
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Cloud access security broker (CASB) acts as a gatekeeper between cloud service users and cloud applications. As organizations move their data to the cloud, they face new risks that traditional firewalls cannot handle. Have you ever wondered how your company keeps data safe when employees access apps from home? A cloud access security broker (CASB) addresses this exact concern by sitting between the cloud service provider and the cloud consumer.
Cloud access security broker (CASB) ensures that network traffic complies with the security policies of the organization. It provides a central location for policy and governance. By using a cloud access security broker (CASB), you gain visibility into "Shadow IT," which refers to apps used by staff without official approval. This technology helps you manage risks across Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS) environments.
What is the cloud access security broker meaning in a practical sense? It is a security policy enforcement point. It can be a local or cloud-based software. It consolidates multiple types of security policy enforcement. These include authentication, single sign-on, authorization, credential mapping, device profiling, and malware detection.
A cloud access security broker definition describes it as a software tool or service that resides between an organization's on-premises infrastructure and a cloud provider's infrastructure. The cloud access security broker (CASB) functions by intercepting data. It then applies security rules before allowing the data to reach the cloud or the user.
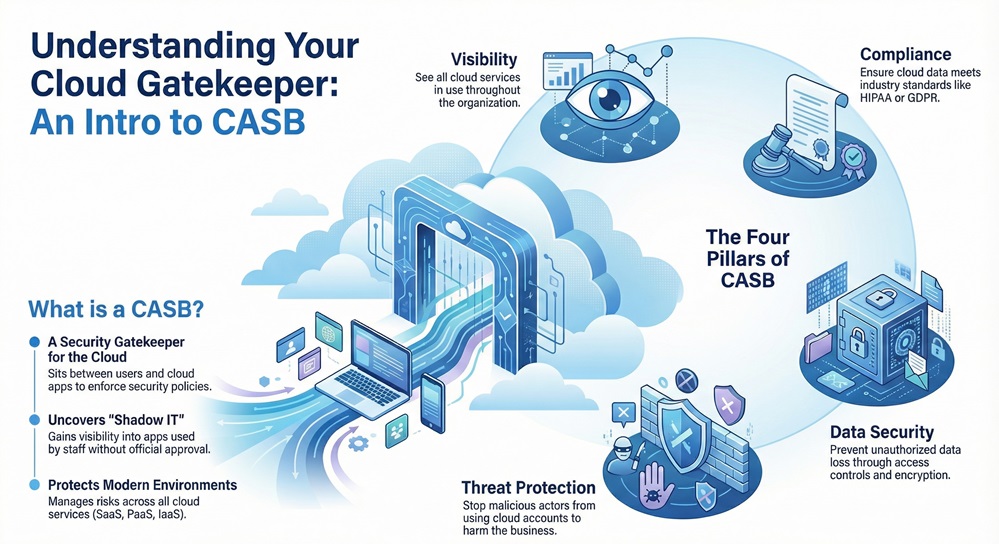
Cloud access security broker (CASB) solutions focus on four main pillars: visibility, compliance, data security, and threat protection. Visibility allows you to see all cloud services in use. Compliance ensures that you meet industry standards like HIPAA or GDPR. Data security involves preventing unauthorized data loss. Threat protection stops malicious actors from using cloud accounts to harm the business.
Why do you need cloud access security broker tools today? Traditional security tools were built for a world where data stayed inside an office building. Now, data lives in the cloud. A cloud access security broker (CASB) provides the specific controls needed for this modern setup. It allows you to protect data even when it is on a server you do not own or manage.
To understand the cloud access security broker (CASB) better, let us look at how it can be deployed. Different businesses have different needs. The following table compares the three primary ways to implement this technology.
| Basis for Comparison | API-Based CASB | Forward Proxy | Reverse Proxy |
|---|---|---|---|
| Primary Function | Connects directly to cloud providers via backend APIs. | Sits in front of the user to monitor outbound traffic. | Sits in front of the cloud app to monitor inbound traffic. |
| Visibility | Provides data at rest visibility. | Provides data in motion visibility. | Provides data in motion visibility. |
| Device Support | Covers managed and unmanaged devices. | Mainly for managed devices with agents. | Supports unmanaged (BYOD) devices. |
| Installation | No agent required on the user device. | Requires agent or local configuration. | No agent required on the user device. |
| Real-time Control | Generally near real-time (not instant). | Excellent real-time control. | Excellent real-time control. |
| Use Case | Best for scanning files already in the cloud. | Best for enforcing corporate policies on-site. | Best for securing access from personal laptops. |
The cloud access security broker (CASB) architecture is designed to handle the complexities of modern networking. It works through a "broken" connection model where it terminates the connection from the user and starts a new one to the cloud. This allows the cloud access security broker (CASB) to inspect every packet of data.
Cloud access security broker (CASB) systems use various methods to identify users and devices. They check if a user is who they claim to be. They also check if the device is healthy and updated. If a user tries to download a sensitive file to an unmanaged phone, the cloud access security broker (CASB) can block that specific action while still allowing the user to view the file in a browser.
How does a cloud access security broker (CASB) identify hidden apps? It uses discovery features to analyze web logs. By looking at these logs, the cloud access security broker (CASB) creates a list of every cloud service being accessed. It then gives each service a risk score. This helps you decide which apps to allow and which ones to block.
Also Read: How the Cato Client Becomes the Identity Anchor for Zero Trust Access
The cloud access security broker use cases are diverse and solve many common security problems. One primary use case is the prevention of data leakage. Many employees accidentally share folders with "anyone with the link." A cloud access security broker (CASB) can automatically find these public links and change them to private.
It also include stopping account takeovers. If a hacker steals an employee's password, they might try to log in from a different country. The cloud access security broker (CASB) detects this "impossible travel" and blocks the login attempt. This keeps your corporate data safe even if passwords are compromised.
Another vital cloud access security broker (CASB) use case is shadow IT discovery. Employees often use free online PDF converters or project management tools. These tools might store your data insecurely. The cloud access security broker (CASB) alerts you to these apps so you can provide safer alternatives.
The leading cloud access security brokers for sase are those that integrate with Secure Access Service Edge. SASE is a framework that combines network security with wide-area networking. A cloud access security broker (CASB) is a core part of this framework. When you look for the leading cloud access security brokers for sase, you should prioritize those that offer a unified management console.
Leading cloud access security brokers for sase help you move away from having too many separate security products. Instead of managing five different tools, you manage one cloud-native platform. This reduces the chance of human error. It also makes it easier for your IT team to respond to threats quickly.
What makes the leading cloud access security brokers for sase stand out? They offer deep integration with other tools like Zero Trust Network Access (ZTNA) and Secure Web Gateways (SWG). This creates a seamless security layer that follows the user everywhere. Whether you are at the office, a coffee shop, or at home, your security remains the same.
Also Read: Device-Aware WAN Firewall Policies in Cato SASE
Finding the best cloud access security broker for unified sase depends on your specific infrastructure. Some providers excel at protecting Microsoft 365, while others are better for multi-cloud environments. The best cloud access security broker for unified sase will provide consistent policy enforcement across all your cloud platforms.
The best cloud access security broker for unified sase should also be easy to deploy. You do not want a tool that takes months to set up. Modern cloud access security broker tools use API connections to start protecting your data in minutes. This speed is crucial in a fast-changing business world.
Another factor for the best cloud access security broker for unified sase is performance. Security should not slow down your work. High-quality cloud access security broker (CASB) solutions use global networks of data centers. This ensures that the security check happens very close to the user, minimizing lag.
Many cloud access security broker examples show how the technology works in the real world. For instance, a financial company might use a cloud access security broker (CASB) to ensure that no Social Security numbers are uploaded to a public cloud. The broker scans every file for specific number patterns and blocks the upload if it finds a match.
Cloud access security broker examples also include healthcare organizations. These groups must protect patient records under strict laws. A cloud access security broker (CASB) can ensure that only authorized doctors can access certain files from specific locations. If a doctor tries to access files from a public Wi-Fi, the broker can enforce a more secure login method.
In the retail industry, cloud access security broker examples often focus on protecting credit card data. The broker monitors all traffic to cloud-based point-of-sale systems. It ensures that data is encrypted before it leaves the store. This prevents hackers from intercepting valuable customer information during transmission.
When you start looking at cloud access security broker solutions, you must first assess your current cloud usage. You cannot protect what you do not know about. Use cloud access security broker tools to run a discovery report. This report will show you exactly which cloud services your team is using today.
Cloud access security broker solutions require a clear set of policies. You must decide what data is sensitive. Is it your customer list? Your source code? Your financial projections? Once you define these, you can program your cloud access security broker (CASB) to watch over them.
Choosing between various cloud access security broker solutions involves testing. Most vendors offer a trial period. During this time, you should check if the tool integrates well with your existing identity provider. You should also see if it correctly identifies the apps your team uses most often.
Also Read: Gain Real-Time Endpoint Intelligence with the Cato Device Dashboard
Effective cloud access security broker tools offer a range of features to keep you safe. One such feature is User and Entity Behavior Analytics (UEBA). This technology learns what "normal" behavior looks like for your users. If a user who usually downloads five files a day suddenly tries to download five thousand, the cloud access security broker (CASB) will sound an alarm.
Cloud access security broker tools also provide robust encryption options. Sometimes, you want to encrypt data before it even reaches the cloud provider. This is called "bring your own key" (BYOK). It ensures that even if the cloud provider is hacked, your data remains unreadable to the attackers.
Furthermore, cloud access security broker tools help with device management. They can check if a laptop has its antivirus turned on. They can check if a phone has a passcode. If the device does not meet your security standards, the cloud access security broker (CASB) can limit what that user can do in the cloud.
Cloud access security broker (CASB) is no longer an optional tool for big companies. It is a necessity for any business that uses the cloud. Without a cloud access security broker (CASB), you are essentially blind to what happens with your data once it leaves your network.
Cloud access security broker (CASB) gives you the confidence to adopt new cloud technologies. You do not have to say "no" to every new app your employees want to use. Instead, you can say "yes" because you have the tools to monitor and secure those apps. This balance of security and productivity is what makes a business thrive.
Does your current security plan include a cloud access security broker (CASB)? If not, you might have a massive gap in your defenses. The cloud is a powerful tool, but it requires a different kind of protection. A cloud access security broker (CASB) provides that protection by keeping your data safe, your users productive, and your company compliant.
Selecting a cloud access security broker (CASB) provider requires careful thought. You should look for a partner that understands your industry. Some cloud access security broker solutions are built specifically for highly regulated fields like banking or healthcare.
Check the vendor's list of supported applications. A cloud access security broker (CASB) is only useful if it can "talk" to the apps you use. Most leading cloud access security brokers for sase support thousands of popular apps. However, if you use custom or niche software, ensure the broker can handle it.
Finally, consider the support and training offered. A cloud access security broker (CASB) is a sophisticated tool. Your team will need to learn how to manage it effectively. The best providers offer extensive documentation and responsive support teams to help you get the most out of your investment.
The move to the cloud brings many benefits, but it also changes the security landscape. You can no longer rely on traditional tools to keep your data safe. A cloud access security broker (CASB) provides the visibility and control you need to protect your business assets. By implementing the right cloud access security broker solutions, you ensure that your team stays productive without compromising on safety.
At FSD-Tech, we believe that security should enable your business, not hinder it. We focus on providing clear, effective, and human-centric security advice. Our goal is to help you navigate the complexities of the cloud with ease. We put your needs first, ensuring that every solution we recommend adds real value to your organization. Let us help you build a safer future in the cloud today.

Secure your cloud journey today. Book a CASB Strategy Session
A firewall protects your internal network from the outside world. A cloud access security broker (CASB) protects your data when it is already outside your network in the cloud. Firewalls cannot see into the specific actions happening inside a cloud app, but a cloud access security broker (CASB) can.
Most modern cloud access security broker tools use high-speed cloud networks to minimize latency. While any security check adds a tiny bit of time, the difference is usually not noticeable to the user. Using an API-based cloud access security broker (CASB) has zero impact on user speed.
No, small and medium businesses also use cloud access security broker solutions. Because many smaller companies rely heavily on cloud apps like Google Workspace or Microsoft 365, they are actually at high risk. There are cloud access security broker (CASB) options designed for teams of all sizes.
Yes, a cloud access security broker (CASB) can help stop ransomware. It does this by detecting unusual file activity, such as a large number of files being encrypted at once. It can also block the download of known malicious files from the cloud into your network.
Shadow IT refers to apps and services used by employees without the IT department's knowledge. A cloud access security broker (CASB) finds these apps by looking at your network traffic. It helps you bring these apps under corporate control or block them if they are too risky.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts