
Executive Visibility in ClickUp – How CXOs Gain Real-Time Control Without Micromanaging
🕓 February 13, 2026

The volume of data you manage from connected devices, like smart cameras or factory sensors, constantly increases. Managing all this data in a distant central cloud computing center creates problems. You encounter high latency, slow reaction times, and big bandwidth costs. You need a better way to process information quickly and locally.
This is where edge computing comes in.
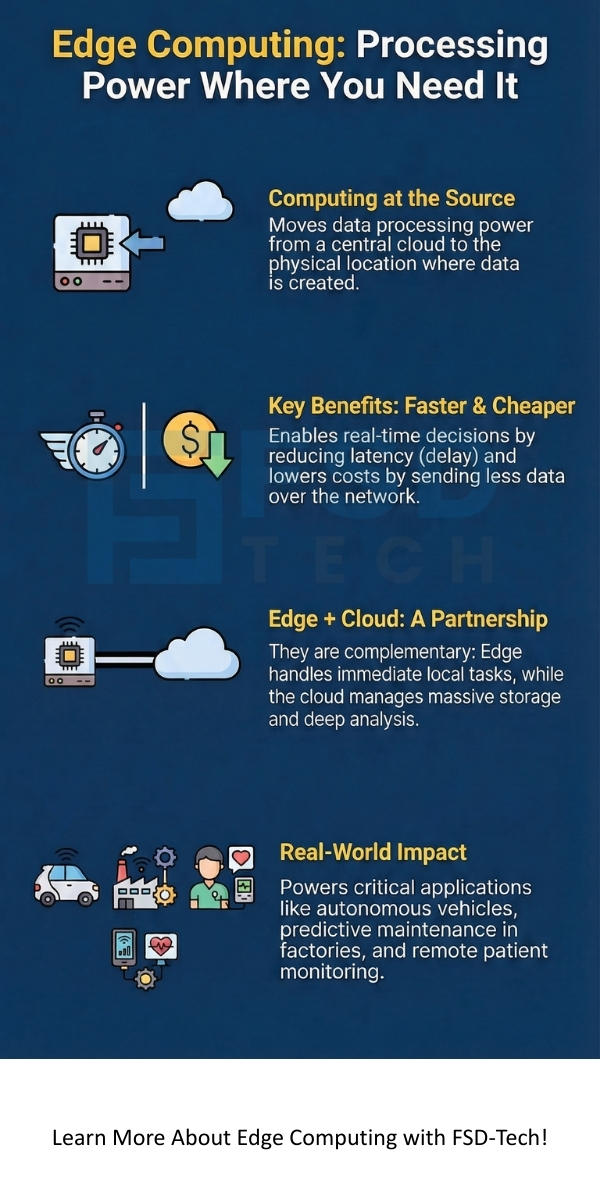
Edge computing is a powerful, distributed information technology (IT) architecture. It moves processing power and data storage closer to the physical location where the data is created. This happens at the “edge” of your network.
We will explore exactly what edge computing is, how it works, and why businesses worldwide are adopting this crucial technology to boost speed and efficiency.
Edge computing can be understood as a computing model. It brings computing resources, such as processing and storage, near the source of data generation. This means that instead of sending all raw data over long distances to a central data center or a large cloud server, you process the critical data right where you gather it.
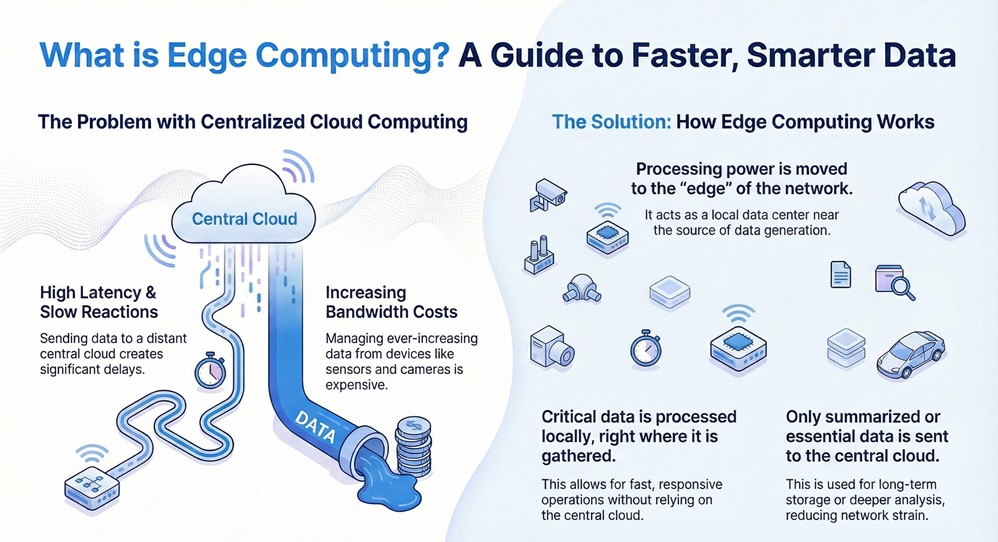
Simply put, edge computing is nothing but a local data center. It lives outside the traditional central facility. It acts as a necessary bridge between the data source and the central cloud.
It is important to note that this technology prioritizes local data processing. Only summarized or critical data then travels to the central cloud for long-term storage or deeper analysis. This systematic process ensures that your operations remain fast and responsive.
The formal edge computing definition refers to the practice of processing data near the generating source, which is at the logical extremes, or edge, of a network.
This implies that the network relies on a vast network of smaller, localized processing devices. These devices, known as edge computing devices, are responsible for collecting, processing, and analyzing data locally. The purpose pattern is to reduce the amount of data sent over the network. This reduction leads to lower latency and better service quality.
In other words, edge computing technology helps you decentralize computing. This offers a major advantage over traditional, centralized models.
Also Read: What is Vulnerability Assessment? Process & Tools
Now, the question arises, why edge computing is becoming a vital part of modern infrastructure. Edge computing provides solutions for several common business and operational problems.
The causation pattern is Due to the massive growth of the Internet of Things (IoT) devices, the sheer volume of data overwhelms central networks. Edge computing provides the necessary framework to manage this data flow efficiently.
Here are the primary reasons why edge computing is essential for your business:
Many people ask about edge computing vs cloud computing. While they both involve processing data, they work on the principle of different operational locations and goals. They are complementary, not competing, technologies.
| Basis for Comparison | Edge Computing | Cloud Computing |
|---|---|---|
| Primary Location | Closer to the data source (the "edge"). | Distant, centralized data centers. |
| Data Processing | Localized, real-time processing of immediate data. | Large-scale analysis, long-term storage, and global access. |
| Latency | Extremely low (milliseconds). | Higher (tens to hundreds of milliseconds). |
| Bandwidth Use | Low (only sends aggregated or critical data). | High (requires high bandwidth for large data transfers). |
| Typical Use Case | Real-time monitoring, industrial control, autonomous vehicles. | Backup, big data analytics, global application hosting. |
| Focus | Speed, immediacy, and operational continuity. | Scalability, massive storage, and general computing power. |
While edge computing focuses on immediate action near the device, cloud computing deals with big-picture analysis and storage. They work together so as to provide a seamless data pipeline, where the edge handles the rapid local needs and the cloud handles the archival and deep learning tasks.
Also Read: What Is Endpoint Detection & Response (EDR) in Cybersecurity?
The edge computing architecture can be understood as a multi-layered structure. This structure allows data to flow efficiently from the source to the final storage location. It is based on three main elements:
1. The Edge Layer
The Edge Layer consists of the edge computing devices themselves. These devices are the physical hardware present at the data generation site.
2. The Fog Layer (Fog Computing vs Edge Computing)
The Fog Layer acts as a bridge between the Edge and the Cloud. This is where the concept of fog computing vs edge computing becomes relevant.
Fog computing refers to a distributed computing structure. It extends cloud processing capabilities down towards the local area network (LAN) level. It is distinct from edge computing in terms of location.
The purpose is to provide more complex computing, storage, and networking services closer to the end devices than the central cloud.
3. The Cloud/Core Layer
The Cloud/Core Layer comprises the traditional, centralized data centers.
How edge computing works is based on this sequential flow. Data is born at the edge, aggregated in the fog, and stored/analyzed long-term in the cloud.
Edge computing in IoT is one of the most significant applications of this technology. The Internet of Things (IoT) is nothing but a network of physical objects embedded with sensors, software, and other technologies. These devices collect and exchange data with other systems over the internet.
The problem arises when an IoT system generates a massive, continuous data stream. For example, a wind farm with hundreds of turbines continuously generates operational data. Sending terabytes of this raw data to a distant cloud for immediate failure detection is inefficient.
Edge computing in IoT solves this problem. The edge devices (i.e., the controllers inside the turbines) perform simple, real-time anomaly detection.
This allows for instant reaction times. This functionality is critical for industrial automation, smart cities, and especially for mobile edge computing applications.
Also Read: Unified Threat Management (UTM): Key Security Functions
To understand the practical impact of edge computing, consider these specific examples:
The advantages of implementing edge computing solutionsare numerous and significantly improve business operations.
Edge computing can be used to improve sustainability by making energy use more efficient. Smart grid systems rely on edge devices to monitor and regulate energy flow in real time. They ensure that power is distributed exactly where and when it is needed, which helps in reducing overall waste and optimizing the use of renewable energy sources.
Also Read: What Is Spyware Software? Types, Signs & Removal Guide
Selecting the right edge computing solutions involves choosing the correct hardware and software.
Mobile edge computing (MEC) meaning refers to the deployment of cloud-computing capabilities within the radio access network (RAN) close to mobile subscribers.
MEC* aims at bringing IT and cloud-computing resources into the cellular base stations. This allows for extremely low-latency applications for mobile users.
For example, streaming a live event in Virtual Reality (VR) to a mobile user requires incredibly fast data delivery. The MEC platform provides this necessary speed by hosting the content server directly within the local carrier network, closer to your phone.
Therefore, MEC plays a vital role in enabling future technologies like 5G networks, autonomous driving, and advanced augmented reality (AR) experiences.
Edge computing is a critical shift in how you manage the overwhelming flow of modern data. It signifies moving intelligence out of the centralized cloud and placing it at the network’s edge, where data is created. This fundamental change provides the necessary speed and responsiveness required for real-time applications, such as autonomous vehicles and predictive maintenance in factories.
By reducing latency and cutting bandwidth costs, edge computing plays a vital role in increasing your operational efficiency and security. We are here to help you integrate these powerful edge computing solutions so as to ensure your business remains fast, resilient, and ready for the future of connected technology. Contact us today to optimize your data flow.
Key Takeaways
Based on our discussion, here are the crucial points you should keep in mind about edge computing:
Mobile Edge Computing (MEC) meaning implies that the edge server is positioned inside the mobile carrier's network, often at a base station. This focuses on improving the experience for mobile users. Fog computing, on the other hand, is a more general term for any intermediate layer of processing between the core cloud and the edge devices. MEC is a specific type of fog computing.
No, edge computing vs cloud computing are complementary. Edge computing handles immediate, time-sensitive processing locally, while the cloud provides vast resources for long-term storage, deep analysis, and global data management.
An edge gateway is nothing but a buffer device. It acts as a central collection point for several local edge computing devices. The gateway performs pre-processing, translation of data formats, and secure transmission of the aggregated data up to the cloud or fog layers.
In retail, a popular edge computing example is smart inventory tracking. Edge cameras monitor shelf stock and immediately alert staff when an item needs restocking. Another example is the use of local servers to process point-of-sale transactions so as to ensure rapid checkout, even if the main internet connection is slow.
An edge computing platform provides the necessary software. It helps in centrally managing, deploying, and updating the applications running on all of your geographically distributed edge computing devices. This simplifies the complex management and maintenance of the entire system.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts