
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

In the modern world of software development, security often feels like a race against time. Have you ever wondered how major companies keep their applications safe before they even go live? Many organizations rely on a specific method to catch bugs while the code is still being written. This method is known as Static Application Security Testing (SAST).
Imagine finding a tiny crack in a building's foundation before the walls even go up. That is exactly what static application security testing does for software. It allows developers to scan their work for hidden dangers without ever running the program. This proactive approach saves thousands of dollars and prevents massive headaches later.
But how does it actually work? And why is everyone talking about "shifting left" in the security world? Let us dive into the details of this essential security practice.
What is static application security testing exactly? In simple terms, it is a "white-box" testing method. This means the tool has full access to the internal "blueprints" of your application. The static application security testing process involves analyzing the source code, bytecode, or binaries of an application.
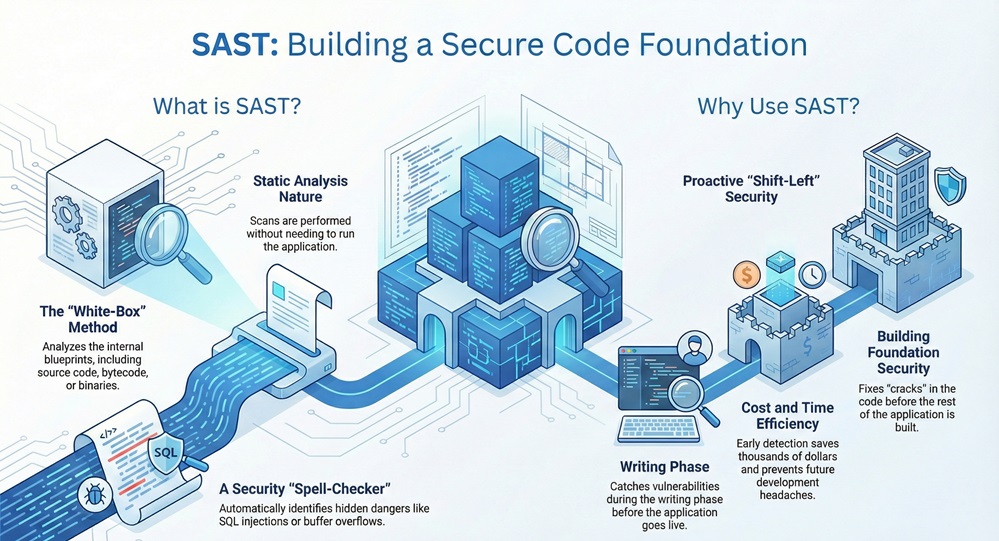
Unlike other methods, what is static application security testing (SAST) is defined by its "static" nature. The application does not need to be running for the scan to work. This makes it an ideal choice for the very first stages of development. It acts like a spell-checker, but instead of looking for typos, it looks for security holes like SQL injection or buffer overflows.
When you look for the best static application security testing software, you will often see it compared to Dynamic Application Security Testing (DAST). While static application security testing sast tools look at the code from the inside, DAST looks at the running app from the outside.
| Basis for Comparison | SAST (Static) | DAST (Dynamic) |
|---|---|---|
| Approach | White-box (Internal) | Black-box (External) |
| Requirement | Source code access | Running application |
| Timing | Early development (Coding/Build) | Testing/Production phase |
| Vulnerabilities | Code-level flaws (e.g., SQLi) | Runtime issues (e.g., Config errors) |
| Feedback | Real-time for developers | Post-execution for security teams |
| False Positives | High | Low |
Also Read: What is Dynamic Application Security Testing (DAST)?
SAST static application security testing follows a very systematic process. It does not just "read" the code; it builds a deep model of how the data flows.
Static application security testing sast tools offer a unique advantage because they help you "shift left." This means you move security to the beginning of your timeline.
While static application security testing software is powerful, it is not a magic wand. There are some hurdles you should know about.
Sast static application security testing often struggles with "false positives." This happens when the tool flags a piece of code as dangerous even though it is perfectly safe. Dealing with these reports can take up a lot of time.
Also, SAST cannot see what happens during runtime. If your server is misconfigured or your API has a logic flaw that only appears when running, a static scan might miss it. This is why most pros recommend using a mix of both static and dynamic tools.
Also Read: What is Hash Function? Data Integrity and Security
You might hear people use the terms static code analysis vs static application security testing interchangeably. Are they the same thing? Not quite.
Static code analysis is a broad category. It focuses on the quality, style, and maintainability of the code. It checks for things like "dead code" or "messy formatting."
On the other hand, SAST is a specific type of static analysis. It focuses strictly on security. While code analysis wants your code to be "pretty," SAST wants your code to be "safe."
If you are looking for the best static application security testing software, the market has several top-tier options. Each tool has its own strengths depending on your coding language.
Also Read: What is Security Information and Event Management (SIEM)?
Are you ready to bring static application security testing services into your team? Success depends on how you set it up.
Sast static application security testing works best when it is "invisible." You should integrate it directly into the Integrated Development Environment (IDE). This way, the developer gets a little red underline the moment they write an insecure function.
You should also tune your rules. Don't try to catch everything on day one. Start with the most critical issues, like injection attacks. As your team gets used to the tool, you can turn on more advanced checks.
The world of static application security testing sast tools is changing fast. By 2026, AI has become a standard part of these platforms. Modern tools no longer just "find" the problem; they "fix" it too.
AI-powered agents can now suggest the exact patch needed to close a security hole. This reduces the "noise" of false positives and lets your developers focus on building new features instead of chasing ghosts in the code.
Securing your software does not have to be a reactive game of "whack-a-mole." With static application security testing, you can build a culture of safety from the very first line of code. We believe that security is not just a checkbox; it is a core value that protects your users and your reputation.
Our team is dedicated to helping you find the right static application security testing sast tools to fit your unique workflow. We focus on clear results and human-centered support so you can ship your products with total confidence.
Is your code safe? Speak with a security architect today to find the right SAST solution for your team. Book a Free Consultation

Static application security testing is a cornerstone of modern cybersecurity. By scanning code early and often, you stop threats before they ever reach a user.
You should use it as early as possible. The best time is during the coding phase, before the code is even committed to the main branch.
No, but it makes them much faster. A human might miss a tiny logic flaw in a million lines of code, but a tool will find it in seconds. Use the tool for the "easy" stuff so your humans can focus on complex logic.
Not at all. Static application security testing software works for mobile apps, desktop software, and even embedded systems. If there is source code, you can use SAST.
SAST looks at the code you wrote. Software Composition Analysis (SCA) looks at the third-party libraries and "open-source" bricks you used to build your house.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts