.webp&w=3840&q=75)
How ClickUp Enables Outcome-Based Project Management (Not Just Task Tracking)
🕓 February 15, 2026

In today's digital world, businesses rely on a vast network of external partners, vendors, and software components. Your organization trusts these relationships to keep operations running smoothly. However, this interconnected ecosystem also creates serious vulnerabilities. Are you confident that the code or hardware you integrate into your system is completely secure?
Supply chain attacks represent a major and increasing threat to cybersecurity worldwide. These specific attacks target an organization indirectly. They aim at weaker links within the network of suppliers that provide components, software, or services to the main company. A successful supply chain attack allows threat actors to bypass the strong, established defenses of the primary target. This method of compromise ensures persistent access for the attacker.
We will explore what this sophisticated threat is and what it means for your security posture. This discussion will detail the core concepts, outline the various forms this attack takes, and provide concrete steps you can take today. Understanding this risk determines whether your system remains secure or falls victim to the current, stealthiest form of digital espionage.
A supply chain attack can be understood as a type of cyber threat. It aims to damage an organization by compromising elements within the trusted chain of suppliers and services. The core target is not the final company directly. Instead, attackers seek to insert malicious code, hardware, or components into the products or services that the main company later utilizes.
The term supply chain attacks definition refers to the exploitation of inherent trust. Organizations place a high level of trust in their vendors, software updates, and manufacturing partners. This trust serves as the entry point for the attacker. The action plays a vital role in modern cyber warfare because a single successful intrusion can compromise thousands of customers downstream.
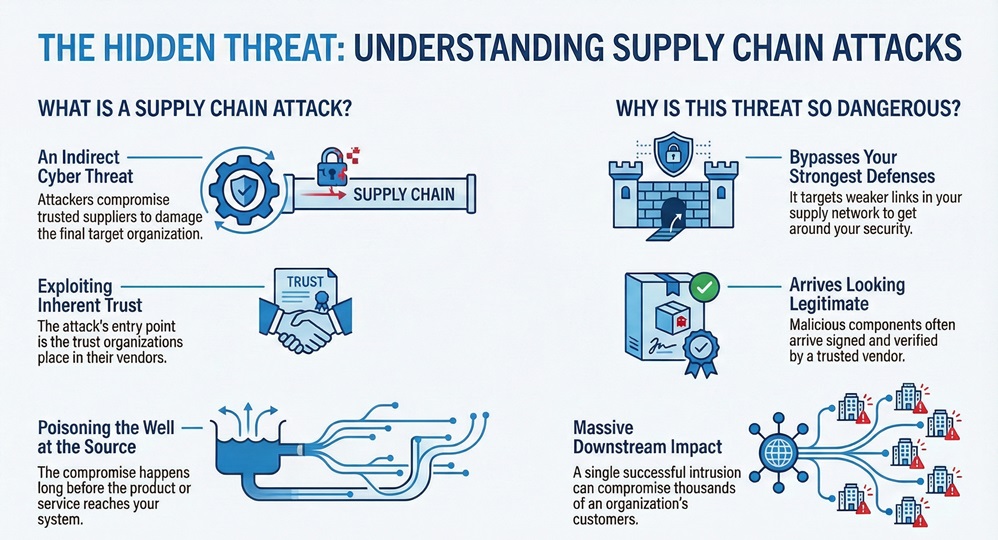
Supply chain attacks are particularly dangerous because the malicious component often arrives signed and verified by a trusted vendor, appearing completely legitimate to the victim's security systems.
The compromise happens long before the product or service reaches your environment. The attacker successfully poisons the well at the source. Thus, the security of your system now depends entirely on the security practices of your upstream partners.
To understand the unique danger, let us compare a supply chain attack with a traditional direct attack.
| Basis for Comparison | Supply Chain Attack | Traditional Cyber Attack |
|---|---|---|
| Target of Initial Compromise | A third-party vendor, supplier, or component manufacturer. | The primary victim's own network perimeter (e.g., firewall). |
| Goal of Attack | Inserting malicious functionality into trusted products or code. | Bypassing a direct security measure to gain initial access. |
| Trust Exploited | High trust placed by the victim in their certified vendor. | No trust; the attacker must use deception (e.g., phishing). |
| Impact | Widespread; can affect numerous users or clients instantly. | Localized; typically affects only the targeted organization. |
| Detection | Highly difficult. Malicious payload is signed by a trusted entity. | Easier. Relies on detecting known intrusion attempts or malware signatures. |
The term types of supply chain attacks signifies that this threat is not limited to a single method. The threat vector can include any element that moves from an external source into your environment. Such elements include hardware, software, network components, and data services.
Supply chain attacks comprise three main categories. Let us now discuss these categories in detail.
This category is the most prevalent in modern security breaches. Software supply chain attacks specifically target the code and development ecosystem used to create software. The core idea is to compromise the source of the application itself.
Software supply chain attacks typically occur in various ways. These attacks include injecting malicious code into open-source libraries that developers widely use. The compromise also involves tampering with the code repositories or the build pipeline of a trusted software vendor. For instance, if a hacker compromises a popular update server, all users downloading the next legitimate patch automatically receive the malware. This process allows the malicious code to run with the high permissions of a legitimate application.
A supply chain attack may also target the physical components of computing devices. This type of attack is much harder to execute but delivers a highly persistent threat. Hardware attacks involve tampering with devices during manufacturing. Attackers plant chips, sensors, or modified components into the final product.
The malicious component can serve several purposes. It might capture sensitive data, provide a covert communication channel, or disable the system at a specific time. Firmware attacks, on the other hand, target the low-level software embedded within hardware devices like routers or hard drives. Compromising the firmware ensures that the malicious code executes before the operating system and remains undetected by common antivirus programs.
This type of supply chain attack focuses on the services and data providers you rely on. Think about managed service providers (MSPs), cloud service brokers, or outsourced data processing firms. You grant these third parties extensive access to your network, often for legitimate administrative or support purposes.
The attack happens when the threat actor compromises the third-party provider's system. They then use that trusted connection and existing access permissions to pivot into your network. This method is highly effective because your security monitoring often expects and permits traffic coming from your trusted vendor's IP address range.
Also Read: Man-in-the-Middle (MITM) Attack - Prevention Guide
To understand how to mitigate supply chain attacks, you must first comprehend the process an attacker follows. The action unfolds sequentially.
History provides clear evidence of the severity and reach of this threat. Examining famous supply chain attacks helps in understanding the real-world consequences.
The widely cited SolarWinds attack serves as a prime example. In this instance, attackers injected malicious code into an update for SolarWinds' network management software, Orion. When thousands of organizations downloaded this legitimate software update, they simultaneously installed the backdoor. The supply chain attack cyber security impact of this single event affected multiple US government agencies and major corporations.
Another critical example is the NotPetya malware. This particular threat was disguised as an accounting software update in Ukraine. The malicious payload was released through a compromised software update mechanism, affecting companies across the globe. This action caused billions of dollars in damage. This attack demonstrated that compromising one widely used piece of software can trigger a catastrophic global ripple effect.
Also Read: Brute Force Attack in Cybersecurity - How it Works?
If you want to know how to prevent supply chain attacks, you must adopt a security posture that treats every external component as potentially risky. You must minimize trust and verify everything. Organizations cannot simply rely on their own perimeter defenses.
Supply chain attacks necessitate a shift in security thinking. You should enforce strong controls across your entire vendor ecosystem. This step is because the compromise often originates from a place you traditionally trust. You must establish a continuous process of verification, even for well-known and reputable partners.
You prevent supply chain attacks by implementing a layered defense strategy. This strategy focuses on controlling what goes into your system and constantly monitoring what happens after it arrives.
Mitigation requires systematic effort. How to mitigate supply chain attacks involves specific actions that reduce the probability and impact of a compromise. Let us now discuss the most crucial steps you should implement.
Supply chain attacks represent one of the most dangerous and sophisticated cyber threats today, exploiting trust in third-party vendors, software updates, and hardware components to infiltrate even the most fortified organizations. By compromising a single trusted link, attackers can achieve widespread, persistent access with devastating impact, as seen in high-profile incidents like SolarWinds and NotPetya.
Prevention demands a zero-trust mindset, rigorous vendor risk management, mandatory Software Bills of Materials (SBOM), strict least-privilege access, network segmentation, and continuous monitoring.
Stop Supply Chain Attacks Contact FSD-Tech today

In this section, we will discuss some common questions regarding supply chain attacks cyber security.
Software supply chain attacks refer to attacks that compromise software development components. They aim at the source code, libraries, build tools, or distribution mechanisms. The goal is to inject malicious code into a legitimate application that reaches end-users without raising suspicion. This means the attacker avoids targeting the end-user directly.
The primary method involves poisoning an artifact (software package, hardware component, or configuration file) at the source. This is because the victim's system inherently trusts the source. This action allows the attacker to use the vendor's credibility to bypass strong security defenses.
A supply chain attack uses third parties because their security is often less rigorous than the final, primary target. Attacking the third party provides an easier, indirect route into a highly secure network. This method leverages the complex web of business trust to gain unauthorized access.
Strong encryption helps by ensuring the integrity of the communicated data. Encrypting code repositories and software updates ensures that an attacker cannot tamper with the data without leaving verifiable evidence. When the software arrives, the recipient can confirm the package has not been modified since the vendor signed it.
The most important defense is zero trust architecture. This architecture operates on the principle of "never trust, always verify." It requires strict identity verification for every person and device attempting to access network resources. This step ensures that even if a component is compromised, its access within the network is strictly limited.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts