers of defense for effective Man-in-the-Middle prevention. Stopping an MITM attack requires vigilance and the correct security tools.
1. For Websites and Organizations
Organizations must focus on strong, modern encryption and proper configuration.
2. For Individual Users
You, the user, play a vital role in securing your communication.
If you suspect a breach, how to remove Man-in-the-Middle attack activity from your system?
Also Read: What is a Botnet? How Botnet Attacks Work & Prevention
The attackers rely on specialized Man-in-the-Middle tools to execute the different attack phases effectively.
So, with the above discussion, we can say that the Man-in-the-Middle (MITM) attack signifies an active, significant threat to the security and integrity of your online interactions. This type of attack successfully intercepts communication by acting as a silent Man-in-the-Middle proxy. The attacker aims at stealing your credentials and sensitive information. You must perform continuous vigilance and apply proper security measures for effective Man-in-the-Middle prevention.
Always ensure your connections utilize HTTPS and use a VPN whenever you connect to public Wi-Fi. Organizations must enforce HSTS and strong TLS protocols. Remember that only applying strong, layered defenses helps to secure your digital conversations and prevents unauthorized access.
We believe that providing you with this knowledge empowers you to make informed decisions about your security. Protecting your data is our shared goal. We are committed to offering clear, actionable security advice that helps you safeguard your digital life. Remember, a well-informed user is the first and best line of defense against any cyber threat. Start securing your connections today!
You now know that a Man-in-the-Middle attack in cyber security represents an active threat to your data's privacy and integrity. It is an active eavesdropping attack that silently inserts itself into your digital communication path.
Here are five frequently asked questions that clarify the Man-in-the-Middle attack meaning and your role in Man-in-the-Middle prevention.
The biggest giveaway is usually the absence of HTTPS or a security warning in your browser when you expect a secure connection (like on banking or email sites). If you try to reach an HTTPS site but see only HTTP in the URL, or if your browser displays a certificate mismatch warning, an attacker is likely attempting SSL Stripping. This acts as a clear signal that someone is positioning themselves as a Man-in-the-Middle proxy.
Yes, they can, but it is much harder. MITM attack in cryptography often targets the initial handshake. Attackers use techniques like SSL/TLS Hijacking or, more commonly, SSL Stripping to force the connection to downgrade from HTTPS to unencrypted HTTP. When you use strong, modern encryption like TLS 1.3, and the website enforces HSTS, the risk reduces significantly, but it requires both parties—the user and the website—to be secure.
Common indicators include: slow or erratic network performance, especially right before a connection request; unexpected logouts from secure sites; and, in sophisticated local network attacks (like ARP Spoofing), you might notice unusual network activity when you inspect your router or network logs. Running a network traffic analyzer can often reveal misdirected packets caused by Man-in-the-Middle attack tools.
Yes, a VPN (Virtual Private Network) is highly effective against external Man-in-the-Middle attack types, especially those occurring on public Wi-Fi. The VPN creates an encrypted tunnel between your device and a secure server. If an attacker intercepts your traffic on the public network, all they see is the VPN's scrambled data. They cannot decrypt it, which completely nullifies their ability to steal or modify your information.
While passwords are the primary target, an MITM attack can also capture virtually any data you transmit. This includes credit card numbers, session cookies (allowing them to hijack your logged-in session without needing your password), confidential emails, private chat messages, and even biometric data if you transmit it over the network. The goal is to compromise the data's confidentiality and integrity.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts