
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Cybersecurity is a vital aspect of your digital life. You secure your accounts with passwords, assuming they are safe. But, do you really know how a determined attacker tries to break those passwords? Let us understand a major threat in digital security: the brute force attack.
This type of attack is nothing but a persistent guessing game carried out by a machine. An attacker uses specialized software to automatically try every possible combination of characters until they find the correct password or decryption key. It is worth noting that this approach relies on sheer computational power and time to ultimately gain unauthorised access to your system or data.
As we know, this method is often effective against weak or simple passwords; understanding the mechanism and defences is crucial for robust protection against brute force attacks. How do attackers carry out this tireless task, and more importantly, how can you stop a brute force attack before it succeeds? We will explore these critical questions and provide you with actionable steps to safeguard your accounts.
The brute force attack can be understood as a trial-and-error method an application program uses to decode encrypted data, such as passwords or hidden web pages. In simple words, the attacker tries every potential key or password until the correct one works. This approach relies on repeatedly attempting to guess the required information.
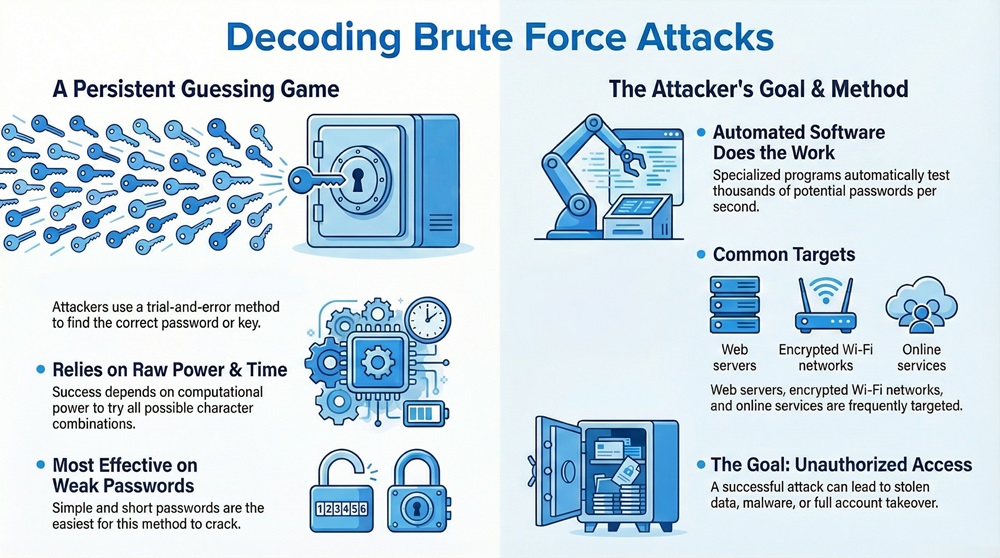
This method typically targets web servers, encrypted Wi-Fi networks, and online services. A successful brute force attack in cybersecurity means the attacker now possesses your credentials, allowing them to steal data, install malware, or even take control of your entire account. The primary goal is to define brute force attack as an attempt to compromise security by exhausting all possibilities.
The fundamental working principle of a brute force attack is systematic trial. The attack process generally involves these sequential steps:
But, how does a brute force attack work so fast? Due to the immense processing speed of modern computers, the tools can test millions or even billions of combinations per second.
Also Read: Dictionary Attack in Cybersecurity - How it Works and How to Stop?
While both methods aim to guess passwords, they differ significantly in their approach. Understanding this contrast is essential for forming a comprehensive brute force attack protection strategy.
| Basis for Comparison | Brute Force Attack | Dictionary Attack |
|---|---|---|
| Strategy | Tries every possible combination of characters. | Tries combinations based on a list of common words, phrases, and passwords. |
| Time Required | Can be very long, depending on password length and complexity. | Generally faster, but only if the password is on the list. |
| Success Rate | Guaranteed success eventually, provided enough time and computational power. | Lower success rate against strong, complex, or unusual passwords. |
| Wordlist Use | Does not primarily rely on a pre-compiled wordlist. | Heavily relies on a pre-compiled wordlist or 'dictionary'. |
| Complexity | High complexity; tests random strings. | Lower complexity; tests known, commonly used strings. |
The term brute force attack is a general category. Attackers employ several specific methods under this umbrella, each with a slightly different focus. Let us now discuss the major types of brute force attack.
1. Simple Brute Force Attack
This is the most basic form, which simply tries all combinations. It does not use any specific intelligence, like wordlists or previously known credentials. This means that a simple brute force attack requires the most time and computational effort.
2. Dictionary Attack
A dictionary attack is an evolved form. It significantly reduces the time required by starting with common passwords, phrases, and words from a dictionary file. This attack aims at a faster result when a user chooses a non-complex word-based password.
3. Reverse Brute Force Attack
In this unique method, the attacker already knows the password, which is often a commonly used one. They then use the password to try to find the corresponding username. This helps in finding multiple accounts that share the same common password. For example, the attacker might try the password "password123" against millions of usernames.
4. Credential Stuffing
This type of attack refers to the use of compromised username/password pairs from a data breach on one service to attempt logins on a large number of other services. The attacker relies on the fact that many users reuse the same login credentials across various platforms.
5. Hybrid Brute Force Attack
The hybrid approach combines elements of simple brute force and dictionary attacks. It takes dictionary words and then adds variations like numbers or symbols at the beginning or end. For example, it might try "password123!" or "Summer2025" for a better chance of success. This approach tends to be more effective and efficient than a simple dictionary attack.
Also Read: What is Credential Stuffing? Detection and Prevention
The brute force attack plays a vital role in understanding the security strength of cryptographic systems. What is brute force attack in cryptography? It refers to the process of trying every possible key to decrypt a message or break a cipher.
In this context, the security of an encryption algorithm is often measured by the total time it would take a powerful computer to carry out a successful brute force key search. The strength of the encryption depends on the key length.
This attack indicates that strong encryption is nothing but the usage of a sufficiently long key space.
A key that is too short allows the attacker to break the cipher in a reasonable amount of time. Therefore, brute force attack in information security often acts as a benchmark for security strength.
The key to preventing a brute force attack lies in making the process computationally and temporally expensive for the attacker. You must implement multiple layers of defense to significantly reduce the risk.
1. Enforce Strong Passwords and Passphrases
The simplest defense is a complex password. Strong passwords comprise of a mix of upper and lower-case letters, numbers, and symbols, and must be at least 12-16 characters long. Longer, non-dictionary passwords exponentially increase the time needed for a successful guess.
2. Implement Rate Limiting and Account Lockout
Rate limiting allows the system to restrict the number of login attempts from a single IP address within a specific timeframe (e.g., 5 attempts in 5 minutes).
3. Use Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a critical defense mechanism. Even if the attacker successfully guesses the password, they cannot access the account without the second factor. This second factor is usually a code sent to a mobile device or generated by a hardware key. 2FA ensures that the password alone is not enough to gain entry.
4. Deploy CAPTCHAs
A CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) helps in distinguishing between a human user and an automated script. Requiring the completion of a CAPTCHA after a few failed login attempts eliminates the use of most brute force attack tools.
5. Monitor and Analyze Login Traffic
Systematic monitoring of login attempts is based on checking for unusual activity.
Such monitoring indicates an ongoing brute force attack in network security, allowing the administrator to block the suspicious IP address immediately.
6. Change Default Credentials
Many systems come with default usernames and passwords (like "admin/admin"). Attackers often target these well-known defaults first. You must change all default credentials immediately after setting up any new system or server.
Also Read: What Is a Whaling Attack? How It Works & Prevention
To stop the attack on a server, you must configure the firewall or the web application firewall (WAF) to block IP addresses showing too many failed login attempts in a short span. Using services like Fail2ban helps in automatically blacklisting these malicious IPs.
In brute force attack in information security, a significant aspect of brute force attack protection involves how you store passwords on your server. When a user creates a password, the system should not store the password in plain text. Instead, it generates a one-way cryptographic hash of the password.
Hashing and Salting
The server stores the salt and the salted hash. When you log in, the system applies the same salt to the password you enter, hashes the result, and compares it with the stored salted hash. If the two hashes match, access is granted. This approach makes the brute force attack significantly harder because the attacker must brute force the hash of each individual, unique, salted password, rather than a single common hash.
The brute force attack is a patient, tireless guessing method that aims to compromise your credentials. Understanding this attack, from its basic meaning to the types of brute force attack, empowers you to build stronger defenses. You must employ crucial measures like strong, unique passwords and the mandatory use of Two-Factor Authentication (2FA).
Implementing account lockout policies and ensuring proper password hashing and salting significantly increases the cost and time required for an attacker to succeed. Robust brute force attack protection requires continuous vigilance and layered security. We believe that informed action is your best defense against unauthorized access, helping you maintain a secure and resilient digital presence.
We are committed to helping you implement robust brute force attack protection measures and secure your digital environment. Your security is our priority, and we provide the expert support and solutions you require to stay ahead of the threats.
Contact us today to understand how we can further strengthen your defense strategy.

To protect your personal and corporate assets from a brute force attack, remember these essential steps:
A. Brute force attack simply means trying every possible password or key until the correct one is found. It is an automated, tireless guessing game played by a computer.
A. A brute force attack aims at unauthorized access by guessing credentials. Conversely, a Distributed Denial of Service (DDoS) attack focuses on overwhelming a server with traffic, making it unavailable to legitimate users.
A. Strong passwords cannot completely prevent the attempt, but they reduce the chance of success to near zero. A complex password with 16 characters requires too much time for a successful brute-force guess, even with the most powerful computers.
A. Yes, there are tools available online. However, using any tool for an unauthorized brute force attack against a system is considered illegal and unethical. You should use these tools only for educational purposes and on systems where you have explicit permission.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts