
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025
.jpg&w=3840&q=75)
Have you ever wondered how security experts keep track of every move a hacker makes? The world of digital threats feels like a giant maze. One wrong turn can lead to a massive data breach. Most people think of cyber attacks as random acts of chaos. But what if there was a map that showed exactly how these attackers think?
The MITRE ATT&CK framework acts as that map. It is a massive, living database of real-world hacker behaviors. Instead of just looking at what a virus does, it looks at the steps a person took to get it there. It changes the way we look at defense.
But how does it work? Why do global companies rely on it every day? In this guide, we will look at how this tool helps you stay one step ahead of the bad guys.
The MITRE ATT&CK framework can be understood as a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge. Unlike other security models, this framework focuses on the perspective of the attacker.
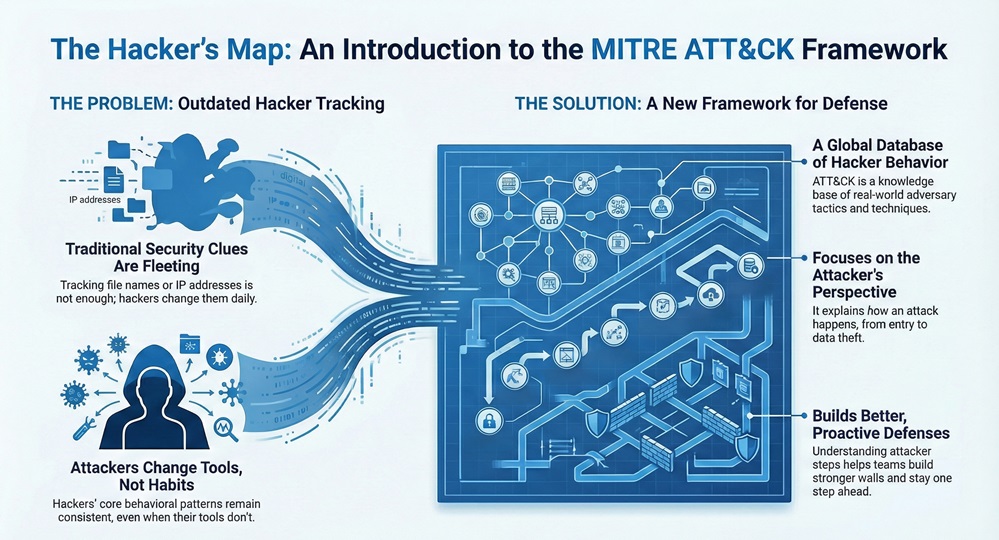
MITRE ATT&CK framework explained simply is a list of the "how-to" steps used by hackers. It does not just tell you that you were hacked. It explains how the attacker got in, how they moved through your network, and what they tried to steal. This information helps teams build better walls.
Ready to close your security gaps?
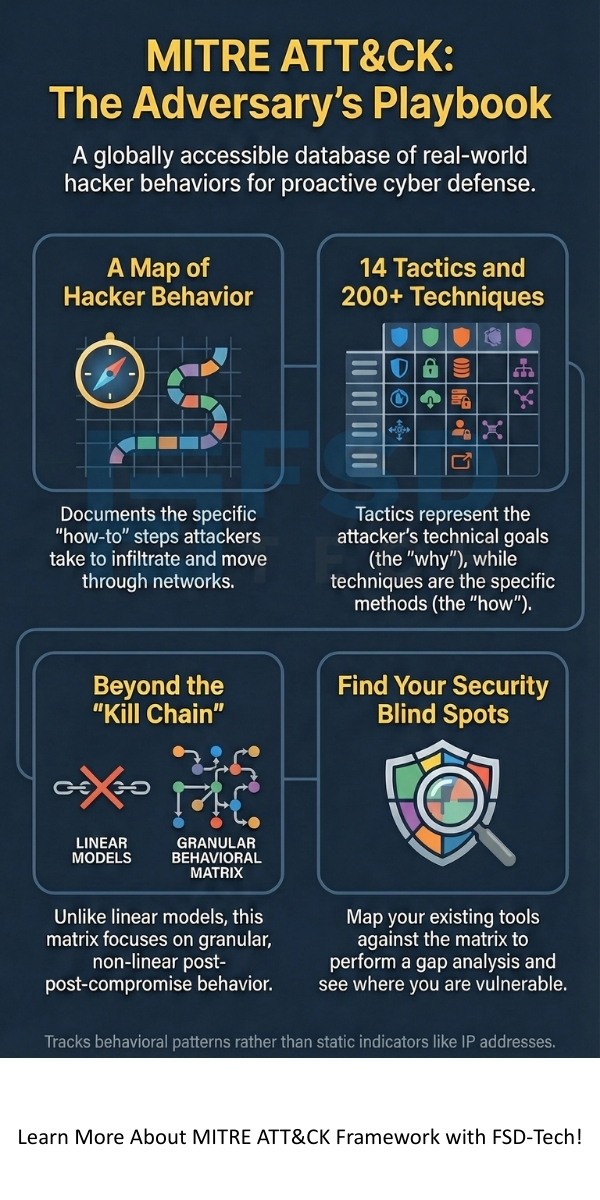
The MITRE Corporation started this project in 2013. They wanted a better way to describe how attackers behave. They realized that tracking file names or IP addresses was not enough. Hackers change those daily. However, hackers rarely change their core habits. This led to the creation of a system that tracks "behavioral patterns" rather than just static indicators.
Many people ask about the difference between the Cyber Kill Chain and MITRE ATT&CK framework. While both help you understand attacks, they serve different purposes. The Kill Chain is a linear model, while ATT&CK is a deep matrix.
| Basis for Comparison | Lockheed Martin Cyber Kill Chain | MITRE ATT&CK Framework |
|---|---|---|
| Structure | Linear, step-by-step model. | Multidimensional matrix. |
| Focus | High-level stages of an attack. | Granular techniques and behaviors. |
| Visibility | Focuses on perimeter defense. | Focuses on post-compromise behavior. |
| Flexibility | Fixed 7-step process. | Non-linear; tactics can happen in any order. |
| Goal | To stop an attack at the start. | To detect and describe every move. |
The MITRE ATT&CK framework helps organizations move from a reactive state to a proactive state. Most security teams wait for an alarm to go off. By using this framework, you can search for gaps before an attacker finds them.
MITRE ATT&CK framework facilitates several key security functions:
Also Read: What is Container Security? Best Practices, Tools, and Risks
The framework is constantly growing. Because hackers find new ways to work, MITRE updates the list regularly. As of the latest 2024 updates, the numbers are quite large.
For the Enterprise matrix, there are 14 tactics. Under these tactics, there are over 200 techniques and nearly 400 sub-techniques.
In the context of the matrix, a "block" refers to a specific technique cell. Each cell contains a description, examples of hackers who use it, and ways to stop it.
There are exactly 14 tactics in the Enterprise version. These tactics represent the "why" behind an action. For example, a tactic might be "Initial Access." The technique would be "Phishing." The tactic is the goal, and the technique is the method.
While the framework is not a "stage-based" linear model like the Kill Chain, it does follow a logical flow of an attack. How many stages are involved in the MITRE ATT&CK framework is often answered by looking at the 14 tactics. These tactics represent the technical goals an attacker must achieve.
1. Reconnaissance
The attacker is gathering information. They look at email addresses, server types, and employee LinkedIn profiles.
2. Resource Development
The attacker sets up their tools. This includes buying domains, creating fake accounts, or renting virtual private servers.
3. Initial Access
The MITRE ATT&CK framework defines this as the moment the attacker gets their foot in the door. This often happens through phishing or exploiting a weak website.
4. Execution
The attacker runs malicious code on your system. They might use a script or a command-line tool to start their work.
5. Persistence
Attackers want to stay in your system even if you restart your computer. They change settings so their software starts automatically.
6. Privilege Escalation
The attacker enters as a normal user but wants to become an "Admin." They look for bugs that give them more power.
7. Defense Evasion
The MITRE ATT&CK framework describes how hackers hide. They might turn off antivirus software or delete logs that show they were there.
8. Credential Access
The attacker steals usernames and passwords. They might look in the computer's memory or use "keyloggers" to watch what you type.
9. Discovery
The attacker looks around your network. They want to find where the sensitive data lives.
10. Lateral Movement
The MITRE ATT&CK framework uses this term for moving from one computer to another. Once they are inside, they hop across the network to find the "Crown Jewels."
11. Collection
The attacker gathers the data they want to steal. This could be credit card numbers, secret blueprints, or emails.
12. Command and Control
The attacker communicates with the hacked computer from a remote location. They send orders to the system to perform tasks.
13. Exfiltration
The data is sent out of your network to the attacker's server. They often compress or encrypt the data to hide the transfer.
14. Impact
The MITRE ATT&CK framework ends with the final goal. This could be destroying data, locking files for ransom, or just making your website crash.
Also Read: What Is a Zombie Computer? Botnet Threats Guide
The MITRE ATT&CK framework is deep. Each of the 14 tactics has many techniques. A technique is a specific way to achieve a goal.
For example, under the Initial Access tactic, you will find a technique called Phishing. But phishing can happen in many ways. This is where sub-techniques come in.
This level of detail helps security teams know exactly what to look for. If you only look for "phishing," you might miss a hacker using LinkedIn messages instead of email.
Using the MITRE ATT&CK framework is a journey. You do not have to master all 200+ techniques on day one. Most companies start small.
Step 1: Identify Your Risks
Which hackers are likely to target you? If you are a bank, you look at groups that steal money. If you are a hospital, you look at groups that use ransomware.
Step 2: Map Your Defenses
The MITRE ATT&CK framework allows you to see what your current tools can detect. You might find that you are great at seeing "Initial Access" but terrible at seeing "Lateral Movement."
Step 3: Prioritize Gaps
You cannot fix everything at once. Use the matrix to find the biggest holes in your wall. Focus on the techniques that are most common in your industry.
Step 4: Automate Detection
Many modern security tools, like EDR (Endpoint Detection and Response), come with the MITRE ATT&CK framework built-in. These tools automatically tag alerts with the correct technique name.
The MITRE ATT&CK framework has changed the world of cybersecurity. It moves us away from guessing and toward a data-driven approach. By understanding the moves of the adversary, you take away their greatest advantage: the element of surprise.
Our company believes that every business deserves a strong defense. We focus on putting the client first by using world-class tools like the MITRE ATT&CK framework. We don't just give you alerts; we give you clarity. Your security is our mission. Let us help you map your journey to a safer digital future.
Don't let hackers stay one step ahead. Contact our experts to map your defenses against the latest MITRE techniques.
What is the main goal of the MITRE ATT&CK framework?
The main goal is to provide a common language for security professionals. It helps everyone understand how attackers behave so they can build better defenses.
Is the MITRE ATT&CK framework free?
Yes. The MITRE ATT&CK framework is a free, open-source tool provided by the MITRE Corporation. Anyone can access it online.
How often is the matrix updated?
MITRE usually releases major updates twice a year. These updates include new tactics, techniques, and information about new hacker groups.
Can small businesses use this framework?
Absolutely. While it looks complex, small businesses can use it to understand basic risks. Even knowing the "Initial Access" techniques can help a small business prevent most attacks.
What is the difference between ATT&CK and D3FEND?
While ATT&CK focuses on what the attacker does, MITRE D3FEND focuses on what the defender should do. They are two sides of the same coin.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts