
Inside Cato’s SASE Architecture: A Blueprint for Modern Security
🕓 January 26, 2025

Many businesses face constant threats from cyber attacks. Among the most dangerous attacks, you find a specific type of phishing called a whaling attack. This attack is highly focused. It aims at top-level executives like the CEO, CFO, or other senior managers. Cyber criminals know that these high-level targets, sometimes referred to as whales, hold the keys to the company’s deepest secrets and largest bank accounts.
Whaling attacks refer to a type of cyber fraud. Whaling essentially means launching a highly customized phishing scam against a very specific, high-value target in a company. The goal is simple: trick the executive into sending money or giving up vital, confidential data.
In this detailed content, we will understand how whaling attacks work. We will also look at the different methods attackers use. Finally, we will show you what you can do to protect your business from this major threat.
Let us now discuss the basic definition and how it differs from other attacks.
A whaling attack is defined as a highly-targeted phishing scam. It is specifically aimed at senior executives or high-profile individuals within a business.
A whaling attack is nothing but a large-scale version of phishing. However, this attack is much more personalized and much more dangerous. The criminals involved in whaling spend a lot of time gathering information. They need this information to make their emails look absolutely real.
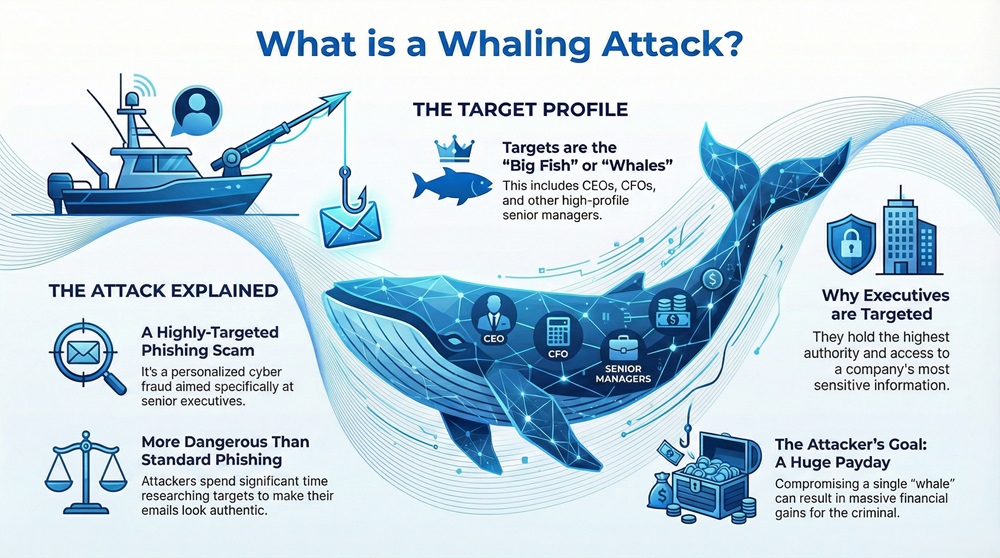
This attack is called a whaling attack because the targets are the "big fish" in the company. These targets, the senior executives, are called whales in this context. Whales hold the highest authority and access to the company's most sensitive information. Landing a single whale can mean huge financial gains for the attacker. This is why attackers put in so much effort.
It is essential to understand how whaling attacks differ from other common email scams. This helps you to build better security.
| Attack Type | Target Scope | Personalization Level | Goal |
|---|---|---|---|
| Phishing | Broad group of people (many users) | Low (generic message) | Steal general credentials or personal data |
| Spear Phishing | Specific person or group (small number) | Moderate to High | Steal credentials, access internal systems |
| Whaling Attack | Senior Executives (one or very few people) | Extremely High (looks totally authentic) | Steal huge sums of money or highly sensitive corporate secrets |
Whaling attacks are a specialized form of spear phishing. Simply put, whaling is spear phishing aimed only at the very top of the organization.
Spear phishing often targets an IT manager or a finance clerk. Whaling attacks, on the other hand, target the CEO or the CFO. These top executives can approve a major wire transfer with just one email.
The high level of detail in a whaling attack makes it highly sensitive. It makes it quite difficult for a busy executive to spot the fake nature of the email.
Now, talking about how these sophisticated attacks actually work.
Also Read: Spear Phishing: Learn About #1 CEO fraud
To understand a whaling attack better, let's look at the steps the attacker follows. The process is very methodical and involves major research.
Step 1: Target Selection and Research
A whaling attack always begins with careful target selection. Attackers identify the CEO, CFO, COO, or another highly influential senior manager.
Then, they begin to gather data. This data is highly specific and publicly available. They use social media, company websites, press releases, and SEC filings.
What information do they look for?
This extensive research helps the criminal build an authentic profile. This profile is essential for the next step.
Step 2: Crafting the Whaling Email
The whaling email is usually a masterpiece of deceit. It must look absolutely real to work. Attackers use the information they found to craft a message that creates a sense of urgency and high importance.
This email usually contains several major elements:
For example, a whaling attack email might have the subject line: "URGENT: Confidential Legal Subpoena - Action Required by CFO." The email will look like it comes from the company's main law firm.
Step 3: The Payload and Execution
Once the executive trusts the email, the attacker moves to the final stage. The whaling attack payload is not always a link to steal a password. The payload is often a direct action request.
The executive is asked to do one of two things:
In both cases, the attacker relies on the executive's high-pressure environment and the email's seeming authority. The success of the whaling attack depends majorly on social engineering.
Let us now understand the major signs that indicate a whaling attack.
You need to know the signs to avoid falling for a whaling attack. Whaling emails are often quite difficult to spot, but they usually contain several subtle clues.
1. Focus on Highly Sensitive Topics
A whaling attack email will not talk about basic things. It will always refer to a highly sensitive issue that only a senior executive would handle.
Any email with a highly sensitive or urgent financial subject should raise an immediate red flag.
2. Immediate and Secrecy-Based Requests
The attacker uses the request for secrecy to prevent verification. The email will often contain phrases like: "Do not discuss this with anyone," or "This is strictly confidential."
The request for action is also immediate. The email insists you act now. This gives you no time to stop and think about the details. A legitimate and major business action will always involve a formal, multi-step process, not a quick email wire transfer.
3. The Sender's Email Address
Always check the sender's actual email address. This is a crucial point in detecting a whaling attack.
4. Unusual Wire Transfer Instructions
If the email requests a wire transfer, always look at the recipient's bank information. A whaling attack will send the funds to an unusual or foreign bank account. They will use a strange name for the payee. Legitimate transfers always go through established banking channels.
The request will often come from a highly-trusted name, such as the CEO or a legal counsel, thereby creating a strong sense of trust. However, the request itself is highly irregular. Hence, you must question the request, not the name on the email.
Moving to the major impact these attacks can have on businesses.
Also Read: Domain Spoofing Explained: How It Works & How to Stop It
A successful whaling attack can cause major damage to a company. The impact goes far beyond just the financial loss.
1. Huge Financial Loss
The primary and most immediate damage is the loss of a large amount of money. Since the targets are high-value executives, the requested transfer amounts are usually substantial. The attackers aim for amounts that require a single-person approval, often hundreds of thousands or even millions of dollars. Thus, the financial blow can be quite devastating.
2. Loss of Highly Sensitive Data
In some whaling attacks, the goal is to steal confidential information. This might include:
Loss of this data can lead to massive fines under data protection laws like GDPR. Consequently, the company faces legal trouble and major reputation damage.
3. Damage to Company Reputation
When a whaling attack is successful, it often becomes public knowledge. Customers, investors, and business partners may lose trust in the company's security. This loss of trust can be a long-term problem. Resultantly, the company's stock price may fall, and partnerships may be damaged.
4. Operational Disruptions
A successful whaling attack often requires a major security clean-up. This means the company's IT and legal teams must stop everything to investigate. This internal disruption costs time and money. It also takes the focus away from the company's core business.
Simply put, a successful whaling attack is a major event that can severely impact the future of a business.
Also Read: What is a Firewall as a Service (FWaaS)?
Protecting against a whaling attack requires a layered approach. It is essential to combine technology with human education.
1. Executive and Employee Training
Training is the most important defense against a whaling attack. Because these attacks rely on social engineering, the human element is the weak link.
2. Implement Strong Email Authentication
You can use technology to help verify email senders. This is a crucial defense against whaling attacks.
3. Establish a Formal Verification Process
Never allow a major financial transaction to be approved based on a single email. This is an essential rule against the financial success of a whaling attack.
4. Limit Public Information
Attackers use public information to craft their highly personalized emails. Therefore, your company should be somewhat careful about what it publishes.
By combining these simple but powerful steps, you significantly reduce the chance of a successful whaling attack.
You can see that a whaling attack is a dangerous, carefully planned threat. Ignoring this risk is not an option for any modern business.
At our core, we believe that your security is our mission. We focus on providing you with clear, practical, and effective defenses. We stand ready to help you train your team, secure your email systems, and build the simple processes that turn a risky situation into a secure operation.

A whaling attack is a major cyber threat. It is a highly targeted phishing scam aimed at the most senior people in your company, the whales.
We can say that strong security is not just about technology. It also majorly involves the human element.
Whaling attacks are much more focused. Phishing targets many people with a generic message to steal simple passwords. Whaling targets only a single, very senior executive with a highly customized email to steal large sums of money or highly sensitive corporate secrets.
No. While many whaling attacks ask for a wire transfer of money, they can also ask for highly sensitive documents. For example, the attacker might pretend to be a lawyer asking for all employee W-2 forms under a court order.
The executive is the perfect target because they have the authority to approve large wire transfers and access highly confidential data. They also often work under great pressure and are busy. This makes them more likely to make a quick decision without proper verification.
The most important thing is to verify the request using a different communication channel. If the email asks for a wire transfer, you must call the sender on a known, official phone number. Do not reply to the email to confirm.

Surbhi Suhane is an experienced digital marketing and content specialist with deep expertise in Getting Things Done (GTD) methodology and process automation. Adept at optimizing workflows and leveraging automation tools to enhance productivity and deliver impactful results in content creation and SEO optimization.
Share it with friends!
share your thoughts