
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Have you ever wondered how hackers break into huge databases? Many people think cyber attacks always involve complex codes or expensive tools. However, one of the most common threats is much simpler. It involves tricking a website into running hidden commands. This guide will help you understand what is SQL injection attack in cyber security and how it impacts your digital safety.
SQL injection meaning refers to a type of cyber attack where a hacker inserts malicious code into a database query. By doing this, the attacker can view data they are not supposed to see. This might include customer details, private messages, or even credit card numbers. Because many websites rely on databases to store information, what is SQL injection vulnerability remains a top concern for developers globally.
How does a simple search bar or login box become a weapon for a hacker? While it sounds like a movie plot, it happens every day. In the next few sections, we will explore how SQL injection works and provide a sql injection with example to clarify the process.
Is your website leaking data? Get a Professional Vulnerability Scan
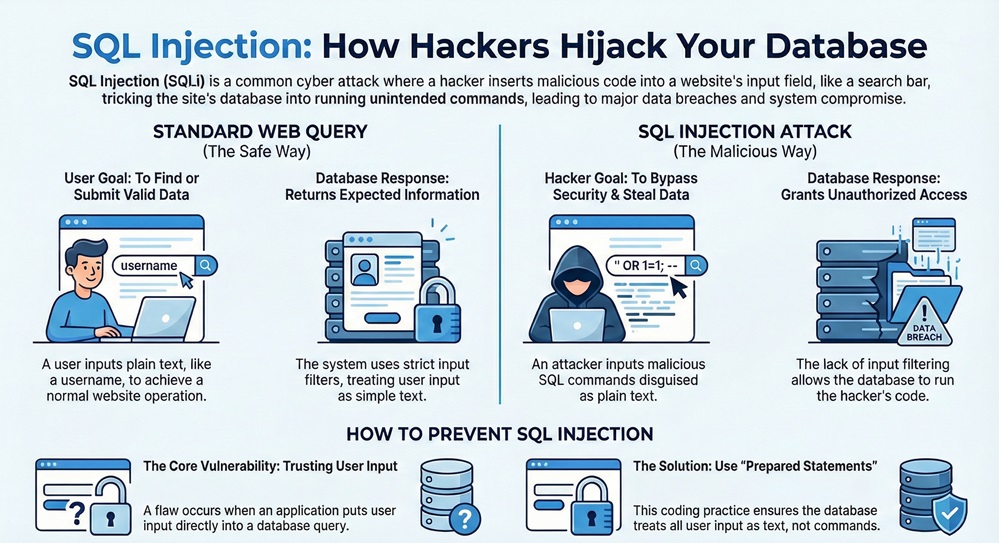
To understand what sql injection truly is, we must look at how it differs from a normal, safe request. The following table highlights the core differences.
| Basis for Comparison | Standard Web Query | SQL Injection Attack |
|---|---|---|
| User Intent | To find or submit valid data. | To bypass security and steal data. |
| Input Type | Plain text (e.g., a username). | Malicious SQL commands. |
| Database Response | Returns requested information. | Grants unauthorized access or control. |
| Validation | Uses strict input filters. | Exploits lack of input filtering. |
| Result | Normal website operation. | Data breach or system shutdown. |
SQL injection meaning starts with the way a website talks to its database. Most sites use a language called Structured Query Language (SQL). When you type your name into a form, the website sends that name to the database to find your account.
Instead of just sending a name, the hacker sends a piece of SQL code. If the website does not check the input, the database runs the hacker's code. This allows them to "inject" their own commands into the system.
What is SQL injection vulnerability in a technical sense?
It is a flaw in the web application's code. This flaw occurs when the application takes user input and puts it directly into a database query without cleaning it first. This is like leaving your front door unlocked and hoping no one walks in.
Prevent sql injection by using modern coding habits. Developers should never trust what a user types. You must assume every input is a threat. By using specific tools like "prepared statements," you can make sure the database treats all input as simple text, not as a command.
Also Read: Cato SASE and DNS Security: Preventing and Mitigating DNS-Based Attacks
Sql injection involves a few specific steps. First, the attacker finds a place on a website that accepts user input. This could be a login page, a search bar, or a feedback form. They then test this field by entering special characters like a single quote (').
SQL injection looks for an error message. If the website shows a database error, the hacker knows the site is vulnerable. They then craft a "payload." This payload is the actual malicious code designed to trick the database.
An SQL injection attack in cyber security researchers call a "classic" exploit? It is the "OR 1=1" trick. The hacker enters this phrase into a login box. Because 1 always equals 1, the database sees the statement as "true." This often lets the hacker log in without a password.
SQL injection with example logic:
Imagine a login query: SELECT * FROM users WHERE username = 'admin' AND password = 'password123'.
The hacker types ' OR '1'='1 in the password box.
The query becomes: SELECT * FROM users WHERE username = 'admin' AND password = '' OR '1'='1'.
The database sees that "1=1" is true and logs the hacker in as the admin.
What sql injection types exist? While the goal is usually the same, the methods vary. Some are quiet and slow, while others are fast and loud.
What is sql injection vulnerability risks for each type?
In-band is dangerous because it is fast. Blind SQLi is dangerous because it is hard for security tools to detect. All types can lead to a total loss of data privacy.
Does sql injection still work in a world of advanced firewalls? Yes, it does. Even though we have known about this threat for over twenty years, it remains a top risk on the OWASP Top 10 list.
SQL injection meaning has stayed the same, but hackers have become more clever. Many old websites still use outdated code. Even new sites can be vulnerable if developers rush their work or forget to use security libraries.
Trends show is that automated tools now do the work. Hackers use bots to scan thousands of websites per hour. These bots look for any tiny gap where they can slip in a command. If your site is online, it is a target.
It requires a "defense in depth" strategy. This means you do not rely on just one security layer. You build multiple walls to protect your data.
Prevent sql injection by using Parameterized Queries. This is the best way to stop the attack. It tells the database exactly what is code and what is data. Even if a hacker enters a command, the database will just see it as a long, weird piece of text.
Prevention of SQL injection also involves using a Web Application Firewall (WAF). A WAF acts like a filter. It looks at all incoming traffic and blocks anything that looks like a malicious SQL command. While it is not perfect, it stops most basic attacks.
What is sql injection and how to prevent it for beginners?
Also Read: Cato SASE Implementation Roadmap 2025: A Step-by-Step Guide
How can sql injection attacks be prevented at the code level? Let us look at the "Prepared Statement" method. When a programmer uses this, they send the query structure to the database first. Later, they send the user's data.
What is sql injection vulnerability protection? By separating the command from the data, the database never mixes them up. This makes it impossible for the user's input to change the intent of the query.
How sql injection can be prevented through input validation is also vital. If a form asks for a zip code, the code should reject anything that is not five numbers. If a hacker tries to type a SQL command, the system will simply say "Invalid Input" and stop the process.
Does SQL injection still work because of human error? Most of the time, yes. Writing secure code takes time and training. Sometimes, a developer might use a "quick fix" that leaves a hole in the security.
What is SQL injection attack in cyber security experts worry about? They worry about legacy systems. These are old programs that companies still use but no longer update. These systems often use very old versions of SQL that are easy to hack.
SQL injection meaning also extends to the "Supply Chain." This means the tools or plugins you use on your website might have a vulnerability. Even if your own code is perfect, a buggy plugin could let a hacker in.
What SQL injection damage looks like can be scary. If you think you have been hacked, you must act fast. First, take the affected system offline. This prevents the hacker from stealing more data.
What is SQL injection and how to prevent it after the fact? You must find the hole. Look through your server logs to see what commands the hacker used. Once you find the vulnerable code, patch it immediately using the methods discussed.
SQL injection with example recovery steps:
We believe that every business deserves a secure digital presence. Cyber threats are always changing, but our focus on client safety never wavers. We work hard to stay ahead of hackers so you can focus on growing your brand. Our team values transparency, excellence, and the protection of your data above all else. Let us build a safer digital future together.
Need help securing your legacy code? Consult with our Security Engineers

The main goal is to gain unauthorized access to a database. Hackers want to steal, change, or delete sensitive information.
Basic attacks are very easy and can be done by beginners using free tools. However, "Blind" SQL injection requires more skill and patience.
No. A firewall is a great tool, but it cannot see everything. The best protection is writing secure code from the start.
Any language that talks to a database can be vulnerable. This includes PHP, Python, Java, .NET, and many others.
You should scan your website every time you update the code. Regular monthly scans are also a good habit for any business.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts