
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

In today’s hybrid work environments, managing which applications are allowed—or restricted—on your corporate network is critical to both productivity and security. Cato’s Application Control engine provides granular control over user behavior and application usage across the WAN and internet.
With the updated Cato Management Application (CMA), defining and enforcing application policies is both streamlined and deeply integrated into traffic visibility. In this blog, we’ll walk you through how to configure, monitor, and optimize Application Control policies using the current CMA interface—no guesswork, no outdated tabs.
Application Control allows you to:
This feature is available for all customers with Threat Prevention enabled.
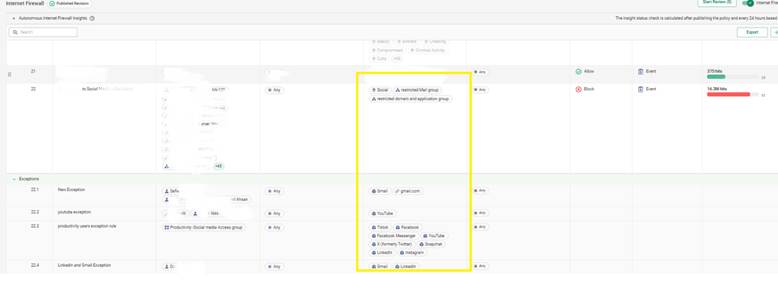
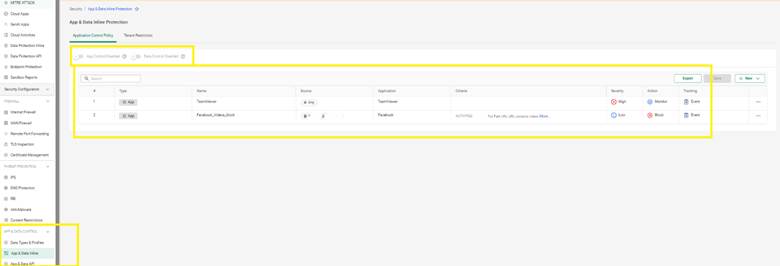
Let’s say your compliance policy prohibits the use of personal file-sharing platforms like Dropbox or WeTransfer, but you still want to allow corporate OneDrive.
Solution:
This keeps your file policies clean while enabling visibility on violations.
Monitor enforcement success and violations using:
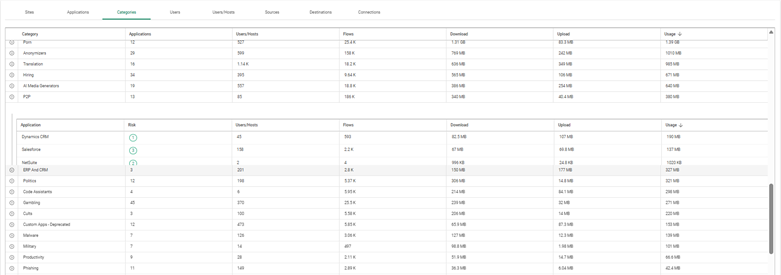
Use this data to:
No, but enabling TLS inspection improves classification accuracy.
Yes, but only when Cato’s DLP (Data Loss Prevention) is enabled.
Analytics data is near real-time; logs are updated every few minutes.
Yes. Rules apply to all users connected via the Cato Client.
Yes. You can define custom apps based on IP/port/domain and use them in Application Control rules.
With Cato Application Control, your IT team can effectively strike the balance between enabling productivity and enforcing security. Start with a few high-impact policies and evolve them as your network visibility improves. Click Here To Know More

Anas is an Expert in Network and Security Infrastructure, With over seven years of industry experience, holding certifications Including CCIE- Enterprise, PCNSE, Cato SASE Expert, and Atera Certified Master. Anas provides his valuable insights and expertise to readers.
Share it with friends!
share your thoughts